Securing Your Industrial Core: Getting the Most from OT Vulnerability Assessments
In today’s interconnected industrial landscape, the security of your Operational Technology (OT) is paramount. An OT vulnerability assessment serves as a cornerstone of a robust defense strategy, offering a deep dive into your systems to uncover weaknesses before they can be exploited.
It’s more than just a scan; it’s a comprehensive evaluation designed to identify potential vulnerabilities, misconfigurations, and hidden attack paths within your critical OT networks and systems. By understanding these risks, you can take proactive steps to fortify your industrial environment.
The Real Value: More Than Just Security
While bolstering your defenses is the primary goal, OT vulnerability assessments offer benefits that extend into compliance and financial protection.
Organizations often use these assessments to demonstrate due diligence for regulatory frameworks like NERC CIP, IEC 62443, or various NIST guidelines. Systematically identifying and documenting potential risks provides clear evidence to auditors and regulatory bodies of a proactive approach to security.
Furthermore, the cyber insurance landscape is evolving. Many providers now look for proof that companies are regularly assessing and managing vulnerabilities in their OT environments.
Conducting thorough vulnerability assessments can streamline the process of securing or renewing essential cyber insurance policies, ensuring you meet insurer expectations for risk reduction.

Peeling Back the Layers: What an OT Assessment Investigates
A critical part of a robust OT vulnerability assessment is configuration analysis. This isn’t just a surface-level check; it involves meticulously evaluating the settings and parameters of your hardware, software, and network components.
The aim is to ensure these configurations align with industry best practices, relevant security standards, and your own organization’s policies. By carefully reviewing device configurations—such as firewall rules, switch settings, and network segmentation—assessors can pinpoint hidden weaknesses.
Common issues uncovered during configuration analysis include overly permissive firewall rules, unrestricted or unmanaged services, exposed protocols or interfaces, and deviations from established management best practices.
Identifying these misconfigurations early allows you to address them before they develop into significant vulnerabilities, adding a crucial layer of assurance to your OT security posture.
The scope of an assessment can be tailored, ranging from a specific subset of systems to the entire industrial environment. While vulnerabilities aren’t actively exploited during these assessments, they are validated with a keen focus on uncovering as many potential attack paths as possible.
Inside the Assessment: Key Areas of Focus
A comprehensive OT vulnerability assessment is multifaceted, examining various aspects of your industrial control systems (ICS). While the specifics can be adjusted to your needs, key areas typically include:
Understanding Your Control System Landscape: The assessment begins by reviewing the overall control system architecture. This encompasses physical process control devices, supervisory control systems (like SCADA), engineering and support systems, how these systems interface with business networks, and the underlying compute and storage infrastructure.
Mapping the Network: Closely related is the network topology review. This phase examines the networks that support your industrial control systems, looking at network structure, configurations, traffic flows, monitoring capabilities, firewall rules, and access control lists.
Network Reconnaissance (Enumeration): Assessors conduct a targeted analysis of in-scope subnets and assets using a combination of passive and active network tools. The outputs from these tools, alongside existing configurations, are examined to identify network-accessible vulnerabilities.
In OT environments, a careful, methodical approach is paramount to avoid any disruption. Network enumeration should only begin after proper authorization and with full coordination with relevant stakeholders.
This collaborative planning prevents unexpected impacts on operational processes. The emphasis is often on non-intrusive methods like passive network sniffing and DNS analysis to gather insights without generating excessive network traffic.
When active techniques are necessary, they are used judiciously, with constant monitoring and fallback plans. Common findings here can include devices with default credentials, systems attempting unauthorized internet communication, use of insecure protocols, or unnecessary open ports.
Host-Level Scrutiny: The assessment delves into host configurations, using both native and introduced tools to detect vulnerabilities based on host type, operating system, installed software, and patch levels.
For highly critical systems where executing new processes is risky, manual analysis is performed. This is particularly vital as Windows-based workstations and servers often form the backbone of OT operations.
Reviewing local administrator account management, inspecting running services, identifying unpatched systems, and assessing endpoint security configurations are all part of this stage.
Industrial Device Specifics: Control devices themselves and their configurations are assessed to identify vulnerabilities and potentially exploitable functionalities.
If feasible, a non-production test device might be used for a deeper, more hands-on analysis without risking the live environment.
Active Directory Integrity: Given its central role, the Active Directory (AD) infrastructure is analyzed to uncover vulnerabilities in authentication protocols, Domain Naming Services (DNS), Group Policy configurations, and Certificate Authority (CA) services. This helps identify potential attack paths by examining user accounts, group memberships, system configurations, and trust relationships.
