Supervisory Control and Data Acquisition (SCADA) systems are the unsung heroes of our modern world. They quietly manage critical infrastructure – from power grids and water treatment plants to manufacturing lines and transportation networks.
But this critical role also makes them a prime target for cyberattacks. As these systems become increasingly interconnected, robust cyber monitoring isn’t just advisable; it’s essential.
Let’s dive into the tools, techniques, and evolving threat trends that security professionals need to navigate to keep these vital systems secure.
The Three Core Layers of Modern ICS Architecture
So, how is a modern Industrial Control System (ICS) put together? Think of it as a well-organized team with three main layers, each playing a unique role in keeping critical infrastructure running smoothly:
- Field Layer: This is where the action happens—sensors, actuators, and input/output devices interact directly with the physical processes on the plant floor.
- Supervisory Layer: Sitting in the middle, this layer includes the SCADA servers and Human-Machine Interfaces (HMIs) that engineers and operators use to monitor and control equipment.
- Enterprise Management Layer: At the top, you’ll find the IT systems that connect the plant to the broader business network, enabling data analytics, reporting, and strategic decision-making.
Each layer brings essential capabilities to the table, but the growing interconnectedness between them also introduces new cybersecurity challenges.
Recent Trends and Key Breakthroughs in Industrial Automation
Industrial automation has come a long way from basic programmable logic controllers managing a handful of machines. Today’s landscape is shaped by several sweeping innovations and pressing focus areas:
- Industrial Internet of Things (IIoT): More devices than ever are networked, collecting real-time data and enabling predictive maintenance across sprawling facilities—from Siemens turbines to Rockwell PLCs.
- Smart Sensors and Edge Computing: Decentralized processing at the “edge” of the network lets plants analyze data right where it’s generated, minimizing latency and spotting issues before they balloon.
- Artificial Intelligence and Machine Learning: This is more than a buzzword. Algorithms now help optimize everything from quality control on assembly lines to energy efficiency at wastewater plants.
- Enhanced Industrial Cybersecurity: As more systems connect to the outside world, cybersecurity solutions tailored for OT environments (think Dragos and Claroty) are seeing rapid adoption.
- Interoperability and Open Standards: Open communication protocols and universal platforms are transforming how automation systems from traditionally siloed vendors work together.
These trends are collectively pushing industrial automation toward smarter, safer, and more autonomous operations. The key takeaway? The sector is evolving at record pace, with both opportunity and risk accelerating in tandem.
The Rising Tide: Why SCADA Systems Are in the Crosshairs
Historically, SCADA systems were often isolated, relying on “security through obscurity.” However, the drive for efficiency, remote access, and data integration with enterprise networks has brought them online, exposing them to a new world of cyber threats.
SCADA vs. IT: Contrasting Performance and Availability Priorities
When it comes to performance and availability, SCADA systems play by entirely different rules than traditional IT setups.
For starters, SCADA networks demand near-instantaneous responses—delays or “jitter” of even a second can disrupt processes controlling everything from pumping stations to assembly lines. These systems are built for real-time operation, often requiring end-to-end latency below one second. Scheduled downtime? Not so fast. SCADA environments are expected to run around the clock, with maintenance windows often planned weeks (or even months) ahead to avoid any unexpected interruptions.
To ensure this relentless availability, redundancy isn’t optional—it’s the norm. Failover systems, backup generators, parallel controllers: all are standard SCADA fare to minimize the chance of outages. In contrast, typical IT systems, while certainly valuing uptime, may tolerate more flexible availability requirements. Back-office servers can handle brief reboots or routine maintenance, and some IT processes can be delayed without significant consequences.
This sharp contrast highlights why classic IT security playbooks can fall short in SCADA environments. The relentless demand for uptime and precision means cybersecurity solutions must be tailored—keeping vital infrastructure humming no matter what digital storm comes its way.
IoT Integration: Unlocking New Advantages for SCADA
So, what happens when you plug the Internet of Things (IoT) into SCADA’s tried-and-true machinery? You move from isolated, stand-alone systems to networks that are more connected—and more capable—than ever before.
Here’s what IoT brings to the control room table:
- Greater Flexibility: With IoT devices, SCADA systems can adapt quickly to changing conditions, scaling up or down as operations demand—think modular, not monolithic.
- Remote Access & Availability: Engineers no longer need to be chained to the console room. IoT-powered SCADA enables monitoring and management from anywhere, at any time, whether it’s a corner office or a coffee shop.
- Real-Time Data & Big Data Analytics: Floodgates open for data. Sensors, meters, and devices now continuously feed detailed information, allowing for proactive analysis, faster troubleshooting, and smarter decision-making.
- Cost Efficiency: By automating monitoring, predictive maintenance, and incident detection, organizations can cut unnecessary site visits and reduce downtime—saving both time and money.
- Scalability: IoT makes it straightforward to add new devices or expand system reach without overhauling the core infrastructure—future-proofing your investment as needs evolve.
In short, integrating IoT transforms SCADA from a silent workhorse into a smart, agile command center—matching the pace of today’s always-on world.

IoT Meets SCADA: The Evolution Toward Cloud Integration
Today’s SCADA systems are no longer just a collection of isolated control panels tucked away in a secure room. Thanks to the rise of the Internet of Things (IoT), these systems have evolved—now connecting countless devices and sensors across power plants, factories, and far-flung pumping stations, all pulling data into centralized platforms.
So, what exactly is an IoT SCADA system? It’s essentially the fusion of traditional SCADA with IoT technologies and cloud computing. Instead of relying solely on dedicated, hardwired networks, modern SCADA setups tap into IoT devices that can transmit data over the internet and leverage cloud-based services—think Amazon Web Services or Microsoft Azure—for data storage, analytics, and management. This shift unlocks impressive benefits, like:
- Remote monitoring and control: Operators can access real-time system data from virtually anywhere.
- Improved scalability: Adding new sensors or capabilities is as simple as configuring a device and updating a dashboard.
- Enhanced analytics and big data processing: The cloud’s horsepower allows organizations to crunch vast volumes of operational data for insights and optimization.
- Greater cost-efficiency: Cloud services and IoT endpoints often reduce the need for heavy, up-front infrastructure investments.
However, this newfound openness comes with major security trade-offs. Once isolated and “air-gapped,” these connected environments now present a broader attack surface, making security a moving target for defenders. Integrating SCADA with IoT and the cloud can open the door to sophisticated cyber threats—especially if security hasn’t kept pace with functionality.
The potential impact of a compromised SCADA system is immense, ranging from operational disruption and financial loss to environmental damage and even threats to public safety. The potential impact of a compromised SCADA system is immense, ranging from operational disruption and financial loss to environmental damage and even threats to public safety.
Breaking Down Critical Assets and Business Impacts in Industry 4.0
So, what exactly counts as a “critical asset” in the brave new world of Industry 4.0? Think of these as the digital and physical components that keep smart factories, interconnected production lines, and sensor-laden operations humming along. They include everything from industrial control hardware (PLCs, RTUs, sensors), OT and IT networks, and the often-overlooked—but vital—software and data flows that link machinery to business systems.
When these assets are in the cyber crosshairs, the business risks expand well beyond simple downtime. Impacts can include:
- Operational Disruption: Production can grind to a halt, causing cascading delays across supply chains.
- Financial Consequences: Think direct revenue loss, compliance fines, or costs tied to system recovery and restoration.
- Reputation Damage: Breaches erode trust with customers, regulators, and partners.
- Safety and Environmental Risks: In sectors like energy or water, a cyberattack could endanger not just assets, but people and the environment too.
Understanding this classification isn’t just an academic exercise—it’s key to prioritizing your cybersecurity strategy and protecting what matters most.
The High Cost of Ignoring Input Validation in SCADA Software
Failing to properly neutralize—or sanitize—inputs in SCADA software can open the floodgates to a range of cyber threats. When user-provided or upstream data isn’t handled carefully, attackers can slip malicious instructions directly into the heart of your critical systems. Here’s how it happens, and why it matters:
Command & OS Injection: Attackers can send carefully crafted data that gets interpreted as system commands. If these commands aren’t filtered out, your SCADA server may unwittingly execute them—potentially giving attackers elevated privileges or the ability to run arbitrary code. This can go as far as giving outsiders control over equipment or processes, sometimes without leaving much of a trace.
Cross-Site Scripting (XSS): Modern SCADA interfaces often involve web-based dashboards. Weak input handling here lets an attacker inject malicious scripts, which might hijack operator sessions or expose sensitive data simply because someone opened the wrong link or page.
SQL Injection: If input data flows unchecked into backend databases, bad actors can tamper with SQL queries. The effects? Leakage of sensitive operational details, unauthorized modifications, or even full compromise of historical control data.
Broadened Attack Surface: Many SCADA components, like RTUs and PLCs, run specialized operating systems, making certain vulnerabilities even more critical. Unchecked inputs increase these components’ exposure, giving adversaries more opportunities to poke holes in your defenses.
In essence, neglecting robust input validation can transform what should be routine data exchange into the digital equivalent of handing over your master keys. Successful exploits can lead to remote code execution, sensitive data leakage, session hijacking, and in some cases, complete operational disruption.
Understanding the adversary is key. Attackers targeting SCADA systems can range from disgruntled insiders and opportunistic hackers to sophisticated nation-state actors and organized cybercriminal groups. Their motivations are equally varied, including espionage, sabotage, and financial extortion through ransomware.

A Brief (and Troubling) History of SCADA Cyber Incidents
SCADA systems have been in the cyber crosshairs for decades—with attackers continually evolving their methods. Some notorious incidents include:
1982: The Siberian Pipeline Explosion
Allegedly the first known SCADA cyber incident, a Trojan horse was injected to manipulate valves and pumps, pushing gas pressure beyond safe limits and causing a massive explosion.1994: The Salt River Project Breach
An attacker used a dial-up modem to access a critical infrastructure system, stealing and altering customer data and system logs.1999: Gazprom Compromise
A Trojan horse enabled an attacker to seize full control over the central switchboard of Russia’s largest gas company, threatening the safe flow of gas across pipelines.2000: Maroochy Shire Sewage Attack
In Australia, a rogue individual took control of 150 wastewater pumping stations using a radio transmitter, causing malfunctions simply by driving around and issuing commands.2003: SQL Slammer Worm
This fast-spreading worm exploited vulnerabilities in Microsoft SQL Server, jumping from enterprise IT to the SCADA network, and disabling a safety monitoring system for five hours.2010: Stuxnet
Arguably the most infamous SCADA-targeted malware, Stuxnet spread via infected USB drives and stealthily sabotaged Iran’s nuclear facility centrifuges.2011–2012: Duqu and Flame
These sophisticated malware strains focused on intelligence gathering—stealing technical diagrams and other sensitive information for future attacks.2015: Ukrainian Power Grid Attack
Hackers took down part of Ukraine’s power grid, leaving roughly 225,000 people without electricity—a stark demonstration of the real-world impact of SCADA breaches.
These incidents underscore not just the variety of attacker motives and techniques, but also the real-world consequences when SCADA security is breached. As attacks grow more sophisticated, understanding these historical lessons is crucial for defenders preparing for what’s next.
Hard Lessons: Notorious Attacks on SCADA & ICS
So, how real is the risk to SCADA and industrial control systems? Let’s take a look at some headline-making cyber incidents that serve as cautionary tales for critical infrastructure everywhere.
Stuxnet:
Arguably the poster child for SCADA-targeted malware, Stuxnet emerged in 2010 as a game-changer. This sophisticated worm was engineered to sabotage Iran’s nuclear facilities by manipulating industrial controls—causing physical equipment to self-destruct while operators were none the wiser. The real lesson? These kinds of attacks are not just theoretical; with patience and resources, attackers can cross the digital-physical divide.
Triton/Trisis:
Fast-forward to 2017, when the Triton malware shook the security world. Unlike traditional attacks that stop operations, Triton targeted safety instrumented systems at an energy facility, potentially putting lives at risk by attempting to disable safety mechanisms. This incident highlighted how attackers are willing to take bolder risks and that the stakes for compromised industrial controls can go well beyond downtime or dollars.
Shamoon and StoneDrill:
Ransomware and destructive malware have also made their presence felt in the industrial sector. Notably, attacks like Shamoon and StoneDrill wreaked havoc across energy organizations in the Middle East, wiping data and disrupting operations. The message is clear: disruption and destruction are both very much on the table for adversaries aiming to make headlines—or a point.
Key Takeaways:
- No organization or industry is immune; attackers target both proprietary controls and widely used platforms.
- Gaps between IT and OT defenses can be exploited for initial entry and lateral movement.
- It’s not just about stealing data—attackers are willing to disrupt, destroy, and endanger safety.
These cases illustrate why proactive monitoring, segmented architectures, and ongoing threat intelligence are table stakes for protecting SCADA systems.
Mapping the Threat: Taxonomies of SCADA Cyber Attacks
To make sense of the diverse and ever-evolving threats facing SCADA systems, security researchers have worked to categorize and classify attacks using taxonomies. These structured approaches help professionals understand where vulnerabilities lie and how attackers operate, ultimately informing better defenses.
Several notable taxonomies have emerged, each with a unique focus:
Vulnerability-Based Classifications: These taxonomies break down SCADA system weaknesses—whether in hardware, software, network configurations, or human processes—to highlight entry points for attackers. By grouping vulnerabilities, defenders can prioritize what to patch or monitor most closely.
Attack Vector and Motive Taxonomies: Some frameworks sort attacks by method (e.g., malware, exploitation of remote access, phishing) or by the attacker’s ultimate goal—such as espionage, sabotage, or extortion. This contextual approach helps organizations anticipate the “why” and “how” behind threats.
Domain-Specific Approaches: Research has also explored classifying attacks based on their impact across cyber-physical domains (the digital and physical worlds), including cross-domain attacks that pivot between corporate IT and operational technology environments.
Intrusion Detection Focus: With supervised machine learning gaining ground in intrusion detection, newer taxonomies organize threats according to how well they can be detected and distinguished by automated systems. This approach guides the development and tuning of smart monitoring tools for SCADA environments.
What’s the takeaway? No single taxonomy covers every nuance, but together they form a playbook that security teams can draw from—helping identify blind spots, optimize defenses, and respond effectively as the threat landscape shifts.
Stuxnet: Unmasking a Game-Changer in Industrial Cyber Warfare
One high-profile example that put SCADA vulnerabilities on the global stage is Stuxnet. When analysts like Ralph Langner began dissecting Stuxnet in 2010, it became clear this was no ordinary malware—Stuxnet was custom-built to disrupt physical operations at industrial facilities, specifically targeting the centrifuges at Iran’s Natanz nuclear plant.
What set Stuxnet apart? Security researchers uncovered a sophisticated, multi-stage attack chain. The worm leveraged multiple zero-day exploits and stolen digital certificates to infiltrate Windows systems. From there, it sought out Siemens Step7 software running on controllers inside industrial networks—not your typical corporate IT endpoints. Once inside, Stuxnet subtly altered process logic, sabotaging the actual industrial process while reporting normal operations to human operators.
This stealthy approach broke new ground in cyberwarfare. It showed how malware wasn’t just a data thief or a nuisance—it could wield real-world consequences, from damaging equipment to halting operations. Stuxnet’s analysis galvanized the cybersecurity community, sparking a surge in awareness and defense for industrial systems that continue to shape the landscape today.
The Inside Angle: Local Access as a Springboard
It’s easy to focus solely on remote threats, but local access often serves as the opening move for attackers looking to compromise SCADA systems. If a malicious actor can physically connect to a networked device—think an exposed workstation, engineering laptop, or USB port—they dramatically increase their range of options.
Once inside, attackers may:
- Escalate Privileges: With hands-on access, cybercriminals can exploit vulnerabilities that might otherwise go unnoticed. For instance, flaws in file handling or input validation could let an attacker masquerade as a system administrator or inject malicious code into critical files.
- Manipulate System Files: Techniques such as planting rogue DLLs or tampering with project files can grant backdoor access or control, bypassing safeguards that are effective against remote threats.
- Leapfrog to Critical Assets: Local access can help adversaries pivot further into the network, using compromised devices as launchpads to reach more sensitive parts of the SCADA environment.
The lesson? Physical security and strict access controls aren’t just old-school IT hygiene—they’re frontline SCADA defense. Even a single unlocked terminal or unprotected USB port can turn local presence into a full-blown cyber incident.
Decoding SCADA Attack Categories: What Matters Most
To understand how attackers approach SCADA systems, it helps to break down the key dimensions of an attack. Security professionals often use a multi-faceted lens for this, categorizing incidents by the following factors:
Type of Attack: Not all threats are created equal. Attacks can range from denial-of-service (DoS) disruptions and data breaches, to sophisticated intrusions aiming for long-term sabotage or espionage.
Attack Target: Hackers set their sights on different parts of a SCADA environment—sometimes hardware like PLCs and RTUs, sometimes the underlying software, or even the communication protocols (think Modbus, DNP3) connecting it all together.
Attack Surface: This is where vulnerabilities live. Gaps can include insecure remote access, unpatched devices, trusted third-party connections, or careless user actions. Understanding your attack surface means knowing how and where adversaries can get a foothold.
Causes: Attacks don’t happen in a vacuum. Common culprits include outdated software, misconfigured systems, insecure network connections, or human error—each presenting an opportunity for exploitation.
Consequences: The fallout from a SCADA compromise isn’t always immediate. Beyond loss of control or service disruption, the damage can cascade—impacting safety, reputation, and compliance down the line.
Impact: At the end of the day, the impacts are often measured by the CIA triad: how a breach affects availability (can the system keep running?), integrity (can you trust the output?), or confidentiality (is sensitive data exposed?).
By breaking attacks down this way, defenders can prioritize risks and shore up their defenses where it matters most.
Applying Hazard Models to SCADA Vulnerability Risk
So, how do we actually predict which vulnerabilities could spell real trouble for SCADA systems? That’s where hazard models come into play.
Think of a hazard model as a statistical crystal ball. Instead of looking for vague “threats,” it helps security teams estimate how likely a vulnerability is to be exploited over time. For SCADA environments—where the consequences of an attack aren’t just about data breaches but could cripple a water supply or shut down the power grid—this predictive power is a game changer.
Here’s why hazard models matter for SCADA:
- Prioritization: With hundreds (sometimes thousands) of vulnerabilities in the wild, hazard models help defenders focus on the ones most likely to be exploited, rather than chasing every security advisory.
- Time-to-Exploit: These models consider factors like system exposure, availability of exploit code, and historical attack patterns—helping teams gauge how urgently a patch needs to be applied.
- Resource Allocation: In environments where downtime is costly, knowing which vulnerabilities warrant immediate action versus scheduled maintenance makes a huge difference for both security and operations.
The takeaway? Hazard models don’t just add another layer of math. They enable smarter, risk-based decision making, helping OT security teams stay one step ahead of attackers—before those vulnerabilities become headlines.
Common Implementation Weaknesses: Where SCADA Systems Stumble
No matter how shiny and impressive your new SCADA deployment looks on paper, the devil is always in the details—especially when it comes to implementation. Many of the most severe vulnerabilities in SCADA environments stem from basic yet all-too-common mistakes in how systems are designed, built, or configured.
Let’s take a look at some of the classic culprits:
Insufficient Input Validation: Picture a control system that blindly trusts every bit of data it receives from sensors, user interfaces, or other components. Without proper checks, attackers can slip in malicious inputs—paving the way for buffer overflows, unauthorized access, or worse.
Path Traversal Flaws: Failing to rein in user-supplied file paths can let attackers “tunnel out” of intended directories, accessing sensitive files far outside the SCADA application’s home turf.
Command and OS Injection: When user-controlled data is fed directly into command interpreters or operating system calls without sanitization, attackers may execute arbitrary commands—often escalating their privileges or establishing remote control over victims. Systems using real-time OSs like VxWorks or Microware OS-9 can be particularly juicy targets if not tightly managed.
Lack of Input Neutralization: Data that isn’t filtered or “neutralized” can be interpreted as actual commands or code. This opens the door to attacks like cross-site scripting (XSS), where attackers inject malicious scripts that run in a victim’s browser, hijacking sessions or stealing sensitive information.
SQL Injection: Here, the application assembles database queries with user-supplied input (without proper safeguards), letting attackers manipulate database statements to steal or corrupt critical operational data.
Each of these issues boils down to assumptions—trusting that inputs are safe, that users can do no harm, or that internal interfaces are immune to tampering. In reality, these gaps are what threat actors exploit to slip through digital cracks and turn powerful SCADA systems against their operators.
Being aware of these architectural weak points is the first step toward shoring up defenses and ensuring tomorrow’s infrastructure stays resilient.

Comparing SCADA Architectures: Security and Performance at a Glance
Not all SCADA systems are created equal—especially when it comes to balancing performance and security. As technology has evolved, so too have the architectures underpinning these vital networks, each with their own quirks and vulnerabilities.
Let’s break down the essentials:
Monolithic SCADA: Think of this as the fortress with a moat—fully isolated and air-gapped from the outside world. Security is its strong suit, but it comes at the cost of reliability and scalability. These legacy systems are expensive to maintain and don’t play well with today’s demands for flexibility or real-time access.
Distributed SCADA: Here, some walls come down. Multiple control centers share responsibility, improving reliability and scaling better than monolithic setups. They typically rely on “security through obscurity”—which works just fine until someone figures out the secret handshake.
Networked SCADA: These systems take a page from modern enterprise IT, using commercial off-the-shelf hardware to drive affordability and rapid scalability. You get real-time processing, much lower latency, and parallel servers. The downside? The attack surface grows, and physical security can become a headache.
IoT-based SCADA: Welcome to the cloud era. These are designed for ultra-reliability and exceptional scalability—perfect for managing sprawling, geographically diverse assets. Performance is top-notch, and encryption standards like TLS/SSL help secure data in transit. However, with more devices online, there are more doors for attackers to try.
In summary, security tends to trade off with performance and convenience as you move from old-school monolithic systems to modern, interconnected IoT-based SCADA. Bolstering defenses often means making tough choices about operational flexibility and cost—a balancing act every security team knows all too well.
Unpacking the TAACCI Taxonomy: Classifying SCADA Attacks
So, how do security pros make sense of the barrage of attack types targeting SCADA environments? Enter the TAACCI taxonomy—a handy framework designed to break down SCADA attacks into key categories. Understanding these categories is crucial for anticipating threats and fortifying critical systems.
Here’s how TAACCI organizes the world of SCADA cyberattacks:
- Type of Attack: What’s the nature of the attempted breach? From malware infections and denial-of-service assaults to more insidious manipulation of data, identifying the type helps defenders tailor their response.
- Attack Target: Not all SCADA components are created equal in the eyes of attackers. Hardware, software, and communication protocols might each find themselves in the crosshairs, depending on the attacker’s goals—whether it’s disrupting power relays or hijacking a HMI.
- Attack Surface: Think of this as the “attackable area” of a system. It’s all the possible entry points a threat actor might exploit. For defenders, mapping this out means recognizing how vulnerabilities—like unnecessary remote access or unsecured user interaction—can snowball into bigger problems.
- Causes: The “why” behind attacks often ties back to underlying vulnerabilities. Misconfigurations, outdated firmware, or lax access controls can all open the door for trouble.
- Consequences: What happens if an attack succeeds? Anything from a corrupted data stream to disrupted operations or, in severe cases, cascading failures affecting broader infrastructure.
- Impact: This final piece zooms out to the broader fallout—how the attack affects system availability, confidentiality, and integrity. In other words: Did data leak? Was there downtime? Was something maliciously altered?
Taken together, TAACCI gives security teams a structured lens for spotting weaknesses and designing more resilient defenses for the gears that keep our modern world turning.
Security Priorities: AIC vs. CIA in SCADA and IT Environments
When it comes to protecting systems, not all environments share the same priorities—and nowhere is this clearer than in the divide between traditional IT networks and SCADA systems.
For most IT setups (think banks, e-commerce platforms, or your local hospital’s network), the focus centers around the CIA triad:
- Confidentiality: Keeping sensitive data safe from prying eyes.
- Integrity: Ensuring information can’t be tampered with.
- Availability: Making sure resources stay up and running.
SCADA systems, however, flip the script. In industrial settings managing critical infrastructure, availability comes first. After all, a water plant controller going offline doesn’t just cause inconvenience—it can risk lives and disrupt essential services. Here’s how the priorities shift:
- Availability: Systems must function continuously—downtime isn’t an option.
- Integrity: Accurate data and commands are crucial for safe operations.
- Confidentiality: Sensitive information still matters, but takes a back seat to staying operational.
In short, while both IT and SCADA environments strive to protect their systems, the “AIC” model—availability, integrity, confidentiality—best reflects what truly keeps industrial operations safe and sound.
Core Requirements for Modern SCADA Security
So, what does it take to keep a SCADA system secure and resilient in today’s threat landscape? Let’s break it down:
Privacy: To keep critical operations off the nightly news, communications within SCADA environments must be tightly protected. This means using strong encryption, access controls, and network segmentation to ensure sensitive data stays in the right hands—especially as remote access and third-party integrations become more common.
Scalability: As infrastructure grows or modernizes, your SCADA solution needs to keep up. It should handle expanding data volumes, new assets, and evolving industrial processes without requiring costly overhauls. Flexible architectures and cloud-enabled management tools can provide the needed agility while maintaining oversight and compliance.
