For decades, industrial organizations have trusted the idea of the air-gapped system—a computer, controller, or network that is physically separated from the internet and therefore presumed secure. The logic was simple: if a system cannot be reached, it cannot be attacked.
But in today’s connected industrial environments, this assumption is dangerously outdated.
Modern OT systems rely on data exchanges, vendor support, engineering laptops, and maintenance workflows that create hidden connectivity—even when the underlying equipment was never designed to touch the internet. Add rapid IT/OT convergence, and the picture becomes clear:
Air-gapped systems are no longer inherently secure—and pretending they are creates some of the most serious blind spots in industrial cybersecurity.
This article breaks down why air gaps fail, how IT/OT convergence compounds the problem, and what organizations must do now to secure their operational technology environments.

What an Air Gap Used to Mean (and Why That No Longer Applies)
Originally, air-gapped environments were used in military, nuclear, and intelligence applications. These systems had:
- Strict physical isolation
- Highly controlled maintenance workflows
- Limited external dependencies
- Dedicated, specialized operators
In those contexts, true air gaps worked because everything surrounding them was tightly regulated.
Modern industrial environments are different.
Today’s factories, power plants, pipelines, water facilities, and logistics hubs rely on:
- Digital transformation projects
- Cloud-connected analytics
- Remote vendor troubleshooting
- ERP and MES data flows
- OT/IT integration
- Continuous maintenance and updates
Operational technology no longer exists in isolation—even when the PLC or HMI itself is not directly connected to the network.
And that’s the crux of the problem.
Why “Air-Gapped” Systems Are Not Truly Air-Gapped
Even in facilities that insist certain systems are isolated, real-world workflows introduce multiple connectivity vectors. These pathways are well-documented in CISA ICS advisories, DOE research, and major OT incident reports.
Below are the major ways attackers bypass air gaps today.
1. Removable Media: USB Drives, SD Cards, and Portable Engineering Tools
This is the most common and most dangerous air-gap bypass.
OT systems often require:
- SD cards for program logic
- USB drives for firmware updates
- Portable hard drives for backups
- File transfers between engineering stations and controllers
These devices move between:
- Office networks
- Vendor laptops
- Cloud download portals
- Multiple facilities
Attackers know this, which is why malware targeting OT environments frequently leverages removable media. Stuxnet is the most famous example, but dozens of OT-specific malware strains use the same method.
Reality:
If USB drives enter your OT environment, you do not have an air gap.

2. Maintenance Laptops: The Hidden Attack Surface
No component breaks the air-gap myth more consistently than the engineering workstation or maintenance laptop.
These devices often:
- Connect to both IT and OT networks
- Travel between multiple industrial sites
- Access vendor cloud systems
- Run full operating systems (Windows/Linux)
- Carry tools, firmware, and configuration files
They are also vulnerable to:
- Phishing
- Malware
- Misconfigurations
- Cross-contamination between sites
A technician plugging a compromised laptop into a PLC effectively creates a temporary bridge between OT and the outside world.
Fact:
Most documented OT intrusions start through compromised engineering workstations—not direct network connections.
3. Software, Firmware, and Vendor Update Packages
OT systems require periodic updates, even when deployed in “isolated” environments:
- Firmware patches
- PLC logic updates
- Vendor-supplied configuration files
- Offline installers and tools
These updates often originate from:
- Vendor cloud portals
- Email attachments
- Internal IT repositories
If the supply chain is compromised, the air-gapped system is compromised before the file ever enters the facility. This was the core dynamic behind major supply chain incidents like NotPetya and SolarWinds.
4. Temporary Network Connections and Remote Support
Even facilities that claim to be air-gapped frequently allow exceptions:
- A 4G modem temporarily plugged in for vendor support
- A laptop bridging IT and OT for a one-time data transfer
- A direct connection to an IT workstation for diagnostics
Temporary connections are rarely logged, rarely monitored, and often forgotten.
But attackers only need one moment of connectivity.
5. Expanding OT Perimeters Through IT/OT Convergence
Modern OT environments include:
- IIoT devices
- Smart sensors
- Wireless gateways
- Cloud-connected HMIs
- Predictive maintenance tools
- MES/ERP integrations
These are not inherently “internet-connected,” but they rely on data moving through IT systems.
