Find the Threats Your Monitoring Tools Won't Surface
Visibility beyond alerts, because attackers don’t announce themselves.
Threats to industrial environments continue to evolve and evade basic monitoring tools, because they’ve moved beyond infiltrating your network traffic.
You need a way to see what’s happening below the surface, before an attacker makes their move. That’s where we come in.
Your risk story
Monitoring provides a good baseline, but creates a false sense of security. Finds surface level activity and known risks. Will miss deeper living off the land signatures.
There's an easy fix
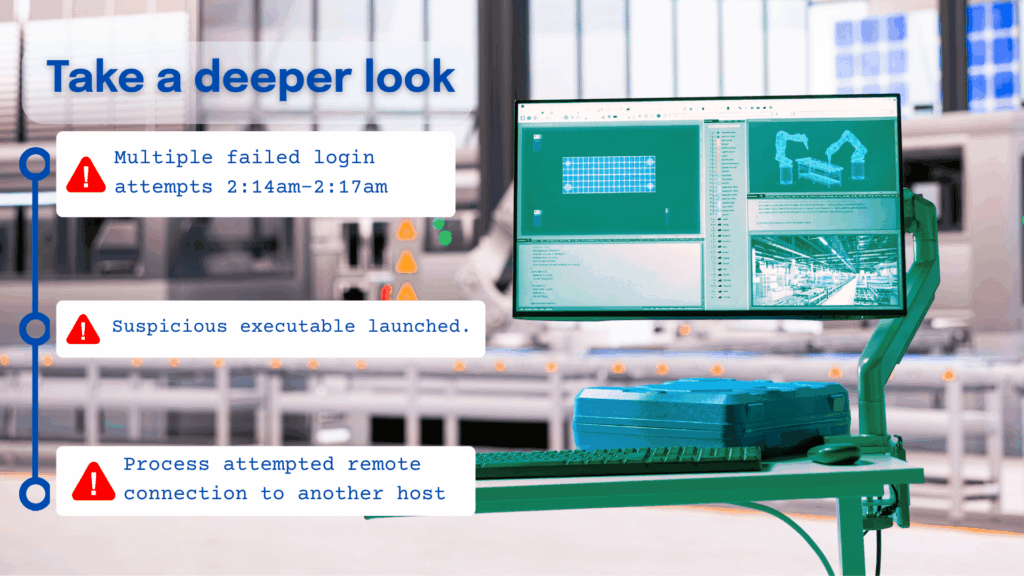
Threat hunting helps you to actively close the gaps that attackers rely on, finding weak spots before they can be exploited. Rapidly analyze network and endpoint data to proactively find threats.
How it works
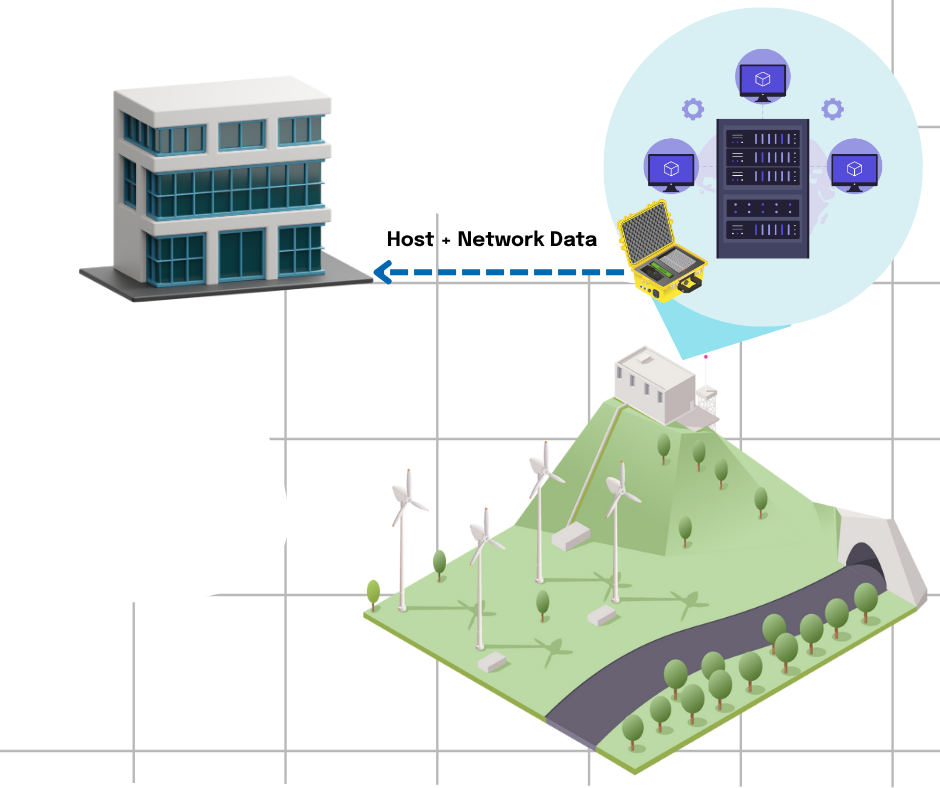
- Ingests batch and streaming data sources for correlation and analysis
- Network data adds OT/ICS protocols and depth that passive and community tools don’t
- Host data, like Windows event logs, registry hives, other device data, helps with finding living on the land threats like Volt Typhoon
- Rapid analysis for deep insights
- Dashboards reveal intel like threats, protocol communications, assets, and more
- Flexible deployment via on-premise, in-cloud or Cygnet Flyaway Kit
- Flexible deployments allow for high scalability in hard-to-reach areas, currently unmonitored areas
- Tactical for anytime, anywhere analysis

Ready to put your defenses to the test?
See how Insane Cyber transforms security
Our products are designed to work with
you and keep your network protected.