Fault Tolerance: Unplanned downtime can have real-world consequences. Modern SCADA systems must be built to withstand both hardware hiccups and software glitches. This includes redundancy, failover capabilities, and robust monitoring, so operations continue running smoothly—even in the face of unexpected disruptions.
Keeping these core requirements front and center doesn’t just protect your network—it ensures the continued safe and reliable delivery of the services our modern lives depend on.

Redundancy, Real-Time Response, and What Makes SCADA Security Unique
When it comes to SCADA systems, uptime isn’t just a nice-to-have—it’s the cornerstone of safe, reliable operation. These systems are expected to hum along 24/7, often orchestrating critical processes where a moment’s delay can spark real-world consequences. Even brief outages, whether from cyberattack or technical failure, aren’t just inconvenient; they’re a direct threat to safety and service delivery. That’s why redundancy takes center stage in SCADA architecture.
Think of it this way: If one workstation or Human-Machine Interface (HMI) trips up, a backup is standing by, ready to take over without missing a beat. Scheduled downtime is meticulously planned weeks in advance—there’s no tolerance for surprises. Compare this with typical IT systems, which may patch or reboot with minimal fuss, and you quickly see just how high the bar is set for availability in operational technology environments.
The real-time nature of SCADA heightens this demand for continuity. Communication delays—sometimes even those lasting less than a second—can ripple into bigger operational headaches. So security measures designed for these settings must not only defend against threats but also uphold strict latency and availability requirements. In short: If a solution adds lag or takes control systems offline for too long, it simply won’t cut it.
This focus on redundancy and immediacy shapes every security and operational decision in SCADA—from layered network defenses to robust failover protocols.
Why Analyze SCADA Vulnerabilities? Understanding the Why
When it comes to keeping SCADA environments safe, knowing how attacks have happened—and why attackers are motivated—offers critical insight for building your defense.
Over the years, some infamous breaches have acted as wake-up calls: think compromised gas pipelines, tampered wastewater stations in Australia, and headline-grabbing worms like Stuxnet that caused physical sabotage on an international scale. These incidents weren’t just about digital mischief. They exposed the real-world consequences of failing to secure control systems: power outages for thousands, environmental contamination, or national security risks.
So, why conduct a thorough survey or review of SCADA vulnerabilities and attacks? The objectives are clear:
- Map the Threat Landscape: By reviewing patterns from past incidents, we can identify which SCADA components and protocols are most frequently targeted by attackers—whether for financial gain, sabotage, or espionage.
- Identify Weak Links: A systematic review helps unearth architectural flaws, exploitable communication channels, and recurring vulnerabilities that adversaries are actively seeking.
- Guide Security Improvements: The insights gained steer the development or fine-tuning of intrusion detection systems (IDS), hardening of protocols, and smarter defensive strategies tailored to real-world attack chains.
- Bridge Knowledge Gaps: Many organizations lack robust SCADA-specific datasets for research and training. Surveying previous attacks encourages the development of realistic testbeds, supporting both innovation and response readiness in the face of evolving threats.
- Anticipate the Adversary: Perhaps most importantly, understanding not just how, but why attacks succeed builds a mindset focused on breaking the attack chain before it leads to disaster.
For researchers, engineers, and security teams, these reviews aren’t just academic exercises—they’re foundational steps to prevent the next big outage or breach.
By learning from the past and questioning how each system could be leveraged in future attacks, the industry equips itself to move from reactive to proactive.
Emerging Threat Trends: What to Watch For
The threat landscape is anything but static. Staying ahead requires understanding the latest attack vectors and methodologies:
- Targeting IT/OT Convergence Points: As Information Technology (IT) and Operational Technology (OT) networks become more integrated, attackers are exploiting vulnerabilities at these convergence points to pivot from less secure enterprise systems into critical control environments. These vulnerabilities often stem from familiar culprits: improper input validation, default or hard-coded credentials, insufficient encryption, and weak access controls. For instance, protocols like DNP3 are especially susceptible—weak encryption within DNP3 messages can enable reconnaissance or man-in-the-middle attacks, while improper resource control exposes them to denial-of-service (DoS) threats.
Seemingly minor oversights, such as an uncontrolled search path or failure to set strong authentication, can open the door to arbitrary code execution or information disclosure. In practice, a single buffer overflow in a SCADA component—often the result of poor memory management—can cascade into larger incidents, including operational disruptions or enabling further attacks. The takeaway: every overlooked detail, from network segmentation to credential management, can become a stepping stone for attackers looking to breach the IT/OT divide.
- Ransomware with an OT Twist: Ransomware attacks are no longer confined to encrypting data. We’re seeing an alarming trend where attackers specifically target OT processes, threatening to disrupt physical operations unless a ransom is paid. This can halt production, disrupt essential services, and create significant safety risks.
- Sophisticated Nation-State Activity: Nation-state actors continue to show a keen interest in SCADA systems, often with the goal of reconnaissance, establishing persistence for future disruption, or outright sabotage. These attackers typically have significant resources and employ advanced, stealthy techniques. One hallmark of their approach is the use of reconnaissance tactics that exploit weak encryption protocols—such as within DNP3 messages—to quietly map out network topology, probe for device functions, and gather sensitive information stored on automation controllers. Successful reconnaissance enables adversaries to masquerade as legitimate components and set the stage for more targeted attacks, including code injection and command spoofing. This patient, methodical information gathering is often the precursor to more destructive activity, allowing attackers to blend in and escalate their access over time, while defenders may remain unaware until it’s too late.
- Exploitation of Remote Access: The increased need for remote operation and maintenance has expanded the attack surface. Weak or improperly secured remote access solutions provide a direct pathway for attackers into SCADA networks.
- Supply Chain Vulnerabilities: Attackers are increasingly targeting the supply chain, compromising software, hardware, or third-party vendors that have access to SCADA environments. A single compromised supplier can provide a foothold into numerous target organizations.
- AI-Powered Attacks (and Defense): Artificial intelligence is a double-edged sword. Attackers are exploring AI to automate reconnaissance, craft more convincing phishing attacks, and identify vulnerabilities faster. Classic reconnaissance techniques—like network sniffing and scanning—remain foundational, but are now supercharged by machine learning. Tools such as Wireshark are widely used for capturing and analyzing local network traffic, giving attackers a detailed map of SCADA system activity. Meanwhile, network scanners like Nmap can quickly enumerate hosts, open ports, and the services running on them, making it easier than ever to inventory a target environment. Combined with AI-driven analysis, these traditional methods allow threat actors to rapidly gather intelligence, prioritize their targets, and customize their attack strategies with unprecedented speed and precision. Conversely, defenders are also leveraging AI and machine learning for advanced anomaly detection and faster incident response.
- Attacks Aiming for Physical Disruption: A deeply concerning trend is the rise of attacks specifically designed to cause physical damage or disruption. This moves beyond data theft or encryption to actively manipulating control systems to unsafe states.
Notorious SCADA Vulnerabilities: Real-World Examples
If you’re wondering just how vulnerable commonly deployed SCADA systems and industrial control hardware can be, unfortunately, there’s no shortage of cautionary tales. In recent years, security advisories from respected sources—including US-CERT—have documented a steady drumbeat of critical weaknesses uncovered in some of the most popular industrial platforms.
Here are some notable examples of vulnerabilities that have made headlines (and headaches) for operators:
Denial-of-Service in Industrial Protocols: Several SCADA platforms have suffered from weaknesses in core communication protocols (like DNP3), which attackers could exploit to crash or disrupt entire networks—potentially halting processes and operations until controls are restored.
Remote Code Execution Flaws: Vulnerabilities have been discovered in HMIs (Human-Machine Interfaces) and historian software, allowing attackers to run malicious code remotely. Such issues in components used for data aggregation and process visualization could lead to widespread system compromise or sabotage.
Insecure Firmware and Software Components: Devices and controllers—think PLCs and smart panels—have, on more than one occasion, shipped with firmware bugs that allow unauthorized access, privilege escalation, or even bricking of critical hardware.
Authentication Bypasses: A perennial favorite for attackers. Certain engineering and configuration tools have been found to contain flaws enabling unauthorized users to bypass authentication controls and gain administrator-level access.
Supply Chain and Third-Party Software Holes: Vendor software used for setup, diagnostics, or remote management has sometimes contained hidden vulnerabilities, providing attackers with a stealthy entry point through trusted channels.
Case after case—from process historians and panel software to configuration tools and communication gateways—proves that vulnerabilities, both old and new, remain a reality in the SCADA ecosystem. Awareness and timely patching are your best friends in the ongoing effort to reduce exposure.

How SCADA Vulnerabilities Become Attack Gateways
So, how do attackers actually break in? It usually starts with vulnerabilities—those little cracks in the armor that make cyber intrusions possible. In the world of SCADA, these weaknesses are strikingly common and, unfortunately, often overlooked.
- Buffer Overflows and The Domino Effect: When a SCADA component doesn’t properly control how much data can be shoved into its memory buffer, attackers can overflow it—causing it to misbehave in unpredictable ways. This isn’t just a technical nuisance; it could allow an adversary to crash the system (Denial-of-Service) or run malicious code, opening the door for even larger attacks.
- Improper Input Validation: If a system doesn’t thoroughly check the data it receives (think user input or network traffic), attackers can sneak in all sorts of crafted payloads. These can bypass defenses, disrupt operations, or lead to unauthorized access—potentially letting attackers command critical machinery.
- Default and Hard-Coded Credentials: Many SCADA devices ship with default usernames and passwords, or store credentials right in the code (like sticking a spare house key under the welcome mat). Attackers often scan for these easy points of entry, using them to slip past authentication and roam freely within the network.
- Weak Encryption and Protocol Flaws: Industrial protocols such as DNP3 often lack strong encryption or proper resource controls. This allows attackers to intercept communications (man-in-the-middle attacks), launch DDoS attacks, or eavesdrop on sensitive control messages—sometimes even manipulating them in real time.
In short, each overlooked flaw—whether it’s an unpatched buffer, a weak password, or an insecure protocol—serves as a potential foothold for adversaries. Once inside, attackers can escalate privileges, pivot to other systems, and cause the kinds of physical or operational disruption that keep plant managers up at night.
Notorious PLC-Targeting Malware: What’s Lurking in the Shadows?
Malware designed to compromise programmable logic controllers (PLCs) isn’t just the stuff of cybersecurity horror stories—it’s a harsh reality for modern industrial environments. Among the most infamous examples is “PLC-Blaster,” a worm that first drew attention at Black Hat Asia 2016. Unlike traditional malware, PLC-Blaster demonstrated the unnerving capability to propagate solely between PLCs, bypassing conventional endpoints altogether. By exploiting logic blocks and trusted communication protocols, threats like this can silently move laterally within industrial networks, making detection particularly challenging.
But PLC-Blaster is far from alone. Other headline-grabbing threats—like Stuxnet, Industroyer (CrashOverride), and TRITON—have shown just how sophisticated and destructive PLC-targeting malware can become. These strains aren’t just proof-of-concept experiments; they’re engineered to disrupt, manipulate, or even destroy physical processes that keep factories, utilities, and infrastructure running.
The common thread among these attacks? They leverage deep knowledge of industrial protocols and vendor-specific quirks to blend into normal operations until it’s too late. The stakes couldn’t be higher: a successfully compromised PLC can spell disaster, underscoring why SCADA cyber defense demands more than just basic IT hygiene.
Key Resources for Industrial Cyber Threat Intelligence
Navigating this hostile cybersecurity landscape requires more than just vigilance—it calls for up-to-date intelligence and practical guidance from trusted organizations. Fortunately, several institutions regularly publish advisories, vulnerability reports, and best practices tailored for industrial control systems (ICS) and SCADA environments.
- CISA’s US-CERT Advisories: The and its US-CERT division are go-to sources for the latest alerts on critical vulnerabilities, detailed guidance on threat mitigation, and threat summaries, including those involving highly sophisticated actors and nation-state campaigns. Their Industrial Control Systems advisories cover a wide range of ICS/SCADA products, from PLC firmware flaws to software vulnerabilities.
- Vendor-Specific Updates and Security Bulletins: Industrial automation giants like Siemens and Schneider Electric routinely issue security bulletins and software patches as new threats are discovered. Staying connected to your vendors’ security advisory feeds is essential for timely response.
- Sectoral ISACs: Information Sharing and Analysis Centers (ISACs) such as the and focus on real-time threat intelligence and collaborative reporting specifically designed for critical infrastructure sectors.
- Global Intelligence Sharing Platforms: International initiatives and public-private partnerships, such as those led by the , offer threat reports and toolkits explicitly covering SCADA and OT environments.
- Third-Party Cyber Threat Feeds: Commercial providers and nonprofit organizations (like SANS ICS, Dragos, Mandiant, and Recorded Future) deliver deep-dive analyses on emerging malware, tactics, and adversary groups targeting ICS worldwide.
Leveraging these resources will help you stay ahead of rapidly evolving nation-state tactics as well as the broader spectrum of threats facing modern SCADA systems.
Challenges Facing Cloud-Assisted IoT SCADA Security
So, what exactly is keeping security professionals up at night when it comes to cloud-assisted IoT-based SCADA systems? It’s a digital tightrope walk, with new hurdles appearing as quickly as we clear the old ones.
Current Pain Points
- Expanding Attack Surface: Integrating IoT devices and cloud connectivity means more endpoints and network pathways to defend. Each device—whether it’s a sensor in the field or a remote access portal—can become an entry point for attackers if not properly secured.
- Complex Access Control: The convenience of remote monitoring and management comes with the headache of enforcing robust authentication and authorization. Ensuring that only the right people and systems have access, at the right times, is far from trivial when you’re juggling on-premise, cloud, and edge devices.
- Data Security & Privacy: Sensitive industrial data flowing between on-site devices and public or hybrid clouds raises concerns around interception, unauthorized access, and regulatory compliance. Encryption in transit and at rest is essential, but not always consistently applied across all components.
- Visibility and Monitoring Challenges: Traditional monitoring tools may fall short when traffic spans local, cloud, and IoT networks. Keeping tabs on who’s doing what, where, and when across this hybrid environment is an ongoing challenge for incident detection and response.
What’s on the Horizon?
- Evolving Threat Actors: As defenders up their game, attackers are also sharpening their tools—including harnessing AI for more sophisticated campaigns. Expect more automated exploits targeting weaknesses unique to cloud-enabled and IoT-heavy SCADA deployments.
- Interoperability and Standards Gaps: The patchwork of vendor platforms, legacy hardware, and evolving standards can create blind spots and compatibility headaches. Ensuring seamless, secure communication across systems requires ongoing attention.
- Scalability and Performance vs. Security: Balancing the need for rapid scaling and ultra-low latency with tight security controls can lead to trade-offs. Often, usability and rapid deployment win out over rigorous security—until something goes wrong.
- Supply Chain Complexity: With more third-party software and services woven into the fabric of SCADA networks, securing the entire ecosystem—including upstream vendors and dependencies—will only become more critical (and complicated).
In short, while cloud-assisted IoT brings impressive capabilities to SCADA systems, it also demands a vigilant, adaptable approach to cybersecurity—one that evolves just as quickly as both the technology and the threats.
How IEC 60870-5-104 SCADA Systems Are Targeted—And Why It Matters
IEC 60870-5-104, a protocol widely used for remote control and monitoring in power systems, has become a favored target for attackers seeking to disrupt critical infrastructure. Unlike more obscure, proprietary protocols, 104’s adoption of TCP/IP makes it especially susceptible to cyber threats that exploit IT/OT convergence points.
Attackers can capitalize on several weaknesses:
- Unencrypted Communications: Unless properly secured, data sent over 104 is often unencrypted, making it ripe for interception and manipulation. Attackers can eavesdrop, replay legitimate commands, or inject malicious traffic to alter system behavior.
- Weak Authentication: If robust authentication mechanisms are absent or poorly implemented, cybercriminals or even disgruntled insiders may masquerade as legitimate control operators—opening the door to unauthorized command execution.
- Protocol-Specific Exploits: The protocol’s design can allow for reconnaissance, revealing sensitive information about the underlying process and network topology. Adversaries may map out the system to plan more damaging, targeted attacks.
- Man-in-the-Middle (MitM) Attacks: Compromising a network segment between control centers and field devices gives attackers a perch to modify commands or status messages, leading to false alarms, denied control actions, or even physical disruption—such as opening circuit breakers or shutting down substations.
The consequences of successfully attacking IEC 60870-5-104 go well beyond nuisance or data theft. Disruption of this protocol can result in blackouts, damaged equipment, safety hazards, and service outages. The risk is compounded by increased remote access and interconnectivity, making defense-in-depth and protocol-aware monitoring tools absolutely critical for operators relying on this standard.

How Encryption and Resource Control Gaps Open the Door to Attacks
Weaknesses in encryption and resource management are a goldmine for attackers looking to exploit SCADA protocols—and unfortunately, these gaps are still all too common in industrial environments.
Insufficient Encryption: More Than Just Eavesdropping
Many SCADA communication protocols, such as DNP3 or older Modbus variants, often lack robust encryption. This makes it far too easy for malicious actors to intercept data in transit—essentially eavesdropping on sensitive operational details. Beyond just passive listening, inadequate encryption opens the door to man-in-the-middle (MITM) attacks, where hackers can not only see but also manipulate communications, potentially sending unauthorized commands or altering device configurations with little resistance.
Resource Control Failures: A Gateway to Disruption
On the other front, poor resource control—think unsecured protocols or improperly managed device authentication—gives attackers a perfect avenue for denial-of-service (DoS) and distributed denial-of-service (DDoS) campaigns. For example, when a SCADA protocol does not strictly validate incoming messages, adversaries can flood a device or network segment with malformed packets. This barrage can overwhelm system resources, causing slowdowns, system crashes, or even complete shutdowns.
Reconnaissance: Building the Attack Blueprint
Weak encryption also means attackers can more easily map out your network and identify critical assets by capturing and analyzing traffic. This reconnaissance phase allows them to learn which devices perform which functions—and plan more targeted, damaging attacks down the line.
In short, vulnerabilities in both encryption and resource management provide attackers with multiple tools, from silent observation and manipulation to full-scale disruption and even groundwork for deeper incursions. Addressing these gaps with protocol hardening, secure authentication, and encrypted communication channels isn’t just a best practice—it’s a necessity for modern SCADA defense.
Key Security Gaps in Smart Grid-Based SCADA Systems
While the modernization of SCADA systems for smart grid integration brings efficiency and new capabilities, it also amplifies risk by introducing specific security gaps that attackers can exploit:
Legacy Components with Inadequate Safeguards: Many smart grid SCADA environments include older devices and software that were never designed with cybersecurity in mind. These legacy components often lack basic security features like encryption or authentication, creating soft targets for adversaries.
Insecure Communication Protocols: Traditional industrial protocols (think Modbus, DNP3) are notoriously weak in terms of security, often transmitting sensitive data in cleartext. Without updates or secure wrappers, these protocols offer an easy eavesdropping opportunity.
Patchwork System Integration: As utilities bolt on new technologies and connect a patchwork of vendor solutions, inconsistent security standards and poor interoperability can lead to critical blind spots or misconfigurations across the network.
Weak Authentication and Authorization: Many SCADA deployments rely on shared credentials, lack robust user access controls, or fail to limit privileges appropriately—making it easier for attackers to escalate their access if they breach the perimeter.
Limited Network Segmentation: Rather than isolating critical control systems from less secure IT assets, some organizations still maintain flat network architectures. This makes lateral movement a breeze for intruders.
Insufficient Monitoring and Incident Response: Smart grid SCADA systems are still catching up when it comes to continuous monitoring and rapid response. Without proper network visibility and early warning mechanisms, breaches may go undetected until damage occurs.
Addressing these gaps requires a tailored approach—layering modern security controls, segmenting networks, upgrading legacy equipment, and prioritizing cybersecurity as a continuous process rather than a one-time fix.
Decoding Man-in-the-Middle Attacks on IEC 60870-5-104 SCADA Networks
Among the most insidious threats facing industrial environments today is the man-in-the-middle (MitM) attack, particularly as it pertains to widely used SCADA protocols like IEC 60870-5-104. But what exactly does this mean for organizations relying on this protocol to manage critical infrastructure?
In simple terms, a MitM attack involves an adversary stealthily intercepting, altering, or injecting communications between two trusted parties—often without either side realizing anything is amiss. When targeting IEC 60870-5-104, attackers exploit gaps in the protocol’s lack of strong authentication and encryption. This allows them to eavesdrop on or manipulate the real-time commands and telemetry exchanged between control centers and field devices.
The risks here are nontrivial. A successful MitM attack could result in false status updates, malicious control commands, or even the covert manipulation of data intended to obscure deeper sabotage. Imagine a malicious actor quietly opening breakers, tampering with measurement values, or masking alarm signals—all while operators believe systems are functioning as expected.
Understanding how these attacks unfold is the first step to mitigating them. Key factors to consider include:
- Weak Authentication: Without robust identity verification, attackers can impersonate trusted devices or operators.
- Unencrypted Traffic: Plain-text communications make it easier for adversaries to intercept and decipher sensitive information.
- Protocol-Specific Flaws: IEC 60870-5-104, due to its age and original design goals, lacks some of the security features considered standard in modern IT protocols.
Mitigating MitM threats requires a defense-in-depth approach. Leading practices include segmenting networks, enabling encryption and authentication mechanisms (where possible), monitoring traffic for anomalies, and keeping a close eye on configuration changes. Solutions from trusted vendors like Fortinet and Nozomi Networks can also help detect and disrupt suspicious activity specific to industrial protocols.
Recognizing MitM threats in SCADA environments isn’t just about fancy tooling—it’s about fostering a security-first mindset, understanding protocol limitations, and implementing layered defenses that can adapt as tactics evolve.
Cloud-Based SCADA: New Cyber Risks on the Horizon
Integrating SCADA systems into cloud environments undoubtedly boosts flexibility, scalability, and remote accessibility—but it introduces a fresh wave of cybersecurity risks that can’t be ignored.
One of the most pressing concerns is the risk of Man-in-the-Middle (MITM) attacks. By leveraging cloud connectivity, attackers can intercept and manipulate data as it travels between SCADA components and the cloud. This not only threatens the confidentiality and integrity of critical control information but can also enable adversaries to disrupt or even sabotage operations by subtly altering commands or sensor data in transit.
Data leakage is another critical issue. Moving sensitive industrial data off-premises means relying on a third-party provider’s infrastructure, increasing the risk that proprietary or confidential information could be exposed—either through misconfigurations, vulnerabilities, or insider threats within the cloud provider’s environment.
Furthermore, the cloud expands the overall attack surface. Improperly secured cloud interfaces, weak authentication, or mismanaged API endpoints can all become convenient entry points for hackers looking to pivot deeper into connected ICS and critical infrastructure (CI). Meanwhile, backdoors—whether unintentional or the result of advanced persistent threats—may be harder to detect and close compared to traditional, air-gapped SCADA networks.
The bottom line? While the cloud unlocks new capabilities, it also demands heightened vigilance and robust security measures tailored to the nuances of both industrial systems and virtualized environments.
How Man-in-the-Middle Attacks Intercept SCADA Data
One threat vector that deserves extra attention is the man-in-the-middle (MITM) attack—a tactic as audacious as it is dangerous. Here’s how it usually unfolds: An attacker positions themselves between the SCADA device and its intended communication partner. By exploiting weak authentication or lack of encryption (which, unfortunately, is still common in certain industrial protocols like DNP3 over TCP), the attacker quietly intercepts all data flowing between the devices.
Once in the middle, the attacker can eavesdrop on sensitive communications, harvest credentials, or even hijack legitimate sessions to issue malicious commands—all without the legitimate parties realizing anything is amiss. This is often accomplished by targeting unsecured network ports (such as HTTP over port 80), taking advantage of outdated firmware, or abusing misconfigured access privileges.
In short, if SCADA communications aren’t properly secured with strong authentication and encryption, MITM attacks make it alarmingly easy for adversaries to capture, alter, or disrupt critical operational data—potentially impacting everything from real-time monitoring to physical process control.
How Malware Like Havex Chooses Its Targets in ICS Environments
Understanding how advanced malware selects its targets in industrial control system (ICS) environments helps shine a light on the risks facing SCADA operators today. Take, for example, the infamous Havex malware. Rather than operating like a digital bull in a china shop, Havex takes a calculated, measured approach to infiltration.
Security researchers often evaluate such malware by looking at three key factors:
- Reconnaissance Capabilities: Havex and similar threats are built to perform deep reconnaissance once inside an ICS environment. The malware scans for specific industrial devices, protocols (such as Modbus or OPC), and active process networks, mapping out what’s valuable and vulnerable before making a move.
- Targeted Scanning and Data Collection: Instead of indiscriminate infection, Havex uses specialized plugins to hunt for particular types of control systems and engineering workstations. It collects system information and configuration data, sending it back to the attackers so they can identify high-value targets within the network.
- Quantitative Analysis by Security Teams: To understand just how selective a malware like Havex can be, experts conduct quantitative evaluations—tracking which devices were probed and how often, which network segments were scanned, and analyzing device logs to reveal patterns in how the malware chose its targets.