If data moves, risk moves with it.
The Bigger Issue: Air-Gap Thinking Doesn’t Fit an IT/OT Converged World
The most important shift in industrial cybersecurity is not new malware, not geopolitical threat actors, and not cloud adoption.
It is convergence—the merging of IT and OT systems into unified digital ecosystems.
This trend is accelerating because:
- Operations need real-time insights
- Facilities depend on remote expertise
- Efficiency improvements rely on data
- Modern supply chains require integration
- OT vendors increasingly use cloud-enabled tools
Because of this convergence, even “isolated” OT systems depend on IT infrastructure for:
- Identity and access management
- File distribution
- Engineering tools
- Virtual machines
- Time synchronization
- Patch repositories
The old assumption—“OT is isolated, so OT is safe”—no longer matches how industrial environments actually function.
The Risks Created by the Air-Gap Myth
Relying on air gaps when those air gaps don’t truly exist creates significant security failures.
Below are the most common.
Risk 1: Lack of Monitoring and Telemetry
If teams believe a system is offline, they often avoid deploying monitoring tools, sensors, or logging.
This results in:
- Zero visibility into suspicious behavior
- Missed changes to logic or firmware
- No detection of unauthorized access
- No forensic evidence after an incident
Attackers often exploit unmonitored environments specifically because they know activity will go unnoticed.
Risk 2: Undefined Ownership and Responsibilities
Air-gapped systems frequently fall into organizational grey areas:
- IT assumes OT manages them.
- OT assumes IT secures them.
- Vendors assume customers own maintenance workflows.
When no one is responsible, nothing is secured.
Risk 3: Misleading Risk Assessments
Air-gapped systems are often excluded from:
- Penetration testing
- Patch management programs
- Vulnerability scanning
This creates a false sense of safety, which increases exposure.
Risk 4: Overreliance on Physical Security
While physical access controls matter, they do not prevent:
- Infected removable media
- Compromised engineering laptops
- Rogue insider activity
- Malware introduced through supply chains
A locked room cannot stop a compromised file.
A Modern Approach: What Replaces the Air-Gap Model
Air gaps are not dead—but the belief that they guarantee security must die.
The future of OT security is converged, visibility-driven, and workflow-focused.
1. Assume Connectivity Even When None Is Documented
This mindset aligns with NIST SP 800-82 guidance.
Treat every OT system as if it could be reached indirectly.
This encourages:
- Continuous monitoring
- File integrity protection
- Logging of engineering activity
- Regular analysis of controller behavior
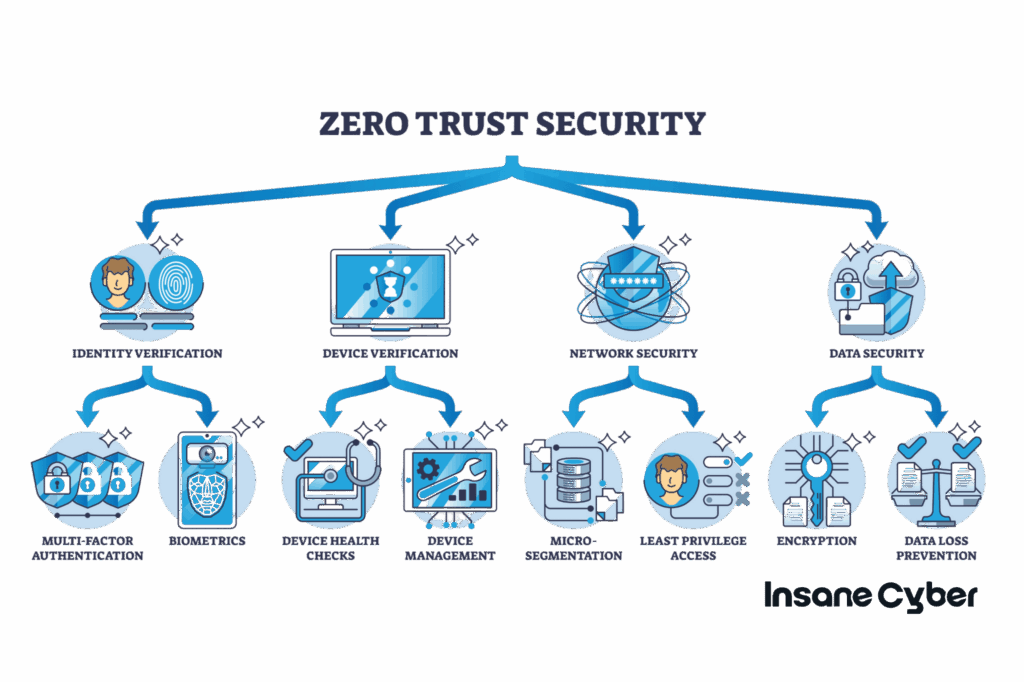
2. Implement Zero-Trust Principles for OT
Zero trust does not break industrial systems.