Issues like excessive privileges, accounts vulnerable to common AD attacks (e.g., Kerberoasting), or misconfigured service principals are often brought to light.

Spotting the Unseen: Common Vulnerabilities Unique to OT
Standard IT vulnerability assessments often miss weaknesses specific to industrial settings. For instance, many OT systems still rely on legacy protocols like Modbus, DNP3, and PROFINET, which may lack robust encryption and authentication, creating communication weaknesses.
Another common issue is hardcoded credentials or default passwords on devices from major vendors, which, if unchanged, offer an easy entry point for attackers.
Unsupported and end-of-life devices are also prevalent in industrial facilities, with critical equipment often running outdated firmware or operating systems like Windows XP due to production constraints or vendor support limitations. Improper network segmentation between business and control systems can allow threats to move laterally, especially through poorly configured VLANs or VPNs.
Furthermore, engineering workstations used for programming devices might lack adequate endpoint protection or monitoring, creating silent footholds. Sometimes, residual test configurations, like diagnostic interfaces or remote access services left by vendors, can create uncataloged backdoors.
Overprivileged service accounts or operator credentials, and misconfigured firewall rules or Group Policy settings in Active Directory, also represent significant risks often overlooked without specialized OT focus.
Timing is Everything: How Often to Assess Your OT Environment
Determining the ideal frequency for OT vulnerability assessments depends on several factors unique to your organization. As a general guideline, annual assessments serve as a solid baseline for most organizations. This helps in catching emerging threats and addressing vulnerabilities that develop over time.
However, if your environment is highly dynamic, supports mission-critical operations (like utilities, energy, or manufacturing where uptime and safety are paramount), or faces stringent compliance requirements, consider increasing the cadence to semi-annually or even quarterly.
It’s also highly recommended to conduct an assessment after any major system changes. This includes infrastructure upgrades, network expansions, the integration of new operational processes, or even significant business events like mergers and acquisitions, which can introduce new risks.
Always consider industry regulations (such as NERC CIP or IEC 62443) or best practices from bodies like ISACA or the SANS Institute, which may suggest specific assessment intervals. Ultimately, aligning assessment frequency with your organization’s operational risk appetite and compliance obligations is key.
Onsite or Remote? Choosing the Right Assessment Approach
A common question is whether OT vulnerability assessments are better performed onsite or remotely. For many assessments, remote execution is often preferred. Secure connectivity options and specialized tools allow for thorough evaluations to be completed efficiently, with minimal setup and cost, and without disrupting daily operations.
However, in specific situations—such as for highly segmented, air-gapped, or particularly intricate industrial networks—an onsite visit may be necessary. Onsite assessments allow for direct interaction with hardware or networks that aren’t remotely accessible, providing deeper insights where required. The best approach is always tailored to your industrial context, aiming for maximum insight with minimal operational impact.
The Outcome: Understanding Your Assessment Deliverables
The primary deliverable from an OT vulnerability assessment is a comprehensive report. This document typically details identified vulnerabilities and potential attack paths, provides risk prioritization, and includes an impact analysis. It should also contain supporting materials for technical teams, operations personnel, and leadership, alongside customized remediation recommendations tailored to your specific environment.
Effective recommendations consider the unique challenges of implementing changes in industrial settings, often providing both short-term and long-term strategies that address people, processes, and technology.
Beyond a static report, active collaboration is key. Throughout the assessment, assessors should engage with your engineering, operations, and security teams. As vulnerabilities are identified, discussing their impact, exploring remediation strategies, and sharing industry best practices ensures your team gains valuable insights and practical solutions.
After the Fix: What Comes Next?
Once you’ve implemented the remediation measures identified in your OT vulnerability assessment, the journey isn’t over. The next crucial phase is to validate the effectiveness of those controls.
This is typically achieved through a focused penetration test tailored to your environment. This step verifies that previously discovered vulnerabilities have been addressed and helps identify any new gaps that might have emerged during remediation. You should expect a follow-up report detailing these penetration test results.
Cybersecurity in industrial environments is a continuous process, not a one-time fix. To maintain and strengthen your security posture, it’s essential to schedule regular vulnerability assessments and penetration tests, stay diligent with system updates and patch management, and incorporate evolving industry best practices from sources like NIST and ISA/IEC 62443.
Planning regular security check-ups will help you keep pace with the ever-changing threat landscape.