Through this methodical approach, malware authors maximize impact while reducing the chance of early detection. For defenders, analyzing past campaigns—complete with their reconnaissance behavior—provides critical insight into what these attackers are likely to pursue next.
Malicious File Injection: SCADA’s Hidden Entry Point
One attack vector that deserves special attention is malicious file injection—a favorite trick amongst those with less-than-friendly intentions. In essence, malicious file injection is when an attacker sneaks harmful commands or code into a SCADA environment by disguising them as legitimate files, inputs, or requests.
How does this actually unfold in the wild? Adversaries might craft input data, code, or project files that, when loaded by a SCADA device or application, exploit weaknesses like poor input validation or unchecked file handling. Consider these attack scenarios:
- Corrupting PLCs and RTUs: Attackers may send purpose-built packets or files to programmable logic controllers (PLCs) or remote terminal units (RTUs) with the goal of manipulating system behavior or corrupting memory—sometimes triggering denial-of-service (DoS) events or worse.
- Cross-Site Attacks via Web Interfaces: If a SCADA web application isn’t validating input properly, an attacker can inject malicious scripts into its web pages, potentially gaining unauthorized privileges or executing code on user endpoints.
- Path Traversal: By cleverly manipulating file path requests—think
../../tricks—bad actors can access sensitive directories or configuration files, opening the door to all sorts of mischief. - Buffer Overflows: Some SCADA human-machine interface (HMI) applications are vulnerable to buffer overflow attacks, where a carefully crafted file can crash the system or create an opening for deeper infiltration.
The upshot? Malicious file injection is a flexible and often highly effective means of piercing a SCADA system’s defenses, whether the target is a legacy PLC, modern digital gateway, or the trusty interface that operators use every day.
Staying alert to these vectors—and ensuring robust file validation and restricted privileges—remains essential in defending against these cunning attacks.
Denial-of-Service (DoS) Attacks on SCADA Historian Systems
Data historians—the vaults of real-time process data in SCADA environments—are a tempting target for attackers seeking to disrupt operations. Denial-of-service attacks against these historian databases can bring critical monitoring and logging to a screeching halt, hampering both real-time visibility and forensic investigations.
Common ways adversaries launch DoS attacks on SCADA historian systems include:
- Exploiting Parsing Vulnerabilities: Attackers may send specially crafted XML or other malformed data packets to historian servers. If the historian software fails to properly validate or parse this input, it can crash, hang, or exhaust system resources. Several popular solutions, such as those from Schneider Electric and GE Digital, have seen patches for these types of parsing flaws.
- Resource Exhaustion: Flooding the historian with a massive volume of requests—whether through automated scripts or botnets—can overload the server’s memory, CPU, or disk space. Once critical system resources are depleted, the historian may become unresponsive or shut down entirely.
- Protocol Abuse: SCADA historians often communicate using proprietary or industrial standards like OPC or OLE. Attackers might exploit weak protocol implementations or use specially constructed requests to induce failures.
- File and Log Manipulation: Attempts to fill up storage by repeatedly writing junk data or corrupt log files can deny access to new data, leading to gaps in historical records and potential loss of operational insight.
A successful DoS attack on a historian doesn’t just cause a temporary hiccup—it can blind operators to unfolding incidents and delay forensic response, creating a ripple effect across monitoring, compliance, and safety operations. Staying vigilant about software updates, scrutinizing logs for abnormal data uploads, and rate-limiting incoming historian requests can help minimize this risk.
Key Security Risks Facing SCADA Historian Databases
When it comes to SCADA environments, historian databases—those repositories storing time-series process data—sit in a precarious spot. These systems are rich targets, so securing them is anything but optional. Here are the leading concerns:
- Default and Weak Authentication: Too often, historian databases come with default credentials out of the box, and these rarely get changed or hardened. Attackers can easily leverage these to gain unauthorized entry, putting sensitive operational data at risk.
- Denial-of-Service (DoS) Vulnerabilities: A common issue is improper validation when parsing XML or other inputs, which can open the door to denial-of-service attacks. Successful exploitation can crash the historian service, effectively blinding operators to process histories and events when they’re needed most.
- Injection Attacks and Data Corruption: Historian systems often include web interfaces for user and admin access. Without robust input sanitization, they can be susceptible to SQL injection or similar attacks. An adversary might craft malicious requests that corrupt historical data or expose critical information, undermining both operational integrity and your compliance posture.
Bottom line: the historian isn’t just about record keeping; it’s a critical component that, if compromised, can impact everything from regulatory reporting to incident response. It deserves the same rigorous security attention as any other piece of your SCADA architecture.
Vulnerabilities Enabling Packet Modification and Resource Exhaustion in RTUs
The reality is, Remote Terminal Units (RTUs) have their own Achilles’ heels. Much like their PLC cousins, RTUs often ship with default credentials left unchanged—making them low-hanging fruit for attackers. If these are never updated, even unprivileged users could quietly slip in, tweak crucial system settings, or in some cases, hijack the entire device.
But it doesn’t end there. Poor connection management is another common pitfall. Some RTUs may fail to properly close out previous I/O connections, instead leaving multiple sessions running simultaneously. Over time, this carelessness piles up, exhausting critical resources. The result? The RTU can get bogged down to the point of becoming unresponsive, opening the door for straightforward denial-of-service (DoS) attacks.
These seemingly basic oversights—unchanged default passwords and sloppy connection handling—can make an RTU an easy mark. And in an environment where uptime is everything, these vulnerabilities are more than just theoretical risks.
Risks of Information Disclosure from Poor Credential Management in PLCs
When credentials aren’t properly managed in Programmable Logic Controllers (PLCs), attackers can find an open door—and they’re more than willing to stroll right in. Weak or mishandled authentication systems allow adversaries to remotely connect to critical PLC ports, often without triggering alarms. Once inside, malicious actors can extract sensitive information such as authentication details, system configurations, or even operational data.
What does this mean for your SCADA environment? With stolen credentials, attackers gain the keys to the kingdom. They can:
- Move laterally within the network, escalating their access and targeting other critical assets.
- Bypass protective measures meant to safeguard sensitive industrial processes.
- Collect intelligence for future attacks—sometimes without ever being detected.
The bottom line: Poor credential management doesn’t just risk a single device; it threatens the integrity and confidentiality of your entire control system. That’s why robust, regularly updated authentication protocols are more than a best practice—they’re a non-negotiable frontline defense.

How Cross-Domain Attacks on Cyber-Physical Systems Are Classified
Cross-domain attacks on cyber-physical systems (CPS) don’t fit neatly into traditional IT or OT attack categories—they’re slippery and inventive, traversing the blurred boundaries between digital and physical realms. So, how do security professionals categorize and describe these multi-pronged threats?
Generally, cross-domain attacks are organized based on how they exploit the interfaces between different system domains, such as IT-OT bridges, networked sensors, actuators, and control logic. Here’s how experts break them down:
- Origin and Target Domains: Taxonomies often start by identifying the source and destination. For example, does the attack originate in the IT domain (think spear phishing) and migrate into OT to disrupt a physical process? Or does it move the other way around?
- Attack Pathways: These attacks frequently leverage vulnerabilities in integration points—like network gateways, protocol converters, or vendor-supplied remote maintenance tools.
- Techniques Used: Categories include lateral movement across domains, protocol manipulation (for example, abusing Modbus or DNP3 to inject malicious commands), and exploiting misconfigured access controls that span both digital and operational layers.
- Intended Impact: Are attackers aiming for data theft, process disruption, equipment damage, or safety system evasion? The taxonomy typically evaluates what’s at risk and the consequences of compromise.
Think of cross-domain attacks like a seasoned cat burglar who slips not just through one window, but connects hallways, ductwork, and even the building’s plumbing to reach the unguarded vault. The most useful taxonomies help defenders visualize these connections and anticipate how attacks might leapfrog from seemingly minor network footholds into the heart of critical infrastructure.
SQL Injection: Undermining SCADA Data Integrity and Confidentiality
One attack vector that keeps defenders up at night is the infamous SQL injection—an old-school trick with a distinctly modern edge in SCADA environments. At its core, an SQL injection exploits poorly secured web interfaces or APIs—common in many SCADA historian modules—by inserting malicious code into database queries.
Here’s why this matters: SCADA historians are the keepers of operational data, logging every valve turn, alarm, and pressure reading. When these interfaces don’t properly sanitize user inputs, a bad actor can send crafted requests that manipulate the system’s underlying database.
The consequences? Far from trivial. Attackers can:
- Modify or Erase Historical Records: By issuing unauthorized commands, an intruder could alter or delete crucial event logs, making it difficult—or impossible—to reconstruct the true sequence of events during an incident or audit.
- Steal Sensitive Information: Confidential operational data, such as production volumes or proprietary control settings, can be exfiltrated and weaponized for industrial espionage or competitive advantage.
- Corrupt Data Integrity: Altered or injected data points can trigger false alarms, mask real issues, or even feed erroneous information back into automated control loops—potentially leading to unsafe operations.
- Facilitate Broader Attacks: Once foothold is gained, attackers may escalate privileges, pivot deeper into the network, or establish persistence for future campaigns.
Staying vigilant requires robust input validation, regular security reviews, and keeping those historian modules patched—because all it takes is one unfiltered web request to rewrite your data’s history, literally.
Privilege Escalation via Packet Capture and Reply Modification
One particularly troubling attack technique in the SCADA realm involves privilege escalation through packet capture and reply tampering. Here’s how it typically unfolds:
An attacker with network access can intercept the communication between a master terminal unit (MTU) and remote terminal units (RTUs) or programmable logic controllers (PLCs)—the backbone of most industrial control environments. If authentication is weak or missing altogether (a not-uncommon scenario in legacy systems), an attacker can capture legitimate command-and-control packets in transit.
With these packets in hand, the attacker can alter their contents, subtly tweaking instructions or replaying previous messages. These maliciously modified packets are then sent along to the intended recipient, which, lacking robust authentication mechanisms, treats them as valid. This can grant the attacker elevated privileges—letting them initiate, delay, or repeat operational commands within the control system.
The impact? Processes like valve operations or safety shutdowns can be manipulated or disrupted, potentially leading to process delays, safety hazards, or operational outages, all without triggering immediate alarms. This method highlights why strong authentication and encrypted communication channels are critical for modern SCADA deployments.
Cyber-Physical Systems-Based Threat Modeling for Critical Infrastructure
So, how do defenders get ahead of this ever-evolving threat landscape? Enter: threat modeling tailored specifically for cyber-physical systems (CPS)—the backbone of modern SCADA environments. Unlike traditional IT, where the focus is heavily on data, CPS threat modeling must account for the tangible impact cyber incidents can have on the real world. We’re talking about electricity grids, water treatment facilities, transit systems—essential services that, if disrupted, can have dramatic, real-world consequences.
Here’s how CPS-based threat modeling typically unfolds for critical infrastructure:
- Holistic Asset Identification: Start by mapping out all physical and digital components, from sensors and actuators to controllers and networked devices. This includes understanding the flow of information and dependencies between components. No detail is too small; if it connects or communicates, it’s on the list.
- Adversary Profiling: Consider the motives, capabilities, and tactics of likely adversaries—from curious insiders to organized criminal syndicates and nation-state groups. Attack paths are analyzed based on the unique blend of cyber and physical access points in SCADA systems.
- Attack Vector Analysis: Model how an attacker might traverse the system—whether through exploiting vulnerable PLCs, manipulating data in transit, or accessing poorly secured remote maintenance ports. Special attention is paid to cascading effects: how a compromise in a single subsystem could ripple into wider operational disruption.
- Impact Assessment: Go beyond data loss; evaluate the real-world consequences of a successful attack. Outcomes can include physical damage to assets, environmental spills, service outages, or safety incidents.
- Defense Prioritization: Use the results to prioritize controls—like segmentation between IT and OT, monitoring for anomalous physical behaviors, and hardening remote access points. It’s not just about ticking boxes; it’s about mitigating the threats that matter most to both uptime and safety.
Threat modeling for critical infrastructure using CPS isn’t a one-off exercise. It’s a living, breathing process that adapts to new technologies, changing operational needs, and—yes—ever more creative adversaries.
By embedding threat modeling in your SCADA security strategy, you’re not just playing catch-up—you’re taking the offensive in defending what matters most.
The Role of User Interaction in SCADA Exploits
Not all SCADA vulnerabilities are automatically exploitable—the human element can be a pivotal factor. In many scenarios, attackers require some form of user interaction to initiate an attack. This can include convincing a technician to open a phishing email, click a malicious link, or unknowingly install compromised software via a USB drive. Even seemingly routine actions, like acknowledging an alert or misconfiguring remote access tools, can open doors for attackers if social engineering is involved.
Crucially, even if a weak point exists in a SCADA environment, adversaries still need a viable pathway to reach their intended target—often relying on crafty manipulation of staff or exploiting poorly segmented networks. It’s a potent reminder that cybersecurity isn’t just a matter of patching software, but also of building a culture of vigilance among the humans operating critical infrastructure.

The Anatomy of Improper Authentication: Variants and Risks
When it comes to SCADA systems, authentication should never be an afterthought. Unfortunately, improper authentication remains a recurring Achilles’ heel, providing numerous footholds for attackers. So, what does “improper authentication” actually look like in the wild? Let’s dig in:
Bypassing Authentication Altogether: Sometimes, developers leave hidden or undocumented pathways into a system—routes that skip authentication entirely. Attackers who find these backdoors can waltz right in, no password required.
Hard-Coded Credentials: A classic blunder involves embedding usernames, passwords, or cryptographic keys directly into device firmware or software. Since these credentials can’t be changed by end users, attackers who obtain them (through leaked documentation or reverse engineering) can gain persistent access—often across many deployments.
Replay Attacks (Capture-Replay): Here, attackers sniff network traffic, grab valid authentication tokens or credentials, and replay them to fool the system into granting access. Without mechanisms like nonce values or session expiration, SCADA systems can be dangerously vulnerable to this trick.
Weak or Missing Certificate Validation: If a system fails to validate digital certificates correctly, attackers can present fake certificates and masquerade as legitimate users or control centers. It’s a fast lane for man-in-the-middle attacks and privilege escalation.
Default Passwords Left Unchanged: Out-of-the-box passwords like “admin/admin” or “user/user” are well-known to attackers. When organizations neglect to update these defaults, the door is left wide open for unauthorized access—not just to view, but potentially to alter vital process controls.
No Limits on Invalid Authentication Attempts: Some SCADA products don’t restrict the number of failed login attempts, making them easy prey for brute-force attacks. Automation tools can hammer away until they hit the right password—no questions asked.
Improper Authorization Controls: It’s not enough to just know who you are; it’s also about what you’re allowed to do. Improper authorization means users—legitimate or not—might get access to sensitive resources or critical operations beyond their intended role.
Unprotected (Unsalted) Hashes: Even when passwords are stored as hashes, attackers can use precomputed rainbow tables to crack them if no unique “salt” value is added. Unsalted hashes lower the bar for credential theft dramatically.
Each of these pitfalls broadens the attack surface of SCADA environments. Addressing them requires a combination of robust configuration, secure software design, and vigilant operational practices.
Machine Learning: Predicting and Preventing Malware Attacks in the Cyber Supply Chain
So how do we get proactive against evolving threat actors in a supply chain context, rather than always cleaning up after the fact? Enter machine learning. By analyzing patterns and anomalies across vast amounts of supply chain telemetry—think network activity, vendor behaviors, download histories, and device communications—machine learning models can spot the subtle indicators of compromise that would slip right past legacy detection tools.
Let’s break that down:
- Behavioral Baselines: Machine learning algorithms first establish what “normal” looks like for your SCADA environment and suppliers. When something changes—say, a vendor starts communicating with new servers or an update package contains unexpected code—the model raises a flag faster than a human could ever hope to.
- Anomaly Detection: It excels at sniffing out unusual activity that may indicate a malware infection moving through the supply chain. Early detection means less time for attackers to move laterally or spread ransomware into critical operations.
- Real-Time Response: Rather than sifting through mountains of logs manually, automated systems powered by machine learning can recognize threats in real time, prioritize alerts, and even shut down suspicious connections to contain damage.
- Evolving with the Attackers: Machine learning keeps pace with attackers by learning from newly observed tactics. As threat actors invent novel malware or craft sophisticated phishing campaigns, the system adapts—there’s no stagnant rulebook to lag behind.
Ultimately, leveraging machine learning for predictive analytics means organizations don’t have to just react to breaches—they can anticipate and thwart attacks before they disrupt the supply chain or reach core SCADA operations.
Key Considerations for Cloud-Based IoT-SCADA: Safety, Bandwidth, and Latency
Moving SCADA to the cloud and embracing IoT connectivity brings a host of operational benefits—but also introduces new risks and technical hurdles that shouldn’t be overlooked.
Data Exposure and System Safety: Cloud-based SCADA inherently involves transmitting data across the internet. This raises concerns about data confidentiality, integrity, and unauthorized access. Sensitive control commands or operational info traveling over public or shared networks need strong encryption, robust authentication, and vigilant monitoring. Security missteps can quickly escalate from awkward to catastrophic when safety-critical systems are involved.
Bandwidth and Latency Challenges: SCADA operations hinge on rapid response times. Increased IoT device traffic and cloud dependence can create bandwidth bottlenecks or latency spikes, especially during high-load periods. Any delay—even milliseconds—in transmitting alarms or control signals could impact production flows or safety shutoffs.
System Optimization: To maintain performance and safety standards, it’s essential to invest in high-bandwidth, low-latency connectivity—think private leased lines, edge computing deployments, or optimized cloud regions tailored for industrial traffic. Load balancing, real-time monitoring, and redundancy planning are also must-haves to prevent slowdowns that lead to costly downtime.
Continuous Monitoring: Even with top-tier infrastructure, ongoing vigilance is non-negotiable. Routine assessments of network performance and failover capabilities help ensure that the system remains both secure and responsive—no matter how many devices join the party or where operators access the system from.
Ultimately, implementing IoT-SCADA in the cloud isn’t just a technical upgrade—it’s a strategic shift that demands a sharp eye on both safety and network performance trade-offs.
Real-World Attack Simulations and Protocol Coverage in SCADA Testbeds
To stay one step ahead of adversaries, researchers and defenders rely on specialized SCADA testbeds designed to replicate both the complexity and vulnerabilities of operational industrial environments. These testbeds come in all shapes and sizes—from small university labs to sprawling, multi-site networks—but their mission is the same: to safely simulate threats and evaluate how real-world attacks could unfold.
So, what exactly can these environments test?
Common Attack Scenarios Simulated in SCADA Testbeds
- Denial-of-Service (DoS) Attacks: Testbeds regularly stage DoS and DDoS scenarios to examine how control system components respond to intentional service interruptions—whether attackers are overwhelming network links or targeting field devices such as PLCs and RTUs.
- Man-in-the-Middle (MITM) Attacks: By intercepting and manipulating communications between devices, MITM attack simulations expose vulnerabilities in protocol implementations and help defenders test anomaly detection on critical data paths.
- Spoofing and Unauthorized Command Injection: These scenarios allow researchers to send malicious or fraudulent commands into the system, highlighting weaknesses in authentication and message integrity—think false actuation or tricking operators with bogus data.
- ARP and Protocol-Specific Attacks: Testbeds can simulate ARP spoofing to disrupt internal routing, as well as specialized attacks like malicious command injection within power grids or chemical plant simulations.
- Wireless and Remote Access Attacks: Given the rise in remote connections, environments increasingly include simulated attacks against wireless networks and VPN solutions, probing for weak access controls.
Protocols Commonly Tested
To simulate the wide array of threats found in the wild, SCADA testbeds support a mix of industrial protocols, including:
- Modbus TCP/IP
- DNP3
- IEC 61850
- OPC UA
- Profinet
- EtherNet/IP
- IEC 60870-5-103
- and even legacy serial connections.
Some advanced environments, such as virtualized or hybrid testbeds, balance cost with fidelity—allowing integration of real hardware (like Siemens or Allen-Bradley PLCs, ABB relays, or Schneider Electric HMIs) alongside network simulators such as OMNeT++ or GridLAB-D. This combination makes it possible to assess everything from reconnaissance and unauthorized access, to the physical disruption of processes, across various utility and manufacturing contexts.
Physical Process and Network Modeling
Beyond digital attacks, testbeds simulate physical industrial processes to evaluate how the impact of a cyberattack ripples from the screen to the shop floor. Whether it’s controlling the flow of power in a mock electrical grid, manipulating the behavior of a modeled chemical plant, or disrupting the integrity of a virtual water system, these simulations provide critical insight into both the cyber and kinetic consequences of an attack.
By leveraging these environments, defenders can test both common and cutting-edge attack techniques on the very protocols and devices powering modern industry—without risking actual infrastructure.
Reset Function Attacks: Disrupting Operations with a Single Command
One attack technique that’s caused major headaches for SCADA operators is the so-called “reset function attack.” Here’s how it works: many SCADA devices communicate over legacy protocols that lack proper authentication or encryption. An attacker who gains access—by sniffing network traffic or leveraging weak remote access controls—can craft a malicious command that tells a critical device to reset itself.
The fallout? When a device receives this bogus reset command, it’s essentially forced to reboot or temporarily shut down, taking essential control or monitoring functions offline. During this restart window, the process it controls could halt, alarms might go dark, and safety routines may be interrupted. Attackers often use replay or spoofing techniques, making their malicious reset look just like legitimate traffic—slipping under the radar of traditional defenses.
Real-world incidents have shown that even a short disruption can ripple out, causing downtime, lost revenue, and safety risks. This makes securing device communications—and monitoring for unexpected reset commands—a top priority for modern SCADA environments.
Memory Corruption: A Sneaky Route for Attackers
Another serious concern in SCADA data acquisition devices is memory corruption. This often stems from improper input validation within device software—think of vulnerabilities lurking in PLC (Programmable Logic Controller) editors. When these tools don’t securely handle the files or projects loaded into them, attackers can craft specially designed project files. Once opened, these malicious files can manipulate the editor’s memory, paving the way for unauthorized code execution—sometimes with the same privileges as the operator using the system.
This isn’t just a theoretical risk. Major vendors like Weintek, Siemens, and WAGO have all issued advisories addressing similar loopholes. With these vulnerabilities, attackers don’t need to find their way around the perimeter—they simply hitch a ride via a poisoned file, potentially gaining the ability to disrupt operations, steal sensitive data, or pivot deeper within the SCADA network.
Protecting against this means keeping PLC software updated, rigorously restricting which files can be loaded, and providing thorough user awareness training to spot the signs of malicious files before they’re ever opened.
How Poor Input Validation Opens the Door to XSS and SQL Injection in SCADA
One of the most persistent weaknesses putting SCADA environments at risk is the lack of rigorous input validation. Simply put, when SCADA hardware or software accepts data from users, interfaces, or other systems without carefully checking that data for legitimacy and safety, the stage is set for attackers to slip in malicious payloads.
Here’s how this plays out for two of the most notorious threats:
Cross-Site Scripting (XSS): If a SCADA web interface fails to properly sanitize user-provided input, attackers can inject malicious scripts straight into the system. This code might arrive via a cleverly crafted URL (reflected XSS) or be stored in the application itself (stored XSS), only to execute when an unsuspecting operator loads a compromised page. The consequences? Anything from hijacked user sessions and stolen credentials to unauthorized actions performed in the name of legitimate users. XSS isn’t just a website nuisance—it’s a real threat to the integrity of your operational technology when exploited in SCADA dashboards or HMIs (think: the infamous Wonderware InTouch exploits flagged by US-CERT).
SQL Injection: When input accepted by SCADA components is blindly fed into backend database queries, attackers get an opportunity to manipulate those queries to their own ends. By injecting specially crafted SQL commands, a threat actor could gain unauthorized access to sensitive operational data, alter configurations, or even disrupt system operations. This vector has been seen in products like Advantech WebAccess/SCADA, where the fallout ranges from data leaks to full-blown loss of control over the targeted environment.
The common denominator? Weak or absent input validation that lets harmful data travel unimpeded into critical systems. Robust validation and sanitization aren’t just good coding practices—they’re frontline defenses against attacks that can escalate from mere inconvenience to full-scale compromise.
Command Injection & OS Injection: Exploiting Trust in SCADA Systems
Two of the more insidious vulnerabilities lurking within SCADA environments are command injection and OS injection attacks. While they sound technical (and they are), understanding their basics can help you spot and defend against them.
Command Injection: At its core, command injection occurs when a system carelessly accepts and executes input from an untrusted source—often without proper validation. Picture a scenario where an attacker slips a malicious command into a user input field or a network request. If the SCADA software blindly incorporates this input into its own operating instructions, the attacker may gain unauthorized capabilities, potentially escalating their privileges or manipulating the system in unintended ways.
OS Injection: OS (Operating System) injection is closely related, but instead of general commands, attackers insert operating system-level instructions. This typically happens when devices like RTUs or PLCs, which often run specialized operating systems (think VxWorks, Microware OS-9, and the like), fail to filter user-provided data. A successfully exploited OS injection flaw allows an attacker to execute arbitrary commands directly on the device’s operating system—opening the door to remote code execution, complete system compromise, and, in severe cases, giving attackers a launchpad for further infiltration.