When done right, it strengthens reliability.
Key steps include:
- Strong identity verification
- Least-privilege access
- Verification of all engineering actions
- Validation of firmware and configuration changes
- Monitoring of removable media usage
This ensures the pathways that bypass air gaps cannot be abused.
3. Secure the Maintenance and Engineering Ecosystem
This is one of the highest-impact changes any organization can make.
Controls should include:
- Hardened engineering workstations
- Isolated contractor access environments
- Logging of all PLC and HMI changes
- Scanning of all offline update files
- Controlled workflows for vendor access
If maintenance workflows are secure, the OT environment is exponentially safer.
4. Extend Visibility Into OT Systems (Even Offline Ones)
Visibility is the foundation of modern ICS security.
This includes:
- Controller state monitoring
- Logic change detection
- Firmware integrity checks
- Alerting on unauthorized modifications
- Behavioral baselines for key devices
Air-gapped or not, OT assets must be visible.
5. Align IT and OT Security Programs
IT and OT teams bring complementary strengths.
IT contributes:
- Identity management
- Governance
- Network visibility
- Threat intelligence
OT contributes:
- Safety requirements
- Process understanding
- Operational constraints
- System lifecycle expertise
Together, they create a unified security program that matches real-world operational needs.
Conclusion: The Air Gap Isn’t Dead But, Its Assumptions Are
Air-gapped systems still matter, but they cannot be relied upon as a standalone security strategy. The realities of maintenance, supply chain, removable media, and IT/OT convergence mean that “offline” systems are rarely offline in practice.
The right way forward is clear:
- Assume connectivity.
- Verify every file, action, and access path.
- Secure engineering workflows.
- Monitor logic, firmware, and controller states.
- Unify IT and OT security programs.
In a converged world, safety and reliability depend on visibility, verification, and modern security controls—not on assumptions about isolation.
Air gaps used to work.
Today, they create blind spots.
It’s time to replace the myth with a strategy fit for modern industrial operations.
How Valkyrie Closes the Air-Gap Security Gap
As industrial environments become more interconnected, organizations need a way to continuously verify the integrity of their controllers, PLCs, HMIs, robots, safety systems, and all the device-level assets that keep operations running. Traditional monitoring tools don’t reach deep enough into the OT stack, and manual validation simply cannot keep pace with the realities of modern cyber-physical systems.
This is where Valkyrie changes the game.
Valkyrie provides automated, device-level visibility across OT environments—regardless of whether systems are online, offline, or “air gapped.” Instead of relying on network traffic alone, Valkyrie collects ground truth from the devices themselves:
- Logic and program changes
- Firmware and configuration integrity
- Unauthorized modifications
- Anomalous controller behavior
- Engineering workstation activity
- File and update pathways
- Device state baselines and deviations
By continuously monitoring this data, Valkyrie eliminates the blind spots that make air-gapped assumptions so dangerous. Even if a system never touches the internet, Valkyrie ensures you still know exactly what is happening inside it.
No guessing. No assumptions. Real visibility.
In a converged IT/OT world, this level of assurance is no longer optional—it’s essential for safety, uptime, and resilience. Valkyrie gives industrial organizations the confidence that their most critical assets are protected, validated, and monitored at all times.