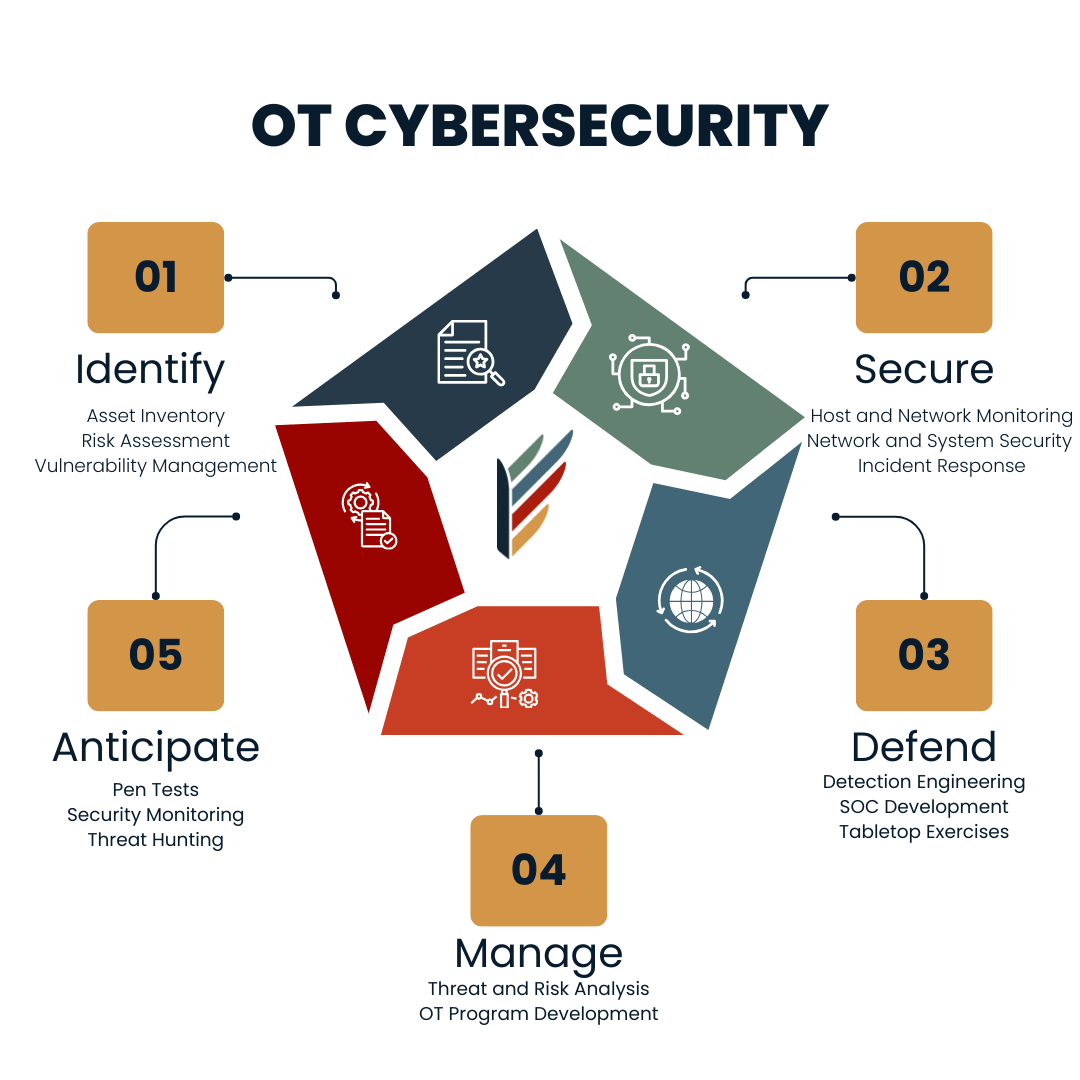
Getting the Most from Your OT Vulnerability Assessment
To truly maximize the benefits of an OT vulnerability assessment, a collaborative and well-planned approach is essential. Engage your operations and engineering teams early in the process to ensure their buy-in and facilitate smooth cooperation.
Clearly define the goals, desired outcomes, and scope of the assessment to align everyone’s expectations.
It’s also vital to establish clear rules of engagement and safe work practices to maintain operational integrity throughout the assessment. Open communication channels, where all activities can be quickly discussed and approved before execution, are crucial.
Finally, ensure that key stakeholders from operations, engineering, IT, security, and leadership are available and involved to enable effective information sharing and decision-making.
By adopting these practices and leveraging a structured assessment methodology, organizations can significantly strengthen their OT security posture and reduce cyber risk in their critical industrial environments. If you’re looking to enhance the security of your operational technology, seeking expert advice on tailored vulnerability assessments is a prudent step forward.
Contact Insane Cyber today to learn more about how our OT vulnerability assessments can help secure your critical infrastructure!