What makes these vulnerabilities especially dangerous in the SCADA context is that many industrial devices were designed in an era before cybersecurity was top-of-mind. Add to this the complexity of proprietary operating systems, and you get a perfect recipe for serious risk. In fact, the U.S. CERT has highlighted real-world incidents where attackers leveraged these weaknesses, demonstrating their very tangible impact on critical infrastructure.
IEC 60870: Security Considerations
As we wade deeper into the murky waters of SCADA protocol security, IEC 60870 deserves a spotlight. Widely adopted for remote control in power systems, this international standard enables communication between control centers and remote terminal units (RTUs) scattered across large geographical areas. It’s praised for its interoperability—meaning you can (in theory) get devices from different vendors to speak the same language, even if they’re from different corners of the globe.
But let’s talk about what keeps security professionals up at night. While IEC 60870 does provide some safeguards, like ensuring data integrity for messages transmitted between devices, it falls short in one crucial area: authentication. The protocol doesn’t include robust mechanisms to verify whether communication commands truly come from a trusted source. This lack of authentication in native implementations leaves the door cracked open for impersonation attacks, where a clever adversary could masquerade as a legitimate device or operator.
Other notable attributes:
- Timestamp Handling: While event timestamps can be created by RTUs to help organize activities in sequence, initial messages may be sent without a timestamp—leaving potential gaps for attackers to exploit.
- Multicast & Interoperability: Its design for broad scalability and vendor-agnostic communication is great for flexibility, but also increases the system’s attack surface.
Bottom line: IEC 60870 was built with reliable communication in mind, not modern cyber threats. Strengthening deployments with network segmentation, additional authentication layers, and vigilant monitoring is non-negotiable in today’s threat landscape.

Big Data Analytics: The Unsung Hero of IIoT Security
When it comes to safeguarding Industrial Internet of Things (IIoT) environments, big data analytics is an absolute game changer. Imagine trying to spot a needle in an endlessly growing digital haystack—IIoT sensors generate mountains of real-time data, from temperature readings to equipment status, all demanding constant vigilance. Traditional, manual monitoring simply can’t keep up.
Big data analytics steps in to make sense of this chaos. Advanced analytical tools sift through massive streams of IIoT data to highlight unusual patterns, flagging potential anomalies before they can spiral into full-blown incidents. This isn’t just about catching cyber threats, either—it’s about predicting equipment failures, optimizing performance, and minimizing downtime.
Organizations leveraging big data analytics benefit from:
- Real-time threat detection: Anomalies and suspicious activity are identified the moment they emerge, enabling rapid response and reducing risk.
- Improved operational efficiency: By analyzing historical and live data, companies can pinpoint inefficiencies, schedule predictive maintenance, and streamline workflows.
- Enhanced decision-making: With rich, contextual insights at their fingertips, teams can make smarter, faster decisions to protect both digital and physical assets.
In short, for modern SCADA and IIoT environments, big data analytics isn’t just a luxury—it’s a necessity, allowing defenders to stay one step ahead in an era where threats and data volumes both seem to grow by the day.
Machine Learning and the NSL-KDD Dataset: Analyzing Intrusion Detection Performance
The ever-evolving cyber threat landscape demands smarter defenses—and that’s where machine learning steps in. When it comes to intrusion detection, especially on benchmark datasets like NSL-KDD, researchers have put a host of machine learning algorithms to the test.
So, how do these methods perform? Classic approaches like decision trees, support vector machines (SVM), and random forests have all been evaluated for their ability to sift legitimate traffic from malicious behavior. Generally, ensemble techniques such as random forests tend to offer improved detection rates and lower false positives compared to single algorithms like naïve Bayes or k-nearest neighbors (KNN). Support vector machines frequently shine at spotting subtle, hard-to-detect attacks, though they can be resource-intensive. Decision trees stand out for their speed and interpretability—making them a favorite in industrial settings where quick, explainable decisions are crucial.
Of course, choosing the right technique is rarely straightforward. The effectiveness depends on factors like tuning, feature selection, and the specific attack types present in the data. Overall, blending multiple machine learning techniques, and fine-tuning them to the quirks of SCADA network traffic, yields the most robust intrusion detection—providing another essential layer in your cybersecurity arsenal.
Denial-of-Service Attacks: A Direct Threat to PLC Simulators
Another serious concern for SCADA security comes in the form of denial-of-service (DoS) attacks. In plain terms, a DoS attack overwhelms a target device or application with a flood of data or specifically crafted requests, causing it to crash or become unresponsive. For Programmable Logic Controller (PLC) simulators—those vital tools used to test and validate control system logic without touching live industrial equipment—a successful DoS attack can have outsized effects.
Imagine a scenario where an attacker identifies a vulnerability in a PLC simulator’s code, such as a limitation in buffer size. By sending network packets that exceed the expected limit, the attacker can exploit this weakness, causing the simulator to freeze or shut down entirely. This doesn’t just disrupt testing; it can delay system updates or mask other malicious activity within the network. Vulnerabilities like this have been highlighted by agencies such as CISA and are actively targeted in the wild, often by submitting oversized network packets to specific ports.
For organizations relying on PLC simulators to ensure system reliability and safety, a well-timed DoS attack could grind validation processes to a halt—potentially opening the door to larger, more damaging attacks.
The Problem with SCADA Security Datasets
So, where do things get tricky for defenders? Well, a recurring stumbling block is data—or, more specifically, the right kind of data. While there’s no shortage of vulnerability databases like the NVD and lists stacked with CVEs, they’re built with traditional IT systems in mind, not the unique quirks of SCADA environments.
For those testing intrusion detection systems (IDS) in industrial settings, standard benchmark datasets (think: the KDD99 or DARPA sets) are just not a snug fit. KDD99 is enormous—enough to strain your system’s resources if you work with the whole thing. In practice, analysts whittle it down to a mere fraction, but even then, they must contend with duplicate and redundant entries, muddying the waters for any machine learning effort. NSL-KDD improved things a bit, but it’s still largely geared toward enterprise IT, not pumps, turbines, or programmable logic controllers (PLCs).
On the flip side, datasets pulled from real water treatment or power distribution systems do exist but often come with their own baggage. Many haven’t been updated in years, failing to reflect today’s threat landscape or the rapid evolution of connected infrastructure. Plus, they tend to focus on narrow SCADA applications instead of the broader ecosystem: energy, manufacturing, water supply—you name it.
In short, security researchers are left piecing together partial views and outdated scenarios. For real progress, it’s essential to develop comprehensive, up-to-date datasets that mirror the diversity and complexity of modern SCADA systems across all sectors—so tools and defenses can be tested against the threats they’ll truly encounter in the wild.
How XSS Leads to Privilege Escalation in SCADA Web Interfaces
One particularly insidious threat SCADA operators must contend with is cross-site scripting (XSS) in their web applications—a vulnerability that can quickly spiral out of control if left unaddressed. When input fields in a SCADA web portal aren’t properly sanitized, attackers can slip in malicious scripts (the infamous XSS payload) that execute in the browsers of unsuspecting users.
What’s the real risk? An attacker who successfully plants such a script can hijack an active user session—for example, by stealing a valid session cookie. Once armed with this digital skeleton key, the adversary can impersonate a legitimate user, rapidly escalating their privileges inside the system. In practical terms, a well-placed XSS exploit could let an attacker leapfrog from basic access rights to controlling critical SCADA functions—potentially with the same authority as a plant operator or administrator.
It’s a classic case of a small crack opening the door to major consequences. That’s why robust input validation, regular security audits, and the least privilege principle are a must when web-facing SCADA components enter the mix.
Path Traversal Attacks: Unwanted Backdoors in RTUs
One vulnerability that keeps popping up in remote terminal units (RTUs) is path traversal. Imagine a nosy neighbor finding your spare house key by poking around, except instead of keys, we’re talking about sensitive files hidden deep within a device’s directory structure.
Path traversal typically happens when input—like a file path—isn’t properly checked or sanitized. Attackers can cleverly manipulate file requests using strings like ../../, tricking the RTU into granting access to directories and files way beyond what should be allowed. This not only reveals critical system files to the attacker but can also open the door to further privilege escalation.
With this access, an attacker in the know could potentially move from a low-privileged user to one with broader system control, putting critical industrial processes at risk. It’s a stark reminder that even a small coding oversight can become a gateway for serious mischief.
How Memory Buffer Issues Open the Door to Attacks
It’s easy to think of SCADA software bugs as obscure, esoteric weaknesses buried deep in the code. But sometimes, the most dangerous vulnerabilities are surprisingly simple—like when a program doesn’t keep a careful eye on the size of its own memory buffer. This classic oversight, often called “improper limitation of memory buffer,” is much more than a programming faux pas; it’s an open invitation for cyber attackers.
Here’s how these mistakes play out:
Buffer Overflow Mayhem: Imagine trying to pour a gallon of lemonade into a pint glass. If the software blindly shoves oversized data into a fixed-size buffer, anything that doesn’t fit spills over memory boundaries. This “overflow” lets attackers inject malicious code or manipulate files—think of it as rewriting the bartender’s recipe mid-pour. Real-world consequences? Remote code execution, file deletions, and sometimes, full system compromise.
Off-by-One Slip-ups: Another classic error is the notorious “off-by-one” mistake. Picture a program that’s supposed to check every locker in a row but accidentally checks one too many (or too few). In code, this means calculations that overstep array limits by a single element—just enough for attackers to sneak in bugs or trigger crashes, yet subtle enough to evade basic testing.
Both flaws often slip through the cracks, mostly due to rushed input validation or bad arithmetic, especially in the fast-changing world of SCADA deployments. The end result? Attackers gain a foothold where none should exist—at the structural core of the very tools designed to keep critical operations running safely.
How Insufficient Input Validation Opens the Door to SCADA Vulnerabilities
So, how does a seemingly “small” issue like not validating inputs spiral into full-blown digital chaos for SCADA systems? Think of it as leaving the front door unlocked and then being surprised when unexpected guests decide to throw a party in your living room.
When SCADA applications fail to rigorously check and sanitize the data they receive—whether from operators, connected devices like PLCs, or remote maintenance sessions—it’s open season for attackers. This single misstep can cascade into a flurry of vulnerabilities, often letting a cyber intruder take the reins with distressing ease.
Here are some common attack avenues paved by poor input validation:
- Path Traversal: Attackers can manipulate file paths (using tricks like
../) to gain access to sensitive files outside their intended directories. This lets them snoop or alter settings beyond their authorized scope. - Command & OS Injection: Malicious inputs can sneak in commands that the underlying SCADA software or even the device’s operating system unwittingly executes. That could mean anything from privilege escalation to complete system compromise—think of a simple maintenance input suddenly giving an attacker the same powers as an admin.
- Cross-Site Scripting (XSS): In scenarios where web-based SCADA dashboards are in play, unsanitized inputs let attackers inject rogue scripts that execute when a legitimate user browses a page. This enables session hijacking, data theft, or more insidious forms of manipulation—all without the victim’s knowledge.
- SQL Injection: SCADA software often talks to backend databases to track sensor readings, alarms, or events. Without proper validation, attackers can inject rogue SQL commands and siphon off sensitive data, alter records, or even disrupt real-time operations.
These vulnerabilities aren’t theoretical. Real-world incidents have exploited weak input handling in products from major vendors like Advantech and Wonderware, leading to remote code execution, data breaches, and worse.
The bottom line: robust input validation isn’t just good coding hygiene—it’s a foundational security pillar for SCADA environments. It’s the digital equivalent of locking every door and window before calling it a night. When neglected, attackers are all too happy to let themselves in.
Why SCADA-Specific Datasets Matter
Robust cybersecurity for industrial environments isn’t guesswork—it relies on high-fidelity data. When it comes to SCADA systems, traditional IT security datasets fall short. SCADA environments use unique protocols, architectures, and operational patterns unlike anything found in a typical corporate network. That means security tools and monitoring technologies need to learn from SCADA-specific traffic, not generic internet data dumps.
But here’s the rub: Real-world SCADA data is rarely available due to safety, privacy, and proprietary concerns. That’s where lab-built testbeds come in. These controlled environments simulate genuine SCADA operations, generating detailed, accurate datasets tailor-made for developing and validating defensive strategies. Without these specialized datasets, it’s nearly impossible to fine-tune intrusion detection systems, run realistic penetration tests, or create machine learning models that don’t drown in false positives.
In essence, the better and more realistic the dataset, the stronger our defenses will be against advanced threats targeting operational technology.
The Critical Role of Memory-Safe Programming Languages in SCADA
So, how can we better protect SCADA software at its most fundamental level? Enter memory-safe programming languages, such as Rust. Traditional SCADA applications have often been written in languages like C or C++, which, while powerful, are notorious for vulnerabilities like buffer overflows and memory corruption—prime real estate for attackers looking to escalate privileges or disrupt operations.
Memory-safe languages like Rust are specifically designed to sidestep these pitfalls. By enforcing strict rules around how memory is accessed and managed, they make entire classes of cyberattacks—think buffer overflows, use-after-free bugs, and dangling pointers—dramatically harder to pull off. For SCADA systems, which often operate for years without frequent updates and need utmost reliability, this reduced attack surface isn’t just convenient—it’s critical.
Even better, modern languages like Rust balance safety with performance, supporting high-speed, concurrent operations without sacrificing control. This makes them ideally suited for the unique challenges of SCADA: real-time requirements, efficiency, and the need for robust isolation between different processes.
In short, adopting memory-safe languages in future SCADA software development isn’t just a trend—it’s a proactive defense move, cutting off entire avenues for attackers before a single line of exploit code can even be written.
Privilege Escalation via CSRF: A Cautionary Example
One particularly sneaky threat vector is privilege escalation through cross-site request forgery (CSRF). Here’s how it plays out in SCADA environments: An attacker tricks a user—often someone with access to a PLC’s web interface—into clicking a malicious link or visiting a compromised website. Unbeknownst to the user, this action sends unauthorized commands to the SCADA device’s web server, taking full advantage of the user’s legitimate authentication.
If the device’s firmware lacks proper CSRF protection, the attacker may bypass authentication completely, planting commands or even altering settings on crucial equipment—all while the legitimate user is none the wiser. For example, older industrial controllers and PLCs without updated firmware have been found susceptible to these web-initiated attacks, as documented by cybersecurity advisories from groups like ICS-CERT.
The lesson? Regularly updating device firmware and ensuring web interfaces have robust CSRF protections isn’t just best practice—it’s a frontline defense against attackers eager for easy privilege escalation.
The Danger of Weak Password Policies
It might sound like cybersecurity 101, but weak password requirements remain one of the lowest-hanging fruits for attackers—especially in SCADA environments. When software fails to enforce strong, complex passwords, it hands adversaries an open invitation to escalate privileges and gain unauthorized access.
The implications? Once inside, attackers can move laterally throughout the system, potentially seizing control of critical operations or exfiltrating sensitive data. Weak passwords are child’s play for everything from brute-force attempts by opportunistic hackers to automated credential stuffing—tools that nation-state actors and cybercriminal groups wield with alarming efficiency.
The lesson here: Even the most advanced technical safeguards can be undermined by something as simple as a poor password policy. Robust password controls, multi-factor authentication, and regular credential audits are essential first steps toward hardening SCADA defenses.
Demystifying Path Traversal: A Sneaky Input Validation Flaw
Path traversal is a classic—but still highly effective—attack that thrives on sloppy input validation, and it’s a growing concern for SCADA environments coming online. Here’s how it works: an attacker manipulates file paths (think sequences like ../../etc/passwd) to break out of an application’s intended directory structure. The goal? To access sensitive files or directories outside the permitted scope, sometimes reaching critical configuration files or operational data.
In SCADA systems, this vulnerability often emerges when user-supplied input isn’t rigorously checked before being passed to underlying file system commands. Attackers can exploit weak validation by sneaking in sequences like ../ (or more creative variations) to fool the system into serving files it never intended to share. It’s not uncommon for poorly implemented controls to stop at the first suspicious pattern, allowing more complex combinations to slip by unnoticed—an Achilles’ heel documented in vulnerabilities like CWE-20 (Improper Input Validation) and CWE-22 (Improper Limitation of a Pathname to a Restricted Directory).
Why is this especially dangerous in industrial contexts? Because what might start as an attempt to browse unauthorized logs could escalate to unauthorized modifications of controller logic, access to field device configurations, or even exposure of credentials. In short: unchecked input fields may become a fast lane for attackers straight into the operational heart of your SCADA deployment.
Critical Vulnerabilities in Industrial RTOS Like VxWorks
When it comes to real-time operating systems (RTOS) such as VxWorks—an industry staple powering everything from factory floor controllers to smart grid infrastructure—several classes of vulnerabilities regularly top the list of security headaches for ICS operators:
- Remote Code Execution Flaws: Attackers often exploit issues in how the RTOS handles network communications, sometimes enabling them to execute malicious code remotely with little or no authentication.
- Weak Authentication and Default Credentials: Many deployments still rely on out-of-the-box credentials or lack proper authentication altogether, giving attackers easy access if they know where to look.
- Stack-Based Buffer Overflows and Memory Corruption: Poor input validation can allow attackers to trigger stack overflows, memory leaks, or data corruption, potentially leading to system crashes or remote takeover.
- Insecure Network Services: Many VxWorks-based devices expose legacy or unnecessary network services, some with known vulnerabilities that have persisted for years, such as outdated FTP, Telnet, or proprietary management interfaces.
- Patch Management Challenges: Because these systems often run continuously in critical environments, patching lags behind, leaving publicly disclosed vulnerabilities open for months or even years.
- Vulnerabilities in Protocol Parsing: Built-in support for various industrial protocols (e.g., Modbus, DNP3) means flaws in protocol parsing routines can be a pathway for attackers to slip past defenses without raising alarms.
Bottom line: a single exploited flaw can provide deep access into operational environments. Asset visibility, rigorous patching, and network segmentation are must-haves when dealing with RTOS in the wild.
Essential SCADA Cyber Monitoring Tools
No single tool is a silver bullet. Effective SCADA monitoring relies on a layered security approach, utilizing a combination of specialized and traditional cybersecurity tools:
Network Intrusion Detection/Prevention Systems (IDS/IPS): These are fundamental for monitoring network traffic for malicious activity or policy violations. For SCADA, IDS/IPS solutions often require deep packet inspection capabilities that understand industrial protocols (e.g., Modbus, DNP3, IEC 61850). Widely used open-source tools like Snort and Suricata exemplify this approach, offering robust detection engines that can be customized for industrial environments. These systems analyze traffic in real time, flagging suspicious behaviors or unauthorized commands that could indicate an attack.
In addition to real-time network monitoring, integrity verification solutions such as Tripwire can further strengthen defenses by continuously checking for unauthorized system or configuration changes—an essential layer in environments where uptime and reliability are paramount.
Finally, staying informed about emerging threats and vulnerabilities is crucial. Resources provided by organizations like US-CERT offer timely advisories and best practices, helping security teams adapt their IDS/IPS configurations to address the latest risks.
By combining protocol-aware detection, file integrity monitoring, and up-to-date threat intelligence, organizations can build a resilient foundation for SCADA security.
Enhancing Intrusion Detection for SCADA Networks
Out-of-the-box IDS solutions—whether open-source favorites like Suricata or commercial options—aren’t always ready for the unique quirks of SCADA networks. To make them truly effective in these environments, a little customization is in order.
Key enhancements include:
- Industrial Protocol Support: Standard IDS engines often struggle with specialized industrial protocols like Modbus, DNP3, and IEC 60870-5-104. Tuning or extending your IDS with deep protocol awareness is crucial, enabling more accurate detection of abnormal or malicious control system commands.
- Environment-Specific Rule Sets: Crafting or importing SCADA-specific detection rules can help catch everything from unauthorized commands to subtle process anomalies. Many community and vendor-supported rule packs now cater specifically to industrial threats, closing gaps mainstream signatures miss.
- Whitelisting & Anomaly Detection: Because legitimate SCADA operations are often highly predictable, supplementing signature-based detection with behavioral baselines and whitelisting known-good commands can dramatically reduce false positives and highlight genuinely suspicious activity.
- Integration with SCADA Monitoring Tools: Plugging your IDS into broader SCADA threat monitoring platforms or SIEM solutions allows for better correlation, quicker investigations, and a holistic view of incidents across IT and OT boundaries.
By tailoring your IDS to the SCADA context, you get a security sentinel that understands not just the “what” of network traffic, but the “why”—greatly improving resilience in the face of evolving industrial cyber threats.
How DTL Algorithms Are Enhancing IDS Performance
Recent advancements in deep transfer learning (DTL) have noticeably elevated the effectiveness of intrusion detection systems, especially in the nuanced realm of SCADA environments. By leveraging DTL, IDS solutions can now better recognize both known and previously unseen attack patterns, improving both detection accuracy and speed.
Some of the key gains include:
- Improved Threat Recognition: DTL models can learn from diverse datasets, making them adept at spotting subtle anomalies across various industrial protocols. This expanded “threat vocabulary” means fewer false negatives and more reliable early warning.
- Adaptability to Evolving Attacks: Transfer learning enables these algorithms to quickly adapt to new or emerging threats—even with limited OT-specific data—by building on knowledge from related domains.
- Reduced Need for Huge Labeled Datasets: Traditional machine learning approaches often struggle due to the lack of extensive, labeled attack data in OT settings. DTL mitigates this by applying insights gained from IT environments or simulated attack scenarios, shrinking the gap between theory and operational reality.
This convergence of improved accuracy, flexibility, and data efficiency makes DTL-based IDS a promising tool in the ongoing arms race against increasingly sophisticated threat actors.
Key Components of Effective SCADA Intrusion Detection
When it comes to evaluating SCADA Intrusion Detection Systems (IDS), it’s not just about checking boxes—it’s about ensuring your defenses are fit for the specialized challenges of industrial environments. Here are the core modules typically involved, along with the critical features you’ll want to prioritize:
Data Collection and Analysis: The foundation of any IDS is its ability to reliably gather data, whether from network traffic or directly from endpoint devices. For SCADA, both network-based and host-based data acquisition are essential, given the diversity of protocols and devices at play.
Feature Extraction: Simply collecting data isn’t enough. The IDS needs to parse and distill key behaviors and patterns, often translating raw traffic into actionable indicators specific to industrial systems.
Detection and Classification: This is where the magic (or math) happens. Many modern IDS solutions leverage machine learning or heuristic algorithms to accurately distinguish between benign activities and actual threats—including new and unknown (zero-day) attack types.
Real-Time Alerting: Speed matters. Timely alerts ensure that suspicious activities can be quickly investigated before damage is done, making the ability to detect and respond to live attacks absolutely non-negotiable.
Performance Impact: Let’s face it—an IDS that grinds your critical systems to a halt is a problem, not a solution. It’s vital to ensure that deployment minimizes performance impact on your operational processes.
Management at Scale: Industrial organizations often span sprawling networks and countless devices. Your IDS should provide centralized management capabilities, making it practical to monitor and update protection across a wide environment.
Encrypted Traffic Inspection: With more SCADA communications adopting encryption, the ability to analyze secured traffic without crippling visibility is increasingly important.
A robust SCADA IDS is measured by how well it brings together these essential modules and features, ensuring security without sacrificing operational reliability.
Decoding DTL-Based IDS Approaches: Key Categories Explained
When it comes to SCADA cybersecurity, Deep Transfer Learning (DTL)-based Intrusion Detection Systems (IDS) are gaining real traction. But just like choosing the right wrench for the job, it’s important to understand which type of DTL-based IDS fits your unique environment.
Here’s a quick rundown of the main DTL-based IDS categories and what sets them apart:
Domain Adaptation Approaches: These methods are designed to bridge the gap between different network environments—think adapting a model trained on a corporate IT network to detect attacks in an OT plant floor. Techniques include feature-based, instance-based, and parameter-based adaptation.
Adversarial-Based DTL: Leveraging concepts similar to Generative Adversarial Networks (GANs), this approach focuses on improving detection in the face of evolving threats, making it tougher for adversaries to bypass defenses.
Multi-Source Transfer Learning: Instead of pulling knowledge from just one source domain, these systems combine patterns from multiple environments to boost accuracy. This is particularly handy for organizations with diverse network setups that don’t fit neatly in one category.
Ensemble DTL Methods: Like assembling a cybersecurity “super team,” these combine outputs from multiple DTL models—each specializing in detecting different attack types—for more robust overall protection.
Each of these subcategories comes with its own strengths and best-use scenarios, whether you need to spot never-before-seen threats or ensure adaptability as your SCADA ecosystem evolves.
With this arsenal, you’re better equipped to navigate the ever-changing threat landscape—and stay one step ahead of the adversaries trying to outsmart your critical infrastructure.
Security Information and Event Management (SIEM): SIEM systems aggregate and correlate log data from various sources across the IT and OT environments. This provides a centralized view for security analysts to detect patterns indicative of an attack. Tailoring SIEM use cases for OT-specific threats is crucial.
Asset Discovery and Inventory Tools: You can’t protect what you don’t know you have. Specialized OT asset discovery tools can identify and map all connected devices, including PLCs, RTUs, and HMIs, providing crucial visibility into the SCADA environment.
Building a thorough asset inventory means documenting not only the existence of devices, but also their configurations, software versions, firmware, and physical or logical network locations. This comprehensive approach is essential to track authorized versus unauthorized devices and to maintain a security baseline.
Active vs. Passive Discovery:
While active methods—like network scans using TCP SYN or ACK—can be effective in traditional IT environments, they may disrupt sensitive SCADA systems by generating unnecessary traffic. Instead, passive discovery techniques are often preferred in control system networks. These non-intrusive methods, such as analyzing MAC-ARP tables or utilizing DNS and ICS-specific monitoring tools, allow you to observe the devices communicating on your network without interrupting critical processes.In short, a well-maintained, passively gathered asset inventory is foundational for both operational efficiency and robust OT security.
Vulnerability Scanners: Regular vulnerability scanning helps identify known weaknesses in SCADA components and software. However, scanning in OT environments must be approached cautiously to avoid disrupting sensitive processes. Many organizations opt for passive scanning techniques or conduct scans during planned maintenance windows.
It’s also crucial to recognize that common vulnerabilities in SCADA systems often stem from improper access controls and weak encryption practices. For instance, default password configurations and poor credential management can leave critical databases, like historians, exposed—making information disclosure to unauthorized actors much easier. Similarly, certain PLCs may be susceptible to attacks where unauthenticated packets can trigger information leaks or even unauthorized modifications to ladder logic. High-privilege adversaries might also intercept traffic between master and field devices, potentially exposing or tampering with sensitive operational data.
This underscores why vulnerability management in SCADA isn’t just about running scans—it’s about understanding the unique risks in your environment, prioritizing remediation, and ensuring robust access controls and encrypted communications wherever possible.
- Leveraging the National Vulnerability Database (NVD) for SCADA Security:
The serves as a comprehensive resource cataloging known vulnerabilities affecting a wide range of technologies—including many in the industrial control systems (ICS) and SCADA world. Relevant entries include critical weaknesses in commonly used protocols (such as Modbus and DNP3), PLC firmware flaws, and authentication bypasses in popular remote terminal units (RTUs) and HMIs.
Some examples of SCADA-related vulnerabilities found in the NVD include:
- Weak default credentials or lack of authentication in devices from major ICS vendors.
- Unpatched code execution bugs in programmable logic controllers (PLCs).
- Input validation issues in SCADA software, potentially allowing remote attackers to manipulate control settings.
- Protocol implementation vulnerabilities leading to denial-of-service or data leakage.
Regularly reviewing the NVD—and subscribing to vendor security alerts—helps organizations stay ahead of exploitable weaknesses. Implementing timely patches and mitigating controls based on this intelligence is vital for robust SCADA cybersecurity.
- Anomaly Detection Platforms: These tools establish a baseline of normal network and system behavior and then alert on deviations. In SCADA environments, this can be highly effective in detecting novel or zero-day attacks that signature-based tools might miss. Machine learning is increasingly powering these platforms. By analyzing historical data, machine learning algorithms can help establish nuanced baselines of “normal” activity and flag deviations that may indicate suspicious behavior. Techniques such as support vector machines (SVMs) are used to distinguish between normal and anomalous network traffic, maximizing detection accuracy while minimizing false positives. K-nearest neighbor (KNN) algorithms can classify new events based on similarities to previously observed data, though they’re typically best suited for smaller datasets due to computational complexity. Linear regression models may also be employed to predict system values based on trends, helping to anticipate abnormal shifts before they escalate into incidents. The integration of these advanced analytics allows anomaly detection platforms to adapt to evolving threats—often catching novel or zero-day attacks that signature-based tools would overlook.
Hidden Markov Models for Water Supply Anomaly Detection
Hidden Markov Models (HMMs) have carved out a practical niche in the world of anomaly detection—especially for water supply systems where normal operations produce complex, ever-changing data patterns. Here’s how it works: HMMs learn how system measurements (like flow rates, pressure readings, or chemical values) typically fluctuate during regular operations by analyzing historical data.
Once the HMM understands these “normal” patterns, it can continuously compare live data streams against its learned model. If something strays too far from the expected—say, a sudden drop in pressure that doesn’t fit any known scenario—the HMM raises a red flag. This is particularly valuable for spotting both slow-building leaks and abrupt failures before they escalate.
Using HMMs yields a few important benefits:
- Early Threat Detection: By modeling normal behavior, unusual trends can be flagged before they become critical.
- Reduced False Positives: Since the HMM adapts to the actual rhythms of your system, it’s less likely to generate noise over routine fluctuations.
- Broad Application: HMMs can be trained for different subsystems—treatment plants, distribution pipes, pump stations—making them flexible for varied SCADA landscapes.
Combined with other monitoring strategies, HMM-based anomaly detection enhances the resilience and security of water supply infrastructure, catching threats that signature-based systems might miss.
Anomaly Detection for Load Forecasting During Cyberattacks
Machine learning-driven anomaly detection platforms are particularly valuable in the context of load forecasting—especially when cyberattacks are in play. These technologies work by learning what “normal” load patterns look like across your SCADA environment, factoring in historic usage data, typical seasonal variations, and the unique behaviors of your industrial assets.
When attackers try to manipulate sensor readings or inject false data to disrupt load forecasts, anomaly detection tools spring into action. By constantly comparing current network and device activities against their baseline models, these platforms can quickly flag unusual changes—whether it’s a sudden spike in energy demand or inexplicable drops—prompting further investigation.
- Detecting Malicious Data Manipulation: If a cyberattacker attempts to alter load data (for instance, inflating numbers to trigger operational inefficiencies), anomaly detection algorithms identify these discrepancies and generate alerts before any real harm occurs.
- Automated Response: Advanced solutions not only spot the anomalies but can also trigger automated workflows—such as isolating compromised devices or rolling back to a safe state—to limit the impact.
- Continuous Learning: Many modern platforms continually refine their models using the latest data, helping organizations adapt to evolving attack tactics while maintaining accurate load forecasts.
In short, the integration of anomaly detection in load forecasting adds an essential layer of resilience, ensuring that even if attackers attempt to disrupt operations, their efforts are met with swift detection and response.
Endpoint Detection and Response (EDR) for OT: While traditional EDR is common in IT, solutions tailored for OT endpoints (like engineering workstations and HMIs) are emerging, providing better visibility and response capabilities for these critical assets.
Host-Based Intrusion Detection (HIDS): HIDS operates directly on hosts within the OT environment—such as HMIs or engineering workstations—to monitor logs, track file system changes, and flag suspicious activity in real time. This can be particularly valuable in OT, where patching systems may be challenging and visibility into endpoint behavior is limited. File integrity management tools, like Tripwire or OSSEC, help detect unauthorized changes to system files and registries, which can be crucial for uncovering stealthy threats and zero-day attacks. For instance, robust file integrity monitoring could have identified malware such as Stuxnet much sooner, highlighting its importance in OT security.
Memory Dump Analysis: Analyzing both volatile and non-volatile memory on devices like PLCs can reveal hidden malware and advanced attacks that evade traditional detection. Techniques such as memory extraction via communication protocols (using function codes) or hardware-level access (e.g., JTAG) allow investigators to capture critical forensic artifacts—like variable content, device logs, and application code—from PLCs. However, these methods come with limitations: device architecture may restrict data acquisition, JTAG access can be disabled by manufacturers, and real-time memory analysis remains a challenge due to operational constraints. Despite these hurdles, memory dump analysis remains a valuable tool for detecting sophisticated threats, provided the device design permits such access.
Together, these approaches enhance the ability to detect, investigate, and respond to threats on OT endpoints—especially in environments where traditional IT security tools fall short.
- Industrial Firewalls: These are designed to segment SCADA networks, control traffic flow between zones, and understand industrial protocols to enforce security policies with greater granularity than traditional IT firewalls.

Taxonomies of SCADA Vulnerabilities
Understanding and classifying vulnerabilities is essential for navigating the complex risk landscape in SCADA environments. Over the years, several taxonomies have been proposed to help security professionals and engineers systematically assess threats and weaknesses unique to industrial control systems.
- SCADA-Specific Vulnerability Taxonomies: Researchers and organizations have developed frameworks that categorize vulnerabilities according to their nature, such as those affecting network services, human-machine interfaces, or control logic. For example, vulnerabilities may be sorted by origin (hardware, software, or configuration), affected protocol (like Modbus, DNP3), or impact (disruption, data loss, unauthorized control).
- Supervised Learning and IDS Taxonomies: As machine learning has become more prevalent in industrial security, specialized taxonomies now exist focusing on supervised learning techniques for intrusion detection systems in SCADA environments. These categorize vulnerabilities based on attack vectors, detection methods, and the types of anomalies commonly encountered in process networks.
- Cross-Domain Attack Frameworks: Broader frameworks also examine how vulnerabilities in one domain (such as corporate IT) can lead to cascading effects in SCADA systems. These taxonomies help map the potential for cross-domain attacks, illuminating the interplay between cyber threats and physical processes.
- Attack Taxonomies: Several academic efforts have classified cyber attacks on SCADA systems by their tactics, targets, and consequences, such as reconnaissance, denial of service, or manipulation of process data. These models provide insight into attacker goals and preferred pathways, supporting both defense planning and incident response.
Leveraging these various taxonomies is invaluable for designing comprehensive risk assessments and for informing ongoing monitoring strategies. Proper classification ensures no vulnerability hides in plain sight, and remediation efforts are prioritized where they matter most.
Multi-Attribute Intrusion Detection for Power Network SCADA
Bringing intelligent monitoring a step further, multi-attribute intrusion detection systems (IDS) offer a tailored way to catch threats that are unique to power network SCADA systems. Rather than leaning solely on one type of indicator (like unusual network traffic), these systems combine data from multiple sources—think device behavior, protocol anomalies, and user activity patterns—all at once.
Here’s how these SCADA-specific IDS approaches offer a sharper line of defense:
- Contextual Awareness: By understanding normal behaviors for each device and protocol (for instance, a PLC using Modbus or DNP3), the IDS can separate actual threats from harmless quirks that generic systems might misinterpret.
- Layered Analysis: Multi-attribute systems cross-correlate network traffic, command sequences, and even timing patterns. This helps them detect sophisticated threats designed to skirt basic, one-dimensional monitoring.
- Reduced False Positives: Since the system weighs several factors before raising an alert, operational teams face fewer wild goose chases, which makes defense both faster and more focused.
- Custom Policy Enforcement: Security teams can define what “normal” looks like at different layers of the power system, ranging from substations to operator workstations, creating bespoke rules that reflect the real-world diversity of a SCADA environment.
By harnessing these multiple angles, a well-tuned SCADA IDS gives operators an early heads-up on insider misuse, zero-day threats, or malicious outsiders—without crying wolf every time something changes.
Defending SCADA Energy Management Systems from DDoS Attacks
Distributed Denial of Service (DDoS) attacks pose a unique challenge for SCADA energy management systems, threatening both uptime and operational safety. One proven approach to mitigating these attacks involves implementing token-based verification mechanisms. By requiring each request to carry a validated token, the system can quickly filter out illegitimate or malicious traffic before it has a chance to overwhelm core services.
This method works particularly well alongside:
- Rate limiting: Restricting the number of requests any single client can make within a given timeframe prevents resource exhaustion.
- Network segmentation: Isolating critical energy management components from less-trusted segments helps contain potential impacts.
- Specialized DDoS mitigation appliances: Deploying devices or cloud-based services from trusted providers like Cloudflare or Radware offers scalable protection by deflecting or absorbing attack traffic upstream.
- Continuous monitoring: Real-time traffic analysis can spot and respond to abnormal spikes rapidly, ensuring disruptions are detected before they escalate.
Used together, these strategies help create robust defenses, minimizing the risk that a DDoS attack can bring energy operations grinding to a halt.
Supervised Learning Techniques in SCADA Intrusion Detection
Among the arsenal of tools protecting SCADA networks, supervised learning has emerged as a smart, modern approach to intrusion detection. Rather than relying solely on signature-based systems (which are only as good as their knowledge of known attacks), supervised learning techniques use labeled data to train detection models to recognize both typical activity and a variety of attack scenarios.
Here’s how it works in a nutshell:
- Labeled Data Collection: Historical data containing examples of normal operations and assorted attack patterns (like malware, unauthorized control commands, or abnormal network behaviors) is carefully curated.
- Training the Model: The supervised learning algorithm—think of favorites like Random Forests, Support Vector Machines, and Neural Networks—learns to distinguish between benign and malicious traffic by analyzing this labeled dataset.
- Detection in Real Time: Once trained, these models monitor live network traffic and system logs, flagging data that matches behaviors learned during training. Because the system “knows” what attacks look like, it can identify even subtle threats.
- Continuous Improvement: As new attacks are discovered, the models are updated with fresh data. This keeps SCADA intrusion detection systems evolving right alongside the threat landscape.
The greatest strength? Supervised learning allows the IDS to spot threats that might evade traditional, rule-based tools, adding another intelligent layer to the defense of critical infrastructure.
Comparing SCADA Cybersecurity Standards
When it comes to securing SCADA systems, a maze of standards exists—each with its own philosophy, strengths, and blind spots. Broadly, these standards can be grouped into international frameworks (like IEC 62443 and ISO/IEC 27001), industry-specific guidelines (such as NERC CIP for energy), and vendor-driven best practices.
IEC 62443: Widely hailed as the gold standard for industrial automation, IEC 62443 offers a comprehensive, risk-based approach. It’s modular, emphasizing both technical controls (like network segmentation and access management) and organizational policies (such as security training). Its biggest advantage is flexibility: organizations can tailor controls to their environment’s unique risk profile.
NERC CIP: Targeted mostly at North American power utilities, NERC’s Critical Infrastructure Protection standards are more prescriptive—detailing exactly what regulated entities must do to protect the power grid. They focus heavily on access controls, auditing, and change management, but can sometimes lag behind newer threats or technologies.
ISO/IEC 27001: This is a general information security management standard—not specific to SCADA, but often used to demonstrate overall cybersecurity maturity. Implementing ISO/IEC 27001 provides a robust governance structure, though additional OT-specific controls are usually needed to cover SCADA’s unique needs.
Ultimately, no standard is a panacea. The most resilient SCADA environments cherry-pick controls from multiple frameworks, aligning them with site-specific risks and regulatory obligations. Regular gap analyses against these standards can reveal overlooked weaknesses and drive continuous improvement.
Anomaly-Based Intelligent Intrusion Detection Systems for Industrial Control
Among the growing arsenal of security solutions for SCADA and other industrial control environments, anomaly-based intelligent intrusion detection systems (IDS) deserve special mention. These platforms don’t rely solely on static threat signatures—rather, they use advanced algorithms and machine learning to learn what “normal” looks like across the network. When something unexpected happens, such as traffic patterns that fall outside established baselines or unusual commands sent to controllers, the system raises an alert for further investigation.
An example: specialized IDS solutions for OT environments, like those designed for protocols such as Modbus or DNP3, can detect subtle deviations in traffic or operational behavior. Some modern platforms have even introduced artificial intelligence to continuously adapt their understanding of “normal”—meaning they can spot previously unseen attack methods or rogue devices as soon as they appear. These intelligent systems are particularly effective in environments where traditional, signature-based tools would struggle, offering a critical early warning against zero-day threats, unauthorized changes, or stealthy movements within the control network.
Model-Based Intrusion Detection in SCADA and Smart Grids
Model-based intrusion detection brings a uniquely adaptive defense to SCADA systems and smart grids. Unlike traditional signature-based tools, these solutions build mathematical or behavioral models of how devices, protocols, and processes SHOULD operate under normal, “healthy” conditions.
Here’s how it works in practice:
- Baseline Behavior Modeling: The system first observes regular patterns of communications and actions across SCADA devices (like PLCs, HMIs, RTUs) or smart grid controllers, creating a high-fidelity “normal operations” profile.
- Continuous Monitoring: Once the baseline is set, real-time network and device activity are compared against expected behaviors. Model-based systems excel in spotting even subtle anomalies—a command sequence out of order, an unusual data payload, or timing changes that don’t fit the usual rhythm.
- Detection of Novel Attacks: Since this approach assesses behavior rather than looking for known threat signatures, it’s particularly effective at uncovering zero-day attacks or sophisticated adversaries attempting to bypass traditional defenses.
- Automated Response and Forensics: Advanced model-based platforms can not only alert operators to deviations but may also trigger automated responses, like isolating affected systems, and provide forensic data to aid incident investigations.
In essence, model-based intrusion detection acts as a vigilant guardian—constantly cross-referencing live activity with established norms, so operators receive rapid, precise alerts to both known and previously unseen threats across their critical infrastructure.
Edge-Based Multi-Level Anomaly Detection for SCADA Networks
Edge-based multi-level anomaly detection is an innovative approach that helps address the unique visibility and response challenges in SCADA environments. Here’s how it works in practice:
- Distributed Detection at the Edge: Instead of sending all data to a central server for analysis, anomaly detection logic is deployed directly on edge devices such as remote terminal units (RTUs) or local gateways. This ensures real-time monitoring closer to the source of data and minimizes response times.
- Layered Analysis: The process typically involves multiple layers of detection. Basic checks (like protocol compliance or threshold violations) are handled immediately at the device, flagging obvious anomalies. More sophisticated analysis—such as cross-device correlation or machine learning-based detection—can be layered on top, often at centralized aggregation points or dedicated monitoring nodes.
- Resource Efficiency: By filtering out known-good or benign activity at the edge, this method reduces network bandwidth usage and lowers the load on central monitoring systems. Only pertinent alerts or suspicious events are forwarded, making it easier for security teams to focus on real issues.
- Scalability and Resilience: The distributed nature of this setup fits large or geographically dispersed SCADA deployments, providing resilience even if some network segments are isolated. Local detection continues to operate independently until connectivity is restored.
- Rapid Response: With detection and even initial triage happening at the edge, incident response can begin immediately—critical for operational technology environments where time is often of the essence.
This multi-tiered approach enables security teams to catch threats faster, filter out noise, and maintain system performance without sacrificing visibility.
How Vulnerabilities in Industrial Automation Software Are Identified and Disclosed
Detecting and addressing vulnerabilities in the SCADA and broader industrial control system (ICS) landscape is a collaborative and ongoing process. Here’s how it typically unfolds:
Research and Responsible Disclosure: Security researchers, vendors, or asset owners may discover vulnerabilities during routine assessments, penetration testing, or via bug bounty programs. Once identified, the responsible party generally notifies the vendor or affected organization privately, giving them an opportunity to address the issue before publicizing details.
Vendor Response and Patching: After notification, the vendor investigates, develops, and tests a patch or mitigation—balancing the need for security with the operational realities of industrial environments (where patching is rarely as simple as a quick software update).
Advisory Publication: When a fix or mitigation is available, organizations such as CISA, US-CERT, and ICS-CERT publish detailed advisories to inform the wider community. These advisories typically outline impacted products, potential attack methods, and recommended mitigations, arming asset owners with the information needed to protect their systems.
Ongoing Collaboration: Disclosure doesn’t end at publication. Ongoing monitoring, industry information-sharing forums (like ISACs), and feedback loops between vendors, asset owners, and researchers help ensure vulnerabilities are addressed comprehensively and that lessons learned inform future risk management.
This coordinated approach encourages transparency while minimizing exposure, ultimately strengthening the security posture of critical infrastructure.
Understanding CVE and CWE in SCADA Security
When it comes to defending SCADA environments, industry standards like CVE (Common Vulnerabilities and Exposures) and CWE (Common Weakness Enumeration) play an essential role. But what do these acronyms mean for the day-to-day safety of your control systems?
At its core, the CVE system functions like a global dictionary for publicly known cybersecurity vulnerabilities. Each CVE identifier provides a standardized reference for specific security flaws—think of it as a unique fingerprint for every bug, from input validation misses to privilege misconfigurations. Security teams, vendors, and asset owners rely on this common language to assess which vulnerabilities affect their SCADA assets, track new threats as they’re disclosed, and prioritize patching efforts where they matter most.
CWE, on the other hand, goes a level deeper. While CVEs catalog individual vulnerabilities, CWE classifies the underlying types of software weaknesses that frequently show up in industrial systems. Examples include improper input validation, flaws in access controls, or path traversal issues. Understanding common weakness patterns helps SCADA defenders recognize risky coding practices and proactively address classes of vulnerabilities before they’re weaponized in the wild.
Why does this matter in an industrial context?
- Prioritization: CVE lists let industrial operators quickly identify which known vulnerabilities put their SCADA networks at risk, so they can deploy mitigations or updates in a targeted manner.
- Systematic Defense: By mapping your assets and software against CWE-listed weaknesses, your teams can shore up known weak points—reducing the odds of repeat issues across multiple systems or vendors.
- Benchmarking and Compliance: Regulatory frameworks and auditors often reference CVE and CWE when evaluating the security posture of OT networks. Keeping up with these standards is key to demonstrating robust, industry-compliant defenses.
In short, both CVE and CWE empower organizations to turn the flood of vulnerability data into meaningful, actionable intelligence—an absolute must for any modern SCADA security program.
The State of Intrusion Prevention and Prediction Research in SCADA
While intrusion detection has seen considerable advancement within SCADA security, the areas of intrusion prevention and attack prediction are still emerging frontiers. There’s a notable gap when it comes to tools that not only detect ongoing attacks but also anticipate and prevent future threats before they take hold.
Recent academic and industry attention has turned to leveraging machine learning for this predictive capability. Techniques such as Support Vector Machines (SVM), random forest classifiers, regression analysis, and Naive Bayes models have shown promise in forecasting potential attacks. Notably, ensemble methods like random forest have yielded some of the best predictive results, particularly for identifying reconnaissance activities—the early, probing stages of an attack.
However, these machine learning-driven approaches are not one-size-fits-all. Their effectiveness tends to be limited to certain types of cyber threats and might not generalize seamlessly across every SCADA deployment. More real-world testing, especially outside of controlled environments, is needed to confirm whether these methods can reliably prevent attacks on critical infrastructure at scale.
Ultimately, while progress is being made, robust and practical solutions for predictive intrusion prevention in SCADA systems are still in development. Organizations looking to stay ahead of adversaries should continue to monitor advances in this area—and, where possible, test emerging machine learning tools within their own unique environments.
Key Frameworks for SCADA Simulations and Security Testbeds
Establishing a realistic environment for SCADA cybersecurity research and operator training isn’t as simple as spinning up a virtual machine. Comprehensive frameworks and testbeds have been developed to mirror the complex behaviors and communication protocols of actual industrial control systems.
A few notable approaches include:
Custom Security Testbeds: Purpose-built SCADA security testbeds provide a controlled “sandbox” where analysts can safely simulate attacks, experiment with new detection tools, and evaluate incident response plans. These testbeds typically replicate OT components such as PLCs, RTUs, HMIs, and network infrastructure, often using a combination of physical hardware and virtualized devices. Researchers can launch targeted scenarios to assess their defense-in-depth controls—without risking production assets.
Simulation Frameworks: Software-based frameworks for SCADA simulation (e.g., open-source or academic platforms) enable organizations and researchers to model industrial networks, communications, and malicious behaviors at scale. These platforms can emulate normal and adversarial traffic on industrial protocols, making them especially valuable for testing the effectiveness of anomaly detection, intrusion prevention, and asset monitoring tools.
Hybrid Approaches: Some organizations take advantage of both hardware-in-the-loop and software simulators—creating a layered environment that closely mimics real-world SCADA architectures. This hybrid approach helps teams validate tool effectiveness against both known and emerging threats, and supports red/blue team exercises for workforce development.
For any organization looking to mature their cyber defense capabilities, investing in a realistic SCADA simulation or testbed environment is a crucial step. It’s the laboratory where defenders fortify their skills, and where new security solutions receive their true stress test.
Security Assessment Frameworks for Cyber-Physical Protocols
When it comes to evaluating the security posture of cyber-physical systems—particularly those using industrial protocols like DNP3—a structured assessment framework is invaluable. Organizations often turn to a blend of risk-based methodologies and protocol-specific testing strategies to identify and mitigate vulnerabilities.
For DNP3, which is widely used in SCADA and ICS environments, comprehensive frameworks typically focus on:
- Protocol-Specific Vulnerability Analysis: Assessing how DNP3 handles authentication, encryption, and session management, and identifying known weaknesses such as lack of message integrity controls or susceptibility to spoofing attacks.
- Threat Modeling: Mapping out potential adversary paths, attack surfaces, and failure points unique to the operational context, taking into account both digital and physical vectors.
- Layered Security Controls Review: Evaluating existing defenses, from perimeter firewalls and network segmentation to deep packet inspection tailored for DNP3 traffic.
- Scenario-Based Testing: Simulating realistic attack scenarios—such as man-in-the-middle or replay attacks—against DNP3 components to gauge resilience and response capabilities.
- Compliance with Industry Standards: Measuring alignment with guidelines from organizations like NIST, ISA/IEC 62443, and integrating recommendations from bodies such as SANS ICS and DHS CISA.
The ultimate goal is not only to check boxes on compliance, but to develop a clear, actionable roadmap that strengthens the overall security posture of your SCADA system, especially when legacy protocols like DNP3 are in use.
Machine Learning Models: Support Vector Machines and Random Forests in SCADA IDS
So, how well do machine learning models like support vector machines (SVMs) and random forests actually perform when deployed for intrusion detection in industrial networks? In recent years, SVMs and random forest algorithms have proven to be increasingly valuable for detecting threats that might otherwise slip through more traditional defenses.
Here’s why they matter:
- Pattern Recognition: Both SVMs and random forests excel at spotting subtle patterns and outliers—ideal for catching anomalous behavior on SCADA networks long before a breach fully unfolds.
- Adaptability: These models can be trained on SCADA-specific traffic and behaviors, giving them a leg up when it comes to flagging OT-centric threats as opposed to relying solely on generic, IT-focused signatures.
- Handling Complexity: Random forests, in particular, are praised for their robustness in noisy, real-world data environments, and are less prone to overfitting—even with the complex, heterogeneous data you’ll find in operational technology environments.
- Performance in Practice: Multiple studies and industry reports show that, when configured and trained correctly, these models can achieve high detection rates while minimizing false positives—a persistent problem in OT security.
However, it’s important to note:
- Data Quality is Key: Their effectiveness is directly tied to the quality and depth of the data used for training. Incomplete or outdated datasets will limit results.
- Resource Considerations: Some machine learning models can be resource-intensive. It’s essential to balance security with the system availability demands typical of SCADA environments.
In summary, SVM and random forest models represent a significant upgrade to IDS capabilities—especially as attackers move toward stealthier, more novel approaches that evade signature-based detection. When paired with human expertise and integrated into a layered defense strategy, these tools are powerful assets for any industrial cybersecurity toolkit.
The Role of Distributed Intrusion Detection Systems (DIDS) in SCADA Security
Distributed Intrusion Detection Systems (DIDS) are gaining traction as organizations grapple with securing expansive and complex SCADA environments. Unlike traditional, centralized IDS deployments, DIDS distribute detection sensors across multiple network segments and endpoints. This approach brings a few notable benefits to the table:
- Enhanced Visibility: By aggregating data from various locations, DIDS provide a more complete picture of network activity. This makes it easier to spot coordinated attacks or lateral movement that might otherwise slip under the radar in isolated systems.
- Improved Detection of Sophisticated Threats: The correlation of alerts and events from multiple sources allows for the identification of subtle, distributed exploits or hidden malware, especially in large-scale SCADA networks.
- Scalability: DIDS architectures can more readily adapt to the ever-growing number of devices and segments typical in modern SCADA deployments.
However, implementing DIDS is not without its challenges:
- Coordination Complexity: Managing and synchronizing a network of distributed sensors can be intricate, requiring effective aggregation and correlation mechanisms to avoid a flood of false positives.
- Performance and Resource Constraints: Industrial networks often consist of legacy devices and limited bandwidth. DIDS solutions must be carefully designed to minimize disruption and maintain the real-time requirements of SCADA processes.
- The Need for Advanced Analytics: To achieve meaningful detection, DIDS often rely on multiple machine learning models and advanced analytics. Building, tuning, and maintaining these capabilities requires specialized expertise.
When done right, DIDS can be a force multiplier for SCADA cyber defense, especially in detecting distributed or stealthy attack campaigns. Their effectiveness, however, depends on thoughtful planning, integration, and ongoing management with an eye toward both security and operational reliability.
Host-Based IDS vs. Network-Based IDS in SCADA: Strengths and Weaknesses
When it comes to intrusion detection in the world of SCADA, both Host-Based Intrusion Detection Systems (HIDS) and Network-Based Intrusion Detection Systems (NIDS) have their own superpowers—and kryptonites.
Host-Based IDS (HIDS): A Deep Dive Guard
HIDS is like an ever-vigilant guard living right on the machine—be it an HMI, PLC, or engineering workstation. Its key strengths include:
- Granular Visibility: HIDS monitors activities inside the host device, catching unauthorized changes to files, registries, or system processes. This makes it particularly adept at spotting anomalies and successful attacks that might slip past network defenses.
- Encrypted Traffic Inspection: Since HIDS operates at the source, it can analyze decrypted data before it’s transmitted over the network, making it effective even against attacks hidden within encrypted sessions.
- Great for Forensics: By maintaining detailed logs and system records, HIDS makes post-incident investigations and root cause analysis much more comprehensive.
But it’s not all sunshine and rainbows:
- Performance Overhead: Resource consumption is the Achilles’ heel of HIDS—especially in SCADA, where endpoints like PLCs and HMIs have limited computing resources. Too aggressive monitoring can bog down critical operations.
- Limited Remote Visibility: HIDS only protects the host it’s installed on. It’s not so handy for detecting attacks traversing the network or hopping between nodes.
Network-Based IDS (NIDS): The Perimeter Watchdog
NIDS acts like the big security camera in the sky, keeping a watchful eye on all traffic flowing across your SCADA network. Here’s where it shines:
- Broad Network Monitoring: NIDS inspects packets moving through the network, making it a great fit for detecting scanning, lateral movement, and remote attacks. It’s especially good at identifying suspicious network patterns—before they reach their final destination.
- Minimal Endpoint Impact: Installation is non-intrusive for field devices; NIDS typically resides on network taps or SPAN ports, so PLCs and HMIs go about their business undisturbed.
- Multi-Host Coverage: One well-placed NIDS can monitor traffic from a wide range of devices, improving scalability and manageability in sprawling SCADA networks.
However, NIDS has its own caveats:
- Blind to Encrypted Payloads: Encrypted traffic can be a black box—NIDS can’t see what’s inside, limiting its ability to detect some sophisticated threats.
- Limited Context on Hosts: Since NIDS isn’t privy to what’s happening inside each device, it may miss subtle compromises or attacker activity that doesn’t involve network communication.
- Signature Reliance: NIDS often depends on known attack signatures and protocol patterns, which makes zero-day or custom attacks harder to catch—especially in highly customized OT environments.
Choosing and Combining Both
In a best-practice SCADA security posture, HIDS and NIDS aren’t competitors—they’re tag-team partners. Each covers the other’s blind spots, delivering layered defense without introducing unacceptable operational risks.
By combining deep host visibility with broad network awareness, you can catch more threats—whether they slither across the wire or burrow deep inside a workstation. For most organizations, the smart move is balancing both approaches and tailoring deployment to system architecture, risk appetite, and resource constraints.
How Distributed Intrusion Detection Systems with Semantic-Based Rules Enhance SCADA Security
When it comes to safeguarding SCADA in smart grid environments, traditional intrusion detection alone often falls short. Enter distributed intrusion detection systems (D-IDS) powered by semantic-based rules—a more adaptive, context-aware approach.
Here’s how they work:
- Distributed Deployment: Instead of relying on a single, centralized system, intrusion detection sensors are strategically placed throughout different zones of the SCADA network. This decentralized strategy ensures broader visibility and helps detect lateral movement by attackers, not just attacks coming from outside.
- Semantic-Based Rules: Unlike static signature-based detection (which only spots known threats), semantic rules focus on the meaning and context of data moving through your smart grid’s control systems. These rules leverage knowledge of normal operations—like which devices typically communicate and what commands are standard—and flag unusual, suspicious actions that break with established patterns.
- Real-Time Analysis: Once data is collected from across the network, semantic-based D-IDS platforms analyze activity in near real time. Suspicious sequences—such as unauthorized control commands or out-of-context device messages—are quickly identified and escalated for immediate response.
- Reduced False Positives: The semantic angle helps minimize noise and irrelevant alerts. Since rules are grounded in true operational context, the system is less likely to bombard your team with false alarms, letting you focus on genuine threats.
By fusing distributed sensors with an understanding of how your SCADA systems should behave, this approach provides deeper, actionable insights—crucial for the rapid detection and isolation of advanced threats in smart grid infrastructure.
SCADA Testbeds for Security Analysis
To truly understand and strengthen the security of SCADA control systems, organizations are increasingly turning to specialized testbeds—essentially, sandboxed environments that accurately replicate real-world control networks. These testbeds play a pivotal role in both research and practical security assessments.
A SCADA security testbed allows cybersecurity professionals to:
- Safely Simulate Attacks: By mirroring the hardware and software found in operational SCADA environments, testbeds make it possible to execute cyber-attacks and observe their effects without risking actual infrastructure.
- Evaluate Defensive Measures: Security teams can deploy and refine various defense mechanisms—from new firewalls and intrusion detection systems to advanced anomaly detection platforms—seeing firsthand how they perform against insider and outsider threats.
- Train Personnel: Testbeds provide a hands-on, realistic training ground for engineers, operators, and security analysts. Staff can practice identifying malicious activities, performing incident response, and restoring systems after hypothetical breaches.
- Advance Research: Academic and industry researchers leverage these platforms to identify vulnerabilities, develop new detection techniques, and understand how specific attack vectors could propagate through a SCADA network.
By offering a controlled yet realistic environment, SCADA testbeds bridge the gap between theoretical security strategies and the gritty realities of industrial network defense.
Machine Learning in SCADA Intrusion Detection: SVM, KNN, and Linear Regression
Machine learning is stepping up as a powerful ally in the battle for SCADA security, offering several algorithms that can help spot intrusions before they become disasters. Let’s take a closer look at how three common approaches—Support Vector Machines (SVM), K-Nearest Neighbours (KNN), and Linear Regression (LR)—are being leveraged to bolster anomaly detection in industrial networks.
Support Vector Machines (SVM): SVMs shine in SCADA environments by classifying data points—separating “normal” from “suspicious” network activity. By analyzing historical traffic patterns (think: commands sent to PLCs or timing between control actions), SVMs can carve out a boundary that distinguishes benign from potentially malicious behavior, reducing false positives. Because SVMs are designed to maximize the separation between categories, they’re especially effective at flagging subtle deviations that could signal a slow-moving attack.
K-Nearest Neighbours (KNN): KNN is the classic “who are your friends?” approach. When a new network event occurs, KNN compares its characteristics—like message content or timing—to a library of past events. If most of its “nearest neighbors” are in the malicious camp, the algorithm sounds the alarm. This makes KNN well-suited for environments where attack behaviors may slightly mutate over time, as long as the system isn’t flooded with massive amounts of data (since search complexity can become a limitation).
Linear Regression (LR): While typically associated with forecasting, linear regression can help predict expected system values, such as sensor readings or control responses. By establishing what “normal” looks like for a given data stream, any significant deviation can be quickly interpreted as an anomaly—potentially pointing to tampering or malfunction. This statistical backbone is especially handy for flagging subtle manipulations that might otherwise get lost in the noise.
Together, these machine learning techniques amplify SCADA defenses by learning from historical operations and proactively flagging anything that falls outside the bounds of safe, established behavior. Their real strength lies in their adaptability—responding to new threats as they evolve, rather than just matching known signatures.
Model-Based vs. Expert System-Based vs. Machine Learning-Based Algorithms in SCADA Intrusion Detection
SCADA intrusion detection solutions can leverage several algorithmic approaches—each offering different strengths and weaknesses when it comes to identifying threats in complex industrial environments:
Model-Based Algorithms: These typically rely on predefined patterns or signatures derived from known attack types. Think of them as the digital equivalent of a bouncer with a list of known troublemakers. If the incoming network traffic looks like something on the list, an alert is triggered. While effective at catching familiar threats, model-based approaches may struggle with novel tactics or zero-day exploits, since they operate within the boundaries of their programmed knowledge.
Expert System-Based Algorithms: Here, the solution mimics human reasoning, drawing upon heuristics, rules of thumb, and accumulated expert knowledge. These systems assess behaviors in the SCADA network much like a seasoned operator spotting odd patterns based on years of experience. By encoding custom rules and decision trees, expert systems can be tailored to unique industrial processes. However, their effectiveness is limited by the breadth and accuracy of the knowledge supplied—if attackers find new ways to sneak around the rules, the system may be left in the dark.
Machine Learning-Based Algorithms: Taking things a step further, machine learning models use historical data to spot abnormal patterns and predict new threats without requiring explicit rules for every scenario. Algorithms like Support Vector Machines (SVM), k-Nearest Neighbors (KNN), or linear regression can cluster normal versus suspicious behaviors, enabling detection of unknown attack strategies. The catch? These models typically require large, high-quality datasets to train, and their complexity can introduce challenges in interpretability and ongoing maintenance.
Each approach plays a role in the overall SCADA defense-in-depth strategy. The most resilient environments layer all three, ensuring coverage for both well-trodden attack paths and those on the bleeding edge.
Multi-Agent Collaboration in SCADA Network Security
A promising approach for safeguarding SCADA networks involves the use of multi-agent collaboration. In simple terms, this means deploying multiple, autonomous monitoring agents—each acting like a specialized security guard—across the network. These agents operate independently but also share information and coordinate responses in real-time.
Here’s why this matters for modern SCADA environments:
- Distributed Detection: By having multiple agents monitor different segments of the network, suspicious activity can be identified more quickly and efficiently, especially when an attack tries to move across zones or target multiple devices at once.
- Increased Resilience: If one agent is compromised or goes offline, others continue to function, ensuring that your monitoring capabilities aren’t limited to a single point of failure (something attackers love to exploit).
- Collaborative Analysis: Agents can rapidly share alerts and insights, piecing together subtle signs of intrusion that might look harmless in isolation but reveal coordinated attack patterns when viewed together.
- Faster, Smarter Response: Autonomous agents can automatically initiate defensive measures, escalate alerts, or even quarantine affected segments while alerting human operators—giving defenders valuable time against fast-moving threats.
This approach essentially turns your SCADA security from a small team into a well-coordinated security force, constantly communicating and adapting to keep threats at bay.
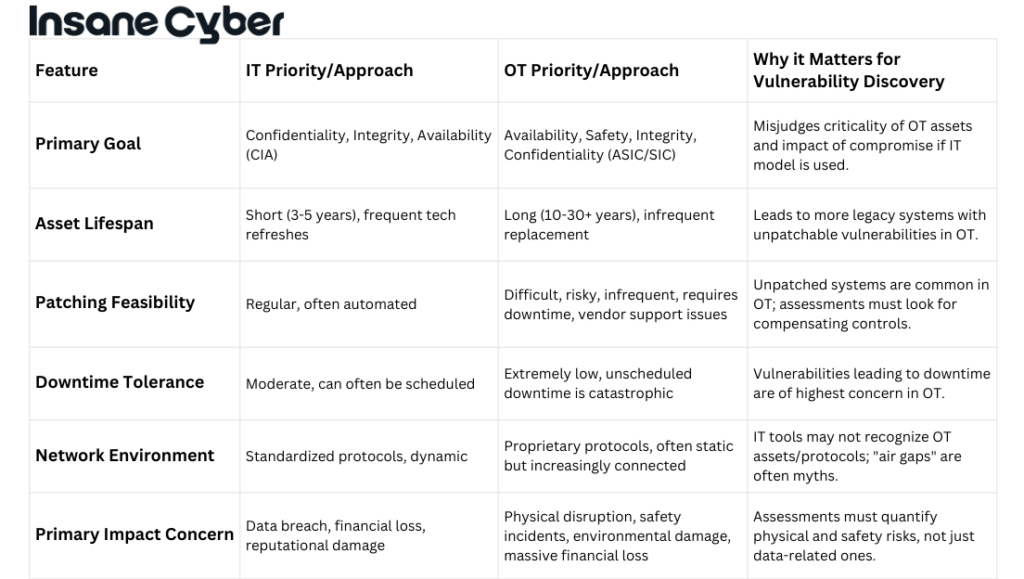
How Do Anomaly Detection Techniques Perform in Big Data SCADA Environments?
As SCADA environments grow more complex and interconnected, leveraging anomaly detection in the context of big data becomes vital for timely threat identification. But how well do these techniques actually perform when deployed at such scale?
- Performance Factors: The effectiveness of anomaly detection hinges on several factors—accuracy in flagging genuine threats, minimizing false positives, and responding swiftly enough to prevent real-world consequences. The immense volume and variety of data flowing through modern SCADA networks represent both a challenge and an opportunity: more data enables richer baselines and pattern recognition, but it also increases the computational demands.
- Types of Techniques: Common approaches include statistical models, machine learning algorithms, and more recently, deep learning. Machine learning–based anomaly detection tools (think those leveraging supervised or unsupervised models) have shown strong results, especially when they’re tuned for the quirks of OT-specific traffic and operational states.
- Scalability & Practicality: Scalability is paramount. Some anomaly detection platforms—like those from Nozomi Networks, Dragos, or Claroty—are engineered to work efficiently even as data volume explodes, offering near-real-time analysis without overwhelming your SOC.
- Areas for Caution: Big data can also mean big noise. Careful tuning is necessary to avoid alert fatigue. Additionally, traditional anomaly detection can struggle with the subtle, slow-moving attacks common in SCADA, making ongoing refinement and contextual awareness essential.
In summary, anomaly detection techniques—when properly implemented and customized for SCADA’s unique traffic patterns—are increasingly powerful in big data applications, but success hinges on balancing sensitivity, scalability, and operational practicality.
The Role of Integrity Checks in Defending Against DoS and DDoS Attacks
Integrity checks on field devices serve as a frontline defense against denial-of-service (DoS) and distributed denial-of-service (DDoS) attacks targeting SCADA environments. By continuously verifying the authenticity and health of communications between field devices (like RTUs and PLCs) and the SCADA server, these mechanisms can quickly detect and block suspicious or malformed traffic designed to disrupt system operations.
One common approach incorporates token-based authentication and secure encrypted channels—think TLS encryption—to ensure that only verified, authorized commands and data are accepted by critical devices. Not only does this help prevent attackers from flooding the network with malicious requests, but it also thwarts attempts to inject illegitimate communications that might slip past traditional perimeter defenses.
In practice, robust integrity verification ensures that:
- Only validated packets from trusted sources reach field devices
- Malicious traffic, such as spoofed requests often seen in DoS and DDoS scenarios, is promptly rejected
- Any deviation from expected communication patterns is flagged and can trigger automated or manual response protocols
The bottom line? Strong integrity checks, when implemented correctly, are both efficient and compatible with modern industrial devices—effectively safeguarding SCADA systems against a range of disruptive attack tactics.
Using SCADA Testbeds for Vulnerability Analysis
Assessing vulnerabilities in live SCADA systems is inherently risky—no one wants to bring an entire plant to a halt or disrupt critical operations just to find out where they’re exposed. This is where SCADA testbeds come into play. These are controlled, laboratory-based environments designed to safely mimic real-world industrial control systems, complete with accurate configurations and common industrial communication protocols.
With a SCADA testbed, security researchers and engineers can:
- Simulate Attacks and Weaknesses: Conduct penetration tests and simulate cyberattacks without threatening production environments, revealing how vulnerabilities might be exploited in the wild.
- Evaluate Security Tools and Patches: Test how network defenses, anomaly detection platforms, and security patches behave under realistic conditions before rolling them out to live systems.
- Study Complex Protocols: Dive deep into the idiosyncrasies of industrial protocols like Modbus, DNP3, or IEC 61850, uncovering protocol-specific risks that standard IT environments might overlook.
Prominent testbeds, such as SCADASim and university lab installations, provide invaluable sandboxes for advancing the security of industrial operations—allowing practitioners to find and fix weaknesses before attackers can take advantage.
Deep Transfer Learning in SCADA Intrusion Detection
Let’s zoom in on one of the more innovative approaches now gaining ground in SCADA cybersecurity: deep transfer learning (DTL), especially as it applies to intrusion detection systems (IDS).
What is Deep Transfer Learning (DTL)?
In a nutshell, deep transfer learning is a powerful artificial intelligence technique. Rather than training an AI model from scratch (which often means needing vast amounts of labeled data that isn’t always available in industrial networks), DTL enables you to take knowledge learned from one domain—say, conventional IT security—and apply or adapt it to another, such as SCADA or broader ICS environments. Think of it as borrowing the “street smarts” an AI has picked up elsewhere and then retraining it to handle the unique quirks of your operational technology network.
How Does DTL Apply to IDS for Industrial Control Systems?
Traditionally, IDS platforms in industrial environments face a common headache: there just isn’t enough attack data specific to OT environments for robust AI training. By leveraging deep transfer learning:
- Pre-trained models—often first “taught” on larger, more generic datasets—can be fine-tuned with whatever limited but relevant data organizations do have from their own SCADA systems.
- This fusion of knowledge lets security teams develop IDSs that spot emerging threats and subtle anomalies, even when signature-based detection would fail.
- DTL-based IDS solutions can tap into several data sources (network traffic, event logs, protocol behaviors) and adapt detection mechanisms to uncover never-before-seen or highly targeted attacks.
Why Does This Matter?
Adopting deep transfer learning in IDSs for SCADA means:
- Improved accuracy and fewer false alarms, crucial for environments where downtime isn’t an option.
- Faster adaptation to new attack patterns, leveraging advances in both AI research and growing libraries of publicly available ICS datasets (like those from MITRE, UNSW-NB15, and others).
- SCADA security teams can focus expertise where it matters most, instead of spending months gathering enough data to start building anything useful.
In short: DTL is fast becoming a practical way to get smarter, more adaptive intrusion detection in environments where both data and downtime are extremely limited.
Machine Learning-Based Feature Selection for Large-Scale Intrusion Detection
Effectively detecting intrusions in sprawling SCADA or industrial networks requires more than tossing all your data into a black box and hoping for the best. Feature selection—the process of pinpointing which data points actually matter—is critical when leveraging machine learning for intrusion detection at scale. The goal? Reduce noise, cut down computation, and sharpen your focus on what signals a real threat.
Here’s how machine learning-based feature selection typically plays out in this context:
- Filter Methods: These rank network features according to statistical criteria such as information gain, chi-squared score, or correlation. For instance, you might use Pearson correlation or mutual information to weed out features that don’t actually correlate with intrusion behaviors. The big advantage: speed and scalability, which is essential when you’re sifting through mountains of real-time traffic.
- Wrapper Methods: These approaches evaluate subsets of features by actually running them through a predictive model, such as a random forest or decision tree. The iterative process—testing combinations for predictive value—often yields higher accuracy, although it’s more resource-intensive. Techniques like recursive feature elimination or even good old stepwise selection fall into this bucket.
- Embedded Methods: Here, feature selection happens as part of the model-building process itself. Algorithms like LASSO (Least Absolute Shrinkage and Selection Operator) or tree-based ensemble models automatically reduce the influence of less significant features, which is particularly useful in dynamic ICS/SCADA environments.
When deployed in SCADA network monitoring, these techniques allow security teams to focus analytics on behavioral fingerprints most strongly associated with attacks, minimizing false positives and detection lag. Machine learning feature selection is especially valuable when coupled with domain-specific expertise—think industrial protocol knowledge or understanding which data fields are likely to spike during an incident.
That’s why you’ll often see a combination of these techniques used in large-scale industrial intrusion detection: first, filtering out irrelevant traffic; next, homing in on the features that truly differentiate normal operations from emerging threats.
The Need for Better SCADA Datasets and Testbeds
Let’s talk about a common stumbling block: the state of datasets and testbeds when it comes to detecting and assessing threats within SCADA environments.
Why Current Datasets Fall Short
While general-purpose vulnerability databases like NVD and CVE offer value, they don’t truly reflect the unique protocols, devices, and risks found in SCADA networks. Many security analysts fall back on datasets like KDD99 or its successor, NSL-KDD, to test network intrusion detection systems. The catch? These legacy datasets bring their own headaches:
- Limited Applicability: Designed for traditional IT, not OT. They miss the nuances of industrial control networks.
- Data Bloat and Redundancy: KDD99 is large but riddled with redundant records, skewing results and increasing resource consumption.
- Outdated Entries: Water supply datasets, for example, haven’t seen meaningful updates in years—and don’t adequately track the sophistication of current SCADA threats.
- Lack of Realism: Other options, like DARPA datasets, were made in isolated environments far removed from today’s interconnected OT-IT world.
All this leaves a gaping hole: there’s no modern, comprehensive, and SCADA-specific dataset that maps to real-world use cases—let alone one that covers the broad diversity of industries (power, water, manufacturing, and beyond).
Improving SCADA Testbeds for Valid Research
Testing and validating new tools or risk assessments shouldn’t be guesswork, but building and maintaining realistic SCADA testbeds is neither fast nor cheap. A few persistent roadblocks include:
- Cost and Complexity: Building high-fidelity testbeds that accurately mimic SCADA architectures (across water, oil & gas, energy sectors, etc.) is resource-intensive.
- Scalability Issues: Many current setups either can’t scale or lack the simulation capabilities that real-world scenarios demand.
- Fidelity Gaps: An effective testbed must reproduce live, messy, and interconnected environments—not just idealized simulations.
What’s Needed?
The industry needs collaborative effort behind two things:
- Comprehensive, regularly refreshed SCADA datasets—including traffic, system logs, and cross-industry application data that reflect today’s threats and architectures.
- Scalable, high-fidelity testbeds—environments that make it possible to safely design, test, and benchmark monitoring and defense solutions across all critical infrastructure sectors.
Addressing these gaps means better detection, faster innovation, and—ultimately—stronger, more resilient SCADA defenses.
The Role and Scope of SCADA Testbeds in Cybersecurity Research
Understanding and defending SCADA systems is tricky when you’re working with live, production environments—there’s just too much at risk. That’s where SCADA testbeds enter the scene. These are controlled, customizable environments designed to mimic real-world SCADA networks as accurately as possible, giving researchers and defenders a safe playground to push boundaries, break things (on purpose), and learn.
So, what exactly can you do with a robust SCADA testbed? Let’s break it down:
Vulnerability Assessment Playground: Authentic vulnerability assessments are nearly impossible on production SCADA networks without risking outages or safety incidents. Testbeds offer a risk-free zone for uncovering misconfigurations, unsafe protocol implementations, and gaps in real-world SCADA stacks. Tools like SCADASim, PowerCyber, and the testbeds at Mississippi State University are popular choices for hands-on experimentation.
Security Control Testing: Think of testbeds as proving grounds for security controls. Want to know whether a new anomaly detection algorithm, firewall configuration, or incident response workflow will actually stop a cyberattack? Testbeds allow validation and fine-tuning of these defenses in a realistic (but safe) setting before rolling them out to critical infrastructure.
Impact and Resilience Analysis: When it comes to understanding how attacks play out—or just how bad “bad” can get—testbeds let researchers simulate attacks and measure the actual consequences. This might include everything from data manipulation and device takeover to full-on process disruption. The insights gained inform better risk assessments as well as more resilient designs.
In short: SCADA testbeds are essential for advancing cybersecurity research without putting real operations—or lives—at risk. They’re the training grounds for the next generation of industrial defenders.
The Role of CWE in SCADA Vulnerability Management
Understanding where your SCADA system might be exposed starts with speaking a common language—and that’s where the Common Weakness Enumeration (CWE) comes in. Think of CWE as an ever-evolving catalog of known vulnerability types—everything from misconfigured authentication to insecure default settings.
For SCADA environments, referencing CWE helps security teams:
- Identify recurring vulnerability patterns: By mapping discovered issues to relevant CWE categories, organizations gain clarity on which weaknesses are most prevalent in their environments.
- Prioritize remediation efforts: Not all vulnerabilities are created equal. CWE definitions enable teams to assess the potential impact and prioritize fixes based on the risk posed to critical industrial processes.
- Improve security practices: Using CWE as a guide, defenders can adapt implementation and configuration strategies to avoid the most common security pitfalls seen in operational technology.
Ultimately, CWE serves as a foundational resource to sharpen the focus of both vulnerability assessments and long-term security improvements within SCADA systems.
SCADA Interoperability: Challenges and Solutions
A persistent headache in SCADA communications is interoperability—getting all the moving parts, often sourced from different vendors and eras, to speak the same language. Traditionally, components like MTUs, RTUs, PLCs, and HMIs relied on proprietary protocols, each tailored to a particular manufacturer (think Modbus, Profibus, or Conitel). While these protocols were great for locking in customers and optimizing for specific hardware, they turned integration projects into a compatibility nightmare.
If your environment mixes and matches hardware or expands over time, proprietary protocols can block subsystems from talking to each other—essentially building communication silos. This not only slows down expansion but also complicates centralized monitoring and unified response to incidents.
The industry’s answer? Moving toward standardized, open communication protocols. Adopting open standards, such as IEC 60870-5-104 or OPC UA, unlocks several benefits:
- Ease of Expansion: New devices slip more easily into the existing infrastructure.
- Greater Flexibility: You’re not stuck using a single vendor’s ecosystem.
- Simplified Integration: Standard protocols mean systems from multiple manufacturers can cooperate without expensive workarounds.
- Future Proofing: Open standards are widely supported, reducing the risk of vendor lock-in or obsolescence.
Ultimately, embracing standardized protocols is key to building a robust, interoperable SCADA environment that can adapt as operational needs—as well as the threat landscape—evolve.
Patch Management in SCADA vs. IT Environments
Patch management in SCADA systems poses unique challenges when compared to traditional IT environments. In corporate IT, rolling out patches is often a routine, automated process—updates are pushed out quickly to address vulnerabilities and keep systems secure. However, SCADA environments operate with a different set of priorities.
Because SCADA systems control critical infrastructure and sensitive industrial processes, uptime and stability are paramount. Applying patches immediately, as you might in IT, can inadvertently disrupt operations or even bring essential services offline. As a result, patches are typically introduced much more cautiously, often scheduled during planned maintenance windows rather than deployed on the fly.
Complicating matters, many SCADA devices run on legacy hardware or outdated firmware that may not even support the latest patches from vendors. In these cases, organizations might need to rely on compensating controls—like enhanced network segmentation, additional monitoring, or industrial firewalls—to mitigate known risks when patching isn’t feasible. This careful, risk-based approach to patch management helps balance security with the need to keep critical operations running smoothly.
Common Practices in DTL-Based IDS Research
When diving into research on Deep Transfer Learning (DTL)-based Intrusion Detection Systems (IDS), the methodology tends to coalesce around a few recurrent choices:
- Datasets: Popular datasets include NSL-KDD, CICIDS2017, and UNSW-NB15. These are staples for benchmarking, offering ample diversity in simulated attacks and normal activity, which are vital for training, validation, and comparative analysis.
- Types of DTL: Researchers apply various transfer learning strategies, such as domain adaptation (to address distribution differences between source and target domains), fine-tuning of pre-trained models, and feature extraction from pre-established neural networks.
- Pre-Trained Networks: Convolutional Neural Networks (CNNs) like VGG16 or ResNet, and architectures such as LSTM, are frequently pre-trained—often on large-scale public datasets (like ImageNet)—before adaptation to SCADA-specific intrusion detection.
- IDS Techniques: Approaches range from classic supervised learning (using labeled data to classify benign vs. malicious traffic) to semi-supervised methods that can leverage both labeled and unlabeled data, exploiting DTL to make sense of limited, domain-specific samples.
- Evaluation Metrics: Research typically hinges on accuracy, F1-Score, and false-positive (false-alarm) rates to gauge performance improvements. Other metrics like precision, recall, and AUC-ROC curves occasionally make an appearance for more nuanced analyses.
By combining these building blocks—carefully chosen datasets, effective transfer learning strategies, and robust evaluation criteria—researchers are steadily enhancing the accuracy and reliability of SCADA-focused IDS solutions.
How DTL Boosts IDS Performance with Limited Labeled Data
Detecting threats in SCADA networks often suffers from one persistent challenge: a lack of labeled attack data in the OT environment. This is where Domain Transfer Learning (DTL) comes into play.
DTL essentially acts as a bridge, allowing intrusion detection systems (IDS) to “borrow” knowledge from other, data-rich environments—like IT networks or simulated datasets. Instead of starting from scratch, the IDS adapts what it’s already learned from one domain and fine-tunes it to spot threats in the SCADA network, even if only a handful of local examples exist.
Why is this useful?
- Reduces reliance on local labeled data: DTL enables more accurate detection without the impossible task of manually labeling thousands of OT events.
- Faster adaptation to new threats: By merging insights from multiple domains, DTL-equipped IDS solutions detect never-before-seen attack patterns more effectively.
- Cost-effective security: Maximizing use of existing knowledge means organizations can strengthen monitoring without massive investments in new data collection.
In short, DTL helps overcome the “needle in a haystack” problem by making the most of every shred of data—without putting your processes at risk.
Noteworthy ICS Traffic Datasets for Research
Researchers looking to advance intrusion detection for industrial control systems aren’t starting from scratch. Several well-known datasets are available, specifically curated to mirror real-world ICS/SCADA traffic patterns and attack scenarios. For example, curated datasets such as those produced by academic consortia and government-backed initiatives often include a mix of benign and malicious traffic:
Morris & Gao Dataset: Developed for the research community, this dataset simulates traffic between various industrial components—including PLCs and HMIs—while integrating both typical operations and a variety of attack scenarios. It’s frequently used to train and benchmark anomaly detection models for SCADA systems.
SWaT and Power System Datasets: Beyond just network logs, datasets from testbed environments like SWaT (Secure Water Treatment) provide deep packet-level captures alongside ground-truth labels. This makes them invaluable for those designing and evaluating IDS models that must distinguish between normal operations and attacks targeting ICS environments.
Leaning on these datasets allows security teams and researchers to rigorously validate new detection techniques before deploying them into the high-stakes world of operational technology.
Recommended Data Sets for SCADA Intrusion Detection Research
If you’re wading into the world of SCADA-focused intrusion detection, a handful of well-established data sets can help you test and refine your security solutions:
- Lemay-Fernandez SCADA Data Sets: Developed for the purpose of security experimentation, these data sets simulate SCADA traffic and embedded attack patterns, making them a staple for benchmarking intrusion detection methods.
- Power Grid Malicious Command Data: Offering a look at both normal and compromised command traffic, this data supports the detection of malicious control activity within smart grid environments—perfect for researchers focused on critical infrastructure.
- ICS Traffic Data Sets (Morris-Gao): Featuring real and simulated industrial control system (ICS) traffic, these data sets help security professionals analyze a variety of attack scenarios in a context that reflects actual operational environments.
- UNSW-NB15 Data Set: While not exclusively OT, UNSW-NB15 is widely used for network intrusion detection research due to its comprehensive labeling of benign and malicious traffic, making it adaptable for OT/SCADA-focused studies.
Using these curated resources, researchers can evaluate, fine-tune, and validate their intrusion detection approaches with realistic network scenarios—an essential step before rolling out solutions on live systems.
Real-Time Testbeds for Power Grid Cyber-Physical Security
An often-overlooked, yet critical, asset in SCADA cyber defense is the use of real-time testbed environments. These platforms simulate actual grid operations, allowing security teams to safely test detection, response, and recovery scenarios without risking live infrastructure. By mimicking both the physical and cyber layers of an operational power grid, real-time testbeds provide a controlled environment to evaluate new security technologies, validate monitoring tools, and train personnel under realistic attack conditions.
Leading research institutions and industry labs have established advanced testbeds leveraging hardware-in-the-loop (HIL) and software simulation to replicate the complex interplay between IT and OT systems. For example, platforms like Idaho National Laboratory’s “Power Grid Cybersecurity Test Bed,” the DOE’s “National SCADA Test Bed” program, or even open-source initiatives such as the “PowerCyber Testbed” at Iowa State University, all offer environments for safe experimentation—ensuring defenses are battle-ready when real threats emerge.
The Need for Comprehensive SCADA-Specific Datasets
While there’s no shortage of general-purpose cybersecurity datasets—think NVD, CVE, or the venerable KDD99—most fall short when applied to real-world SCADA security testing. So, why is the development of a dedicated SCADA dataset so critical?
Unique System Behaviors: SCADA environments operate with specialized protocols, hardware, and operational constraints that generic datasets simply don’t capture. Testing detection tools against data that lacks these unique characteristics risks missing threats hiding in plain sight.
Outdated and Incomplete Standards: Many available datasets, like KDD99 and DARPA, are either outdated or built on isolated testbeds that don’t reflect today’s interconnected SCADA architectures. Some datasets even suffer from duplicate records or redundant information, making them impractical for training accurate and efficient monitoring tools.
Coverage Across Applications: Current datasets tend to focus on narrow use cases—say, water treatment or power grids—without reflecting the wide diversity of SCADA applications in industries like manufacturing, oil and gas, or transportation. This means security solutions trained on such data may miss threats unique to other sectors.
Evolving Threats: As attack methods and technologies evolve, so should the datasets used for testing defense mechanisms. Stale datasets can’t help defenders stay a step ahead of the latest attack tactics that target modern SCADA deployments.
That’s why developing an up-to-date, comprehensive SCADA dataset—one that mirrors real-world architectures and application areas—is essential for building and evaluating robust cyber monitoring tools in these critical environments.
Why Password Salting Matters in SCADA Systems
Password protection in SCADA environments shouldn’t be a one-size-fits-all affair. Salting passwords—that is, adding unique random data to each password before hashing—delivers significant benefits for defenders:
- Thwarts Rainbow Table Attacks: Salting ensures that even if two users share the same password, their hashed credentials look completely different. This renders precomputed rainbow tables (massive databases of pre-hashed values used by attackers) essentially useless.
- Enhances Resistance to Large-Scale Breaches: Should a malicious actor gain access to hashed credentials, the presence of unique salts makes mass decryption efforts much more time-consuming and resource-intensive.
- Aligns with Industry Best Practices: Organizations like NIST and leading cybersecurity vendors recommend password salting to bolster password integrity and overall system resilience.
In short, effective password salting significantly raises the bar for attackers trying to crack credentials—an essential consideration when protecting the sensitive operations controlled by SCADA networks.
Harnessing Attack Simulation Frameworks in Smart Grid Security
Attack simulation frameworks play a pivotal role in strengthening the cybersecurity posture of modern smart grids. By replicating realistic attack scenarios in a controlled setting, these tools allow security teams to proactively identify potential weaknesses—before adversaries do. Think of them as a “fire drill” for your digital infrastructure: they test defense mechanisms, response procedures, and even personnel readiness under simulated cyber duress.
- Benchmarking Defenses: Simulation platforms let you assess how well your existing security controls stand up to contemporary cyber threats—such as ransomware, supply chain exploitation, or protocol-specific attacks.
- Identifying Blind Spots: By mimicking sophisticated attacker tactics, these frameworks can expose hidden vulnerabilities within network architectures, device configurations, and even operational workflows.
- Informing Incident Response: Regular testing of response processes ensures teams are not just prepared on paper, but can react swiftly and effectively in real-world situations.
- Continuous Improvement: As attackers evolve their strategies, simulation environments make it possible to iteratively test and refine defenses, ensuring your security isn’t stuck in last year’s playbook.
For SCADA and OT environments—where the stakes often include the physical world—incorporating attack simulation into your security program is crucial. It bridges the gap between theory and practice, helping you uncover gaps that audits and checklists might miss.
Why the KDD Cup 99 Dataset Still Matters
While talking tools and tech is great, it’s worth highlighting one of the building blocks for intrusion detection research: the KDD Cup 99 dataset. For years, it’s been a go-to resource for anyone in cybersecurity looking to benchmark, test, and refine intrusion detection systems—sort of the “Hello World” of network attack datasets.
- Foundation for Benchmarking: The dataset provides a standardized baseline, letting researchers and vendors fairly compare algorithms and detection techniques.
- Wide Adoption: Its complexity and scope—covering a mix of normal and malicious network activities—have made it a staple in academic studies and in the development of machine learning-based detection tools.
- Fuel for Innovation: KDD Cup 99’s detailed records pushed the envelope for anomaly detection strategies, inspiring advances in how we detect the subtler cyber threats targeting environments like SCADA.
Of course, its age means it’s no longer perfect—modern networks are a different beast. But it set the stage for how real-world threat detection research is conducted, especially when teaching machines to spot the oddities hackers leave behind.
Why SCADA Testbed Development Is So Challenging
Building effective testbeds for SCADA environments isn’t just time-intensive—it can quickly become an expensive beast. Unlike spinning up a few virtual machines for a typical IT setup, SCADA testbeds need to mimic real-world conditions across industries like water treatment, gas distribution, power grids, and more. Here’s the challenge: these environments are complex, tightly integrated with physical processes, and require high-fidelity simulation to provide any meaningful results.
A top-notch SCADA testbed should be:
- Highly Scalable: It must represent both small plants and sprawling, interconnected systems to allow researchers and operators to test a wide variety of scenarios—from minor subsystem failures to large-scale attacks.
- Extremely Realistic: Accuracy matters. The testbed needs to simulate actual hardware, protocols, and operational behaviors as closely as possible. This fidelity is key to understanding how new threats could play out in the physical world.
- Multi-Industry Ready: The best testbeds are adaptable, supporting use cases for everything from electricity and oil to water and manufacturing.
Scalability and realism aren’t easy (or cheap) to achieve. Funding and resources must be allocated not only to the physical or virtual infrastructure but also to developing models that behave like the real thing. As a result, research often gravitates toward simulated environments that capture the complexity of SCADA without the risk—and cost—of live equipment.
Core Approaches to Feature Extraction for Intrusion Detection
Let’s break down how feature extraction—essentially, teaching our systems what to look for—works within intrusion detection for SCADA environments. The approaches can be grouped into three primary camps, each with its own quirks and trade-offs:
Signature-Based and Model-Driven Methods: These are the cybersecurity equivalent of recognizing faces in a crowd—systems are trained to spot known threats based on established patterns and behaviors. Signature-based tools match observed data to a library of “bad guy” fingerprints, making them efficient at catching familiar attacks but less effective against new, never-before-seen threats.
Heuristic and Expert System Techniques: Imagine having a seasoned plant operator hardwired into your security stack. Expert systems leverage accumulated human knowledge, rules, and heuristics to flag suspicious activity—even when it doesn’t match a known signature. They’re great for surfacing weirdness that falls outside the usual patterns but can be challenging to fine-tune and maintain for complex or evolving environments.
Machine Learning/Pattern Recognition Approaches: Here’s where things get interesting. By crunching historical data, these platforms learn what “normal” looks like for your SCADA environment—then flag outliers. Some favorites in this category include support vector machines (SVM), k-nearest neighbors (KNN), and linear regression-based models:
SVM: Finds the clearest dividing line between normal and abnormal—helpful for environments where accuracy is paramount.
KNN: Groups data points based on what they’re closest to, making decisions based on similarity to known examples.
Regression Models: Useful for predicting values and spotting outcomes that don’t match the historical relationship between variables.
The strength of machine learning approaches lies in adapting to emerging threats and catching subtle deviations—though they do require a good chunk of quality data and some horsepower under the hood.
These techniques, often working in tandem, form the backbone of robust feature extraction for modern SCADA intrusion detection. Picking the right blend depends on your risk appetite, operational constraints, and the ever-shifting tactics of attackers poised to target our critical infrastructure.
The Challenge of Resource Constraints in SCADA Cybersecurity
It’s important to recognize that SCADA systems operate under tight resource limitations. Unlike typical IT systems, which are built to handle a variety of security software and protections, many SCADA devices are engineered for efficiency and reliability—often running on minimal memory and processing power. This stripped-down approach means there simply isn’t room to pile on standard security mechanisms like advanced encryption, agent-based endpoint controls, or even frequent software updates.
As a result, options that are routine on office computers—think complex password policies, extensive audit logging, or real-time malware scanning—may be outright impossible or can threaten the stability of the underlying control process. This leaves many organizations balancing the need for robust security with the imperative of keeping critical operations safe, stable, and uninterrupted.
The upshot? Security solutions for SCADA must be carefully selected, lightweight, and often tailored to avoid taxing limited device resources or disrupting vital industrial processes.
Fast Outlier Detection Algorithms for Intrusion Detection
Modern SCADA monitoring tools increasingly rely on sophisticated outlier detection algorithms to spot suspicious activity with speed and accuracy. Among the more notable techniques is the Local Correlation Integral (LOCI), which excels at identifying anomalies or “outliers” in complex, high-dimensional data. Unlike traditional statistical methods, LOCI analyzes patterns based on local density variations, making it adaptive to the subtle shifts typical of cyber intrusions.
Beyond LOCI, other fast algorithms regularly used in intrusion detection include:
- Local Outlier Factor (LOF): This method benchmarks how isolated a data point is compared to its neighbors. It’s especially handy for detecting subtle deviations in large datasets where threats might otherwise blend in.
- Isolation Forest: Unlike density-based approaches, Isolation Forest rapidly isolates anomalies by recursively partitioning data. Its efficiency makes it well-suited for real-time monitoring of industrial networks.
- One-Class SVM: Leveraging machine learning, this technique learns the normal behavior of SCADA systems and flags novel, potentially malicious activity.
These algorithms are valued in SCADA environments for their speed, scalability, and ability to adapt to evolving threats—traits that are crucial when seconds count, and the line between normal and nefarious is razor-thin.
Understanding the UNSW-NB15 Dataset
When it comes to testing and improving network intrusion detection systems (IDS), having the right dataset is crucial. Enter UNSW-NB15—a comprehensive, modern dataset widely used by cybersecurity researchers and practitioners.
So, what sets UNSW-NB15 apart? Unlike older datasets that may not reflect today’s threat landscape, UNSW-NB15 was specifically built to represent real-world network traffic, incorporating both legitimate behaviors and a variety of up-to-date attack vectors. This makes it especially valuable for training, evaluating, and benchmarking intrusion detection tools and machine learning models.
Here’s how it’s commonly used:
- IDS Benchmarking: Security teams can simulate attacks and normal traffic using the UNSW-NB15 dataset to test how well their IDS solutions detect and distinguish threats.
- Machine Learning Development: Researchers leverage this dataset to develop and validate machine learning algorithms designed for anomaly and threat detection, aiming to catch even the most subtle or novel intrusions.
- Realistic Lab Environments: Because it includes diverse attack scenarios (such as exploits, worms, and DoS attacks), the dataset provides a realistic playground to assess how detection tools perform under conditions that closely mirror live networks.
In short, UNSW-NB15 is a go-to resource for anyone serious about advancing network security and intrusion detection capabilities.
Evaluating SCADA Testbeds: Balancing Fidelity, Flexibility, and Scalability
SCADA testbeds play a crucial role in validating security strategies before deploying them in live environments. But not all testbeds are created equal—each type strikes a different balance between real-world fidelity, practical flexibility, and overall scalability.
Physical Testbeds: Maximum Realism, Limited Scale
Physical testbeds are the gold standard when it comes to authenticity. By incorporating actual hardware—PLCs, HMIs, transformers, real-world industrial devices—and supporting native communication protocols like Modbus, DNP3, and IEC 61850, these setups closely mirror operational SCADA environments. This means security controls and attack scenarios unfold as they would in the field, providing invaluable high-fidelity insights.
However, realism comes with a hefty price tag. High costs and logistical challenges can limit expansion, making it difficult for researchers to scale out or modify testbeds quickly. Moreover, certain physical limitations mean that replicating large, complex networks may be impractical outside well-funded industry or government labs.
Virtual Testbeds: Flexible, Scalable, but with Boundaries
Virtualization offers security researchers a more agile and scalable platform. By leveraging software suites like SCADASim or GridLAB-D, you can spin up full digital twins of SCADA networks—complete with configurable attack simulations like spoofing, DoS, or MITM. Virtual testbeds can be rapidly deployed, reconfigured, or cloned, making them ideal for large-scale or scenario-based testing without the upfront investment in hardware.
While virtual testbeds deliver on flexibility and scalability, they’re not without trade-offs. Certain low-level interactions—especially timing nuances or hardware-specific behaviors—tend to be abstracted away or simulated, reducing overall fidelity. This makes it challenging to capture some real-world attack vectors or responses that hinge on physical quirks.
Hybrid Testbeds: The Best of Both Worlds (at a Cost)
Hybrid testbeds attempt to bridge the gap between realism and versatility. By combining elements of both physical hardware and virtualization, they allow you to emulate entire networks while anchoring key nodes or processes to actual devices. This enables research into attack surfaces that span software and the physical layer (e.g., evaluating the impact of DoS attacks on real sensors or actuators), without the need to replicate an entire facility.
In practice, hybrid testbeds provide excellent fidelity for targeted studies and moderate scalability, but typically demand increased investment in both setup and ongoing maintenance. Interfacing between real and virtual components can also introduce complexity, and expanding the system may still be limited by available hardware resources.
Ultimately, choosing the right testbed model depends on your research objectives:
- For deep dives into hardware vulnerabilities or realistic incident response drills, physical or hybrid testbeds offer unmatched insight.
- For rapid experimentation, broad scenario coverage, or budget-conscious projects, virtual testbeds provide a flexible path forward.
By understanding the trade-offs between fidelity, flexibility, and scalability, cybersecurity teams can select or design SCADA testbeds that best support their security goals.
Datasets for SCADA IDS Evaluation
When it comes to testing and benchmarking intrusion detection systems (IDS) in critical infrastructure sectors like power, gas, and water, several publicly available datasets stand out—each with its own focus and quirks:
- Morris Datasets: Developed specifically for power and gas OT environments, these datasets offer network and field device data capturing both normal operation and attack scenarios. Early iterations focus on power system events, while later versions add Modbus protocol data from gas pipeline testbeds, giving researchers options to assess how well security tools detect protocol-specific anomalies.
- UNSW-NB15: Created by the University of New South Wales, this is a comprehensive network security dataset featuring a variety of modern cyber attack patterns—including reconnaissance, exploits, worms, fuzzing, and denial-of-service—making it widely used for IDS training and evaluation, despite its duplicated entries in training sets.
- Modbus TCP Traffic (Lemay & Fernandez): This resource zeroes in on Modbus communications in SCADA systems, simulating genuine control channel activity alongside attack behaviors. It’s a solid pick for those working on Modbus-aware detection capabilities.
- KDD99 and NSL-KDD: Long relied upon for evaluating network intrusion detection, these datasets simulate multi-protocol network traffic and a range of attack types. NSL-KDD improves on KDD99 by removing redundant entries, making it better suited for training robust models.
- Water System Logs (Arnold): For those focusing on water utilities, there’s a specialized dataset capturing a month’s worth of operational logs, including temperature, water flow, inflow, and outflow—offering a chance to test anomaly detection against realistic process data.
These data sources are mainstays in the IDS research community, helping security teams fine-tune analytics and sharpen their response to cyber threats targeting SCADA environments.
Interoperability: Proprietary vs. Standardized Protocols
A major challenge in SCADA environments stems from the mix of communication protocols in play. Many older systems rely on proprietary protocols—like Modbus-RTU, Profibus, or Conitel—which are designed by specific vendors and often only communicate seamlessly with their own hardware. This can create isolated “walled gardens,” where integrating equipment from different manufacturers turns into a technical headache or, in the worst case, is outright impossible.
On the other hand, moving toward standardized and open communication protocols—such as OPC UA or DNP3—breaks down those walls. Standardized protocols are intentionally built for interoperability, making it far easier to mix and match devices from different brands, expand the network as needs evolve, and avoid being locked into a single vendor’s ecosystem. The results are increased flexibility, smoother upgrades, and more resilient operations that can adapt as the industrial landscape changes.
IEC 60870: Powering Communication Across Distances
When it comes to managing power plants scattered across vast regions, IEC 60870 stands as a critical international standard. At its core, IEC 60870 enables reliable and standardized communication between control centers and remote terminal units (RTUs), no matter how geographically separated those sites might be.
Key features of IEC 60870 include:
- Interoperability: The standard ensures different vendors’ equipment can talk to each other, simplifying integration and operation. Vendors typically supply interoperability documentation to help configure communications between control centers and remote units seamlessly.
- Multicast Communication: IEC 60870 supports multicast capabilities, so information can reach multiple devices simultaneously—a necessity in large-scale power distribution networks.
- Event Tracking and Timestamping: When a control center sends data to an RTU, the RTU attaches a timestamp once it receives the application layer message. This process enables accurate sequencing of events and facilitates historical analysis should engineers need to review past incidents.
- Focus on Integrity: While IEC 60870 hasn’t traditionally included robust authentication controls (a noted security gap when compared to newer protocols), it does provide measures for maintaining data integrity between endpoints.
In short, IEC 60870 lays the groundwork for secure, organized, and interoperable communication, making it possible to monitor and control equipment distributed across cities, countries, or entire continents.
.
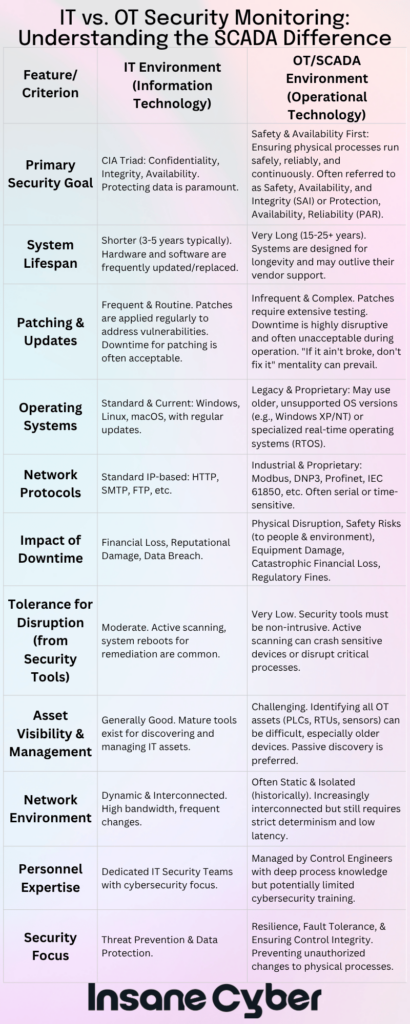
Frameworks for Choosing AMI Communication Technologies
Selecting the right communication technology for advanced metering infrastructure (AMI) in smart grid environments isn’t a matter of guesswork—it requires a structured evaluation. Common frameworks assess technologies based on factors such as frequency spectrum usage, data throughput, coverage area, latency, and reliability in noisy environments.
Some practical approaches include:
- Establishing Criteria Matrix: Stakeholders often build a comparison matrix that ranks options (like WiMAX, Zigbee, cellular, RF mesh, and Power Line Communication) using weighted criteria: spectrum licensing requirements, data rate suitability for metering data volumes, geographic reach (urban vs. rural), integration complexity, and resilience to interference.
- Field Trials and Pilot Testing: Running pilot deployments with leading candidates, such as WiMAX and Zigbee, allows organizations to directly measure performance under actual environmental conditions, considering latency, reliability, and ease of maintenance.
- Cost-Benefit Analysis: Factoring in installation, operation, and long-term maintenance costs ensures that the chosen technology lines up with both technical and financial targets.
- Scalability and Interoperability Assessments: Compatibility with existing infrastructure and future expansion needs are core considerations—protocol support, device interoperability, and vendor ecosystems come to the fore.
- Security Evaluation: Each technology is also scrutinized for its security features, such as built-in encryption, authentication mechanisms, and resilience to known communication-based threats.
By systematically applying these frameworks, utilities and security architects can make informed, risk-mitigated decisions that align with operational requirements and long-term smart grid goals.
Trends in DTL and IDS Research for ICS Since 2015
Since 2015, research into Domain Transfer Learning (DTL) and Intrusion Detection Systems (IDS) for industrial control systems (ICS) has seen a significant evolution. Earlier papers largely focused on traditional IDS methods—think signature-based or rule-based approaches—while more recent work has been driven by the surge in machine learning and AI.
Researchers have begun to blend DTL techniques specifically with IDS solutions to tackle the unique challenges of ICS and SCADA environments. This hybrid approach enables detection algorithms to adapt across different industrial domains, where labeled data is scarce and systems vary widely in configuration. Recent studies delve deep into the practical methods for successfully transferring threat detection models between unrelated plants or sectors—sometimes using benchmark datasets provided by organizations like the ICS-CERT (https://www.cisa.gov/ics) or MITRE (https://attack.mitre.org/matrices/ics/).
Much of this work now falls into three broad buckets:
- Foundational overviews that lay the groundwork for understanding both DTL and IDS concepts in industrial networks.
- Exploratory papers comparing the strengths and weaknesses of standalone DTL or IDS technologies in real-world settings.
- Advanced studies that analyze and benchmark DTL-infused IDS, offering step-by-step evaluations, performance metrics, and real implementation case studies relevant to SCADA protections.
All in all, the literature has shifted from basic introductions toward in-depth, domain-specific approaches that reflect the growing complexity—and interconnectedness—of modern industrial cyber defenses.
How SCADA-Based Operator Support Systems Help Forecast Power Plant Equipment Faults
Operator support systems built on SCADA platforms don’t just monitor—they enable proactive fault forecasting for critical power plant equipment. By continuously collecting and analyzing real-time sensor data from turbines, generators, pumps, and other assets, these systems can spot subtle changes in performance or deviations from expected operation long before a problem triggers alarms.
Here’s how the process typically works:
- Data Collection: SCADA systems aggregate massive streams of sensor readings—vibration, temperature, pressure, flow rates, and more—from across the plant.
- Intelligent Analysis: Advanced algorithms analyze this data looking for patterns or trends that often precede equipment failures, such as increasing vibration in a bearing or gradual temperature rise in a transformer.
- Early Warning Alerts: When the system detects anomalies outside predefined thresholds, it generates alerts for operators. This early notification gives the maintenance team a critical head start—sometimes hours or even days—to address issues before they escalate to costly downtime or safety hazards.
- Decision Support: Some platforms incorporate predictive modeling tools or machine learning to refine their predictions over time, helping prioritize maintenance activities and resource allocation effectively.
In practice, forecasting faults with operator support systems means moving from reactive to predictive maintenance—a huge advantage for reliability, safety, and cost savings in power generation.
Forensic Imaging of Embedded Systems: Tools and Approaches
Embedded systems present unique challenges for forensic analysis, but a handful of specialized tools and methodologies have emerged to address these obstacles. One widely-adopted technique is leveraging JTAG (Joint Test Action Group) interfaces—also referred to as boundary-scan technology—to extract memory contents directly from chips. With a JTAG connection, forensic analysts use hardware debuggers to access and image flash, EEPROM, or RAM, often bypassing higher-level protections.
Other serial interfaces, like UART or SPI, can also be invaluable. These provide additional entry points for acquiring firmware and configuration data, particularly when standard network or file system access is unavailable. For environments where invasive chip-off techniques are feasible, analysts may physically remove memory modules for direct imaging.
Additionally, open-source and commercial tools such as OpenOCD, Bus Pirate, and specialized chip readers simplify connecting to and imaging a wide variety of embedded platforms. The key is thorough documentation and testing—since embedded systems are notoriously sensitive, care must be taken to avoid altering volatile evidence during acquisition.
Limitations of Widely Used Cybersecurity Datasets for SCADA
Even with all these tools, detection and response are only as strong as the data and threat intelligence you rely on. Unfortunately, many widely-used cybersecurity datasets come with significant blind spots when it comes to protecting SCADA environments.
General-Purpose Databases Miss the Mark: Repositories like NVD (National Vulnerability Database) and CVE (Common Vulnerabilities and Exposures) are invaluable for cataloging IT vulnerabilities, but they often lack the level of detail and focus needed for specialized SCADA and OT threats. Many critical vulnerabilities unique to industrial protocols or hardware either appear late or not at all.
KDD99 and Its Shortcomings: The KDD99 dataset has long been a mainstay for intrusion detection testing, but it was never designed for the nuances of industrial control systems. It’s bulky—often only a small fraction is used for realistic testing—and riddled with redundant entries, making it less effective for training detection systems. This “noise” not only ramps up computational costs but also hampers learning accuracy.
NSL-KDD: Incremental Improvements, Persistent Gaps: While NSL-KDD was created to address some of KDD99’s issues, such as duplicate records, it’s still rooted in generic IT scenarios. It doesn’t capture the distinctive traffic patterns, devices, and operational nuances found in SCADA networks.
DARPA: Out of Step with Modern SCADA: The DARPA intrusion detection dataset was built from networks that were isolated and not connected to the public internet. This makes its relevance minimal for today’s internet-facing, interwoven SCADA architectures.
The bottom line: Security practitioners working in industrial environments need datasets and threat intelligence attuned to the realities of SCADA—not just relabeled IT data. Without targeted datasets, even the best detection tools may overlook attacks lurking in the industrial shadows.
Unsupervised Learning Algorithms for Anomaly Detection in IDS
When it comes to spotting threats that might slip past signature-based tools, several unsupervised learning algorithms have carved out a name for themselves in anomaly detection—particularly within Intrusion Detection Systems (IDS) for SCADA environments. These models don’t require labeled attack data; instead, they learn what “normal” behavior looks like, and then flag deviations that could signal a problem.
Some commonly used unsupervised approaches include:
Local Outlier Factor (LOF): LOF assesses the local density of data points. In short, it identifies anomalies by checking which network activities are isolated or far removed from the usual clusters of behavior. If a device or user operates in a way that’s statistically different from its neighbors, LOF gives it a high anomaly score.
Connectivity-Based Outlier Factor (COF): Building on LOF, COF takes into account the chaining distances within groups of data. An activity might seem normal at a glance but, if it’s loosely connected compared to others in its chain, COF will highlight it as suspicious.
Local Correlation Integral and LoOP (Local Outlier Probability): These techniques further refine detection by assessing how correlated a data point is with its surroundings, and then assigning a probability score to its “outlierness.” This helps reduce noise and pinpoints activity that’s statistically improbable given usual network traffic.
Together, these algorithms enable anomaly detection platforms to establish—and constantly refine—a baseline of expected SCADA network behavior. When new activity falls outside those patterns, these tools help raise alerts on potential zero-day or novel attacks that would slip by less adaptive systems.
Security Misconfiguration: Common Pitfalls in SCADA Software
Security misconfiguration remains a lurking threat within SCADA and industrial environments. It’s not just about missing patches—these issues often hide in plain sight, waiting to be exploited by attackers looking for the path of least resistance. Let’s look at some of the most common—and dangerous—ways software systems can stumble:
- Weak or Missing Encryption: Sensitive data traversing SCADA networks should always be encrypted in transit and at rest. If encryption is absent, weak, or relies on outdated algorithms, attackers can easily intercept and read potentially mission-critical information.
- Predictable or Insufficient Randomness: Randomness matters more than you might think. When software relies on weak or predictable random number generation (for things like session tokens or cryptographic keys), attackers may guess those values, opening the door to session hijacking or unauthorized access.
- Acceptance of Unverified Data: Software that fails to validate the origin or authenticity of data is at risk of ingesting malicious commands or spoofed inputs. For instance, a lack of proper checks can allow attackers to establish or hijack sessions—often called “session fixation”—to blend in as legitimate users.
- Lax Password Practices: Easy-to-guess, weak, or default passwords are still a leading cause of breaches. If a SCADA system doesn’t enforce strong password policies (think complexity, rotation, and blocking repeated guesses), privilege escalation becomes trivial. Even worse, hard-coded or unchanged vendor-provided credentials are like leaving a spare key under the mat.
- Improper Access Controls: Not all users (or processes) should have access to all resources. When access controls are too broad or poorly enforced, attackers who gain a foothold can move laterally, access restricted machinery, or manipulate sensitive data undetected.
- Faulty Authentication Mechanisms: Systems that don’t rigorously verify user identities—whether through bypassable login paths, insecure credential handling, or lack of certificate validation—invite both internal misuse and external attacks. Capture-replay attacks (where an attacker reuses valid network traffic to access a system) are a classic example.
- Inadequate Protection Against Brute Force: If failed login attempts aren’t limited or monitored, attackers can repeatedly guess usernames and passwords until they strike gold.
- Unprotected Hashes: Even if passwords are hashed, neglecting to salt those hashes (adding unique data before hashing) exposes the system to rainbow table attacks, potentially revealing user credentials en masse.
These misconfigurations aren’t just theoretical. Each category has enabled significant real-world breaches across industries. Regular security reviews, configuration audits, and leveraging industry best practices like those from NIST, ISA/IEC 62443, and vendor advisories are essential to keep these cracks sealed.
Main Types of SCADA Testbed Design Approaches
Testing and validating the security of SCADA environments is no academic exercise—it’s mission critical. To do that effectively, organizations draw on three main types of testbed designs, each with its own advantages and practicalities:
- Physical Testbeds: This approach uses actual hardware—PLCs, RTUs, networking gear, the real deal—to mimic a live SCADA environment. It delivers the highest fidelity for testing real-world attack and defense scenarios but can be resource-intensive and costly to scale.
- Virtual Testbeds: Here, the focus is on software-based simulations and emulators to replicate SCADA systems and networks. Virtual testbeds are cheaper, safer for disruptive testing, and wildly flexible, making it easy to recreate different architectures or test new threats without risking physical assets.
- Hybrid Testbeds: The best of both worlds, hybrid testbeds mix physical devices with virtual components. This enables highly realistic testing where you can put actual devices through their paces while using simulations to expand coverage or introduce potential attack vectors that would be impractical (or risky) in a fully physical setup.
Choosing the right testbed design depends on your objectives, available resources, and appetite for risk—much like deciding whether to practice firefighting with a candle, a smoke machine, or a real blaze.
Key Criteria for Evaluating SCADA Security Testbeds
Designing or selecting an effective SCADA testbed is a foundational step for anyone aiming to evaluate or improve security solutions in OT environments. Not all testbeds are created equal, and a solid evaluation hinges on several critical factors:
- Reproducibility: The testbed setup should be easily repeatable, enabling other researchers or security professionals to replicate results and validate findings.
- Scalability: An ideal testbed accommodates a wide range of SCADA and ICS devices, protocols, and configurations—without requiring a complete overhaul as new components are introduced.
- Fidelity to Real-World Environments: The closer the testbed mimics the physical devices and configurations of actual SCADA deployments, the more valuable the insights. This includes using genuine hardware when possible and reproducing real processes.
- Process and Attack Simulation: Effective testbeds must simulate real-time process workflows and support a range of attack scenarios, offering a realistic environment for testing both defenses and threat vectors.
- Protocol Diversity: Since industrial environments use a mix of protocols (Modbus, DNP3, IEC 61850, among others), testbeds must support multiple protocols to provide comprehensive coverage.
- Cost Efficiency: Finally, a testbed needs to be affordable enough that organizations (large and small) can implement, maintain, and evolve it as threats—and technology—change.
The right testbed strikes a balance between real-world accuracy, flexibility, and practicality, forming the backbone of any credible SCADA security evaluation program.
Why CWE, CVE, NVD, and US-CERT Matter for SCADA Vulnerability Intelligence
But where should you gather trustworthy vulnerability intelligence for SCADA? Databases like CWE, CVE, NVD, and US-CERT are industry mainstays for a reason:
- Unmatched Coverage: The National Vulnerability Database (NVD) captures a broad array of SCADA-related vulnerabilities, many of which are flagged either by vendors themselves or organizations like US-CERT. This ensures you’re not missing critical threats that could impact your environment.
- Depth and Detail: These resources go beyond simply listing vulnerabilities—they provide important context, such as which industries and geographies are affected, severity ratings tied to real-world impact, and relevant technical details mapped to a standardized taxonomy.
- Data Synchronization: By leveraging databases that tightly integrate with each other (CVE entries sync with NVD, which references CWE categorizations, and US-CERT keeps pace with all of the above), analysts avoid duplications and gaps. This offers a “single source of truth,” making tracking, analysis, and response more straightforward.
- Industry Alignment: These databases are widely recognized and referenced across cybersecurity, making them an essential foundation for both compliance efforts and incident response.
With these sources, SCADA teams are far better equipped to keep sight of the complete threat landscape—rather than hunting for disparate vulnerability clues scattered across obscure channels.
How SCADA Vulnerabilities Are Identified and Filtered
So, where do all these SCADA vulnerabilities come from? The process for tracking them down and sorting them out is (thankfully) more organized than rummaging through a haystack with a metal detector.
Here’s how the vulnerabilities are hunted, gathered, and organized:
Tapping Trusted Sources: Researchers turn to primary repositories like the Common Vulnerabilities and Exposures (CVE), National Vulnerability Database (NVD), Common Weakness Enumeration (CWE), and alerts from the US-CERT. These databases provide comprehensive coverage of known vulnerabilities, both historical and newly discovered—think of them as the Rosetta Stone for security flaws.
Data Extraction and Processing: The raw vulnerability data is usually pulled in bulk, often in formats like JSON directly from the NVD feed. To make sense of this data, power tools such as Microsoft Excel (or your favorite data wrangling app) are used to slice, dice, and filter the mountain of information.
Filtering for SCADA Relevance: Not all vulnerabilities are created equal—or relevant to SCADA. To filter out the noise, searches are narrowed using keywords like “SCADA,” “PLC,” “RTU,” “HMI,” “Historian,” as well as vendor names like Siemens, Omron, or Rockwell Automation. This ensures the end result is laser-focused on vulnerabilities that specifically impact industrial and SCADA systems.
Why Use These Databases?
Coverage and Accuracy: NVD and its synchronized partners track virtually every major vulnerability impacting SCADA products, including comprehensive impact metrics.
Detail and Relevance: These databases don’t just list the bugs—they connect each vulnerability to affected products, vendors, and even the industries or geographies at risk.
By pulling from these robust public sources and tailoring the search to SCADA-specific technologies, researchers can assemble a reliable, up-to-date picture of the threat landscape.
IEC 61850: Authentication and Integrity Considerations
When it comes to authentication and integrity, IEC 61850 offers some built-in mechanisms—but with limitations. The standard does support authentication features, allowing devices on the network to verify the identities of those attempting to communicate. However, integrity protection (ensuring that messages aren’t tampered with in transit) is noticeably less robust. At the protocol level, IEC 61850 was not originally designed with strong data integrity controls, which means critical configuration changes or command messages could, in theory, be altered without detection unless additional protections are put in place.
For organizations deploying IEC 61850, it’s essential to layer in supplementary security controls, such as network-level authentication, encrypted communication tunnels, or application-layer integrity checks, to address these gaps and help safeguard the authenticity and trustworthiness of system messages.
Host Intrusion Detection for Industrial Environments
Host intrusion detection systems (HIDS), such as OSSEC, bring a crucial layer of security monitoring directly to critical endpoints within industrial settings. In SCADA and OT environments, HIDS monitor file integrity, system logs, and configuration changes on servers, engineering workstations, and HMIs. This local visibility is especially valuable for detecting unauthorized access, malware, or attempts to alter essential configuration files—risks that network-only solutions might miss.
HIDS tools can generate real-time alerts on suspicious activities, such as failed logins, privilege escalation attempts, or unexpected changes to control logic files. This empowers incident response teams to react quickly, isolate compromised hosts, and limit potential damage. When integrated with other monitoring platforms (like SIEM), host intrusion detection provides context-rich data that makes it easier to trace attack paths and understand root causes.
While deploying HIDS in OT environments requires careful planning—to avoid resource contention or interference with operations—modern lightweight agents and passive monitoring modes are increasingly being adopted. Overall, HIDS complements network-based defenses by shining a spotlight on activity occurring directly on the most sensitive devices within the SCADA ecosystem.
Honeypots: Luring in SCADA Attackers
Beyond the usual security toolkit, honeypots—like the widely-used Conpot—play a unique role in defending SCADA environments. A honeypot is essentially a decoy system that mimics genuine SCADA devices, protocols, and network behaviors, deliberately designed to attract attackers.
Why use them?
- Real-World Threat Intel: By observing how attackers interact with these “fake” devices, security teams gain firsthand insight into tactics, techniques, and procedures (TTPs) aimed specifically at SCADA systems. It’s like setting a clever trap—and then quietly learning from every move the adversary makes.
- Early Warning System: Interactions with honeypots can alert defenders to new threats or attack trends targeting the organization or industry, providing precious early warnings.
- Safe Analysis: Since honeypots are isolated from production environments, they allow incident response teams to study malware, attempts at exploitation, or unauthorized access attempts without risking actual critical infrastructure.
Modern SCADA honeypots, such as Conpot, can emulate a range of industrial control protocols (Modbus, S7, BACnet, and more). This versatility makes them valuable for both research and practical defense, uncovering vulnerabilities that might otherwise stay hidden.
Effective SCADA Cyber Monitoring Techniques
Beyond tools, effective monitoring hinges on robust processes and skilled personnel:
- Network Segmentation: Dividing the SCADA network into distinct security zones limits the blast radius of an attack. Traffic between zones should be strictly controlled and monitored. Implementing Demilitarized Zones (DMZs) between IT and OT networks is a common best practice.
- Continuous Monitoring and Vigilance: SCADA environments require 24/7 monitoring. This involves not just automated alerts but also proactive threat hunting by security analysts who understand the nuances of industrial control systems.
- Protocol-Aware Monitoring: Deep understanding and monitoring of SCADA-specific communication protocols are essential to identify anomalous or malicious commands that could disrupt physical processes. This means going beyond generic traffic inspection—security teams must be fluent in the unique structures and behaviors of protocols like Modbus, DNP3, and IEC 60870-5-104, which are often found in industrial control systems.
By focusing on protocol-level vulnerabilities, defenders can spot subtle manipulations that traditional IT-centric tools might overlook, such as unauthorized command injections or replay attacks. Numerous studies, including industry reviews, highlight that attackers frequently exploit weaknesses in these communication protocols to gain unauthorized access or tamper with industrial operations. As the complexity of ICS networks grows, protocol-aware monitoring remains a foundational pillar for detecting evolving cyber threats in critical infrastructure.
Intrusion Detection for SCADA Protocols Like IEC 60870-5-104
Detecting threats in SCADA environments isn’t a one-size-fits-all endeavor—especially when it comes to specialized communication protocols like IEC 60870-5-104 commonly used in power systems. Standard network security tools often lack the granular awareness needed to spot protocol-specific anomalies that could signal an attack or misconfiguration.
To address these nuances, effective strategies include:
- Protocol-Deep Inspection: Intrusion detection systems should be capable of parsing and understanding IEC 60870-5-104 traffic—not just basic headers, but the actual command and data structure within messages. This allows for detection of abnormal command sequences and unexpected data flows that might indicate malicious activity.
- Multiattribute Analysis: Effective solutions look beyond simple signature- or rule-based models. They weigh multiple attributes—such as message frequency, command types, source/destination addresses, and timing patterns—to distinguish benign operational changes from suspicious behaviors. Machine learning-based analysis can enhance this approach, adapting to evolving network patterns.
- Behavioral Baselines per Protocol: Establishing a protocol-specific baseline for IEC 60870-5-104 traffic helps highlight subtle deviations. For example, if a new type of control command suddenly appears on a typically ‘read-only’ segment, an alert can be triggered.
- Integration with SIEM and Anomaly Detection: Feeding protocol-aware telemetry into your SIEM or anomaly detection platform can surface vulnerabilities missed by generic monitoring. This is especially useful for legacy equipment where patching isn’t always possible.
All these measures combine to provide tailored, proactive monitoring—catching attacks that might fly under the radar of traditional IT-focused security solutions.
Simulating Attacks on DNP3 Protocols in SCADA Systems
To truly understand the risks facing SCADA environments, security teams often perform simulated attacks—sometimes called red teaming—on critical communication protocols like DNP3. These simulated exercises are invaluable in identifying weaknesses before real adversaries can exploit them.
Here’s how such simulations are typically carried out:
Testbed Environment: Create a replica of your SCADA environment in a controlled lab, mirroring the actual network architecture, PLCs, HMIs, and communication links. This ensures testing won’t disrupt live operations.
Protocol Fuzzing: Leverage specialized fuzzing tools to send malformed or unexpected data packets over the DNP3 protocol. This technique helps uncover vulnerabilities in how devices handle unexpected or malicious commands.
Replay and Injection Attacks: Use packet capture and analysis tools (like Wireshark) to replay legitimate DNP3 traffic, then modify or inject malicious commands to observe how connected devices and monitoring systems respond.
Monitoring Response: Carefully track how detection systems—such as IDS/IPS platforms with deep packet inspection—identify and alert on anomalous DNP3 activity.
By regularly simulating protocol-specific attacks, organizations can pinpoint security gaps, validate the effectiveness of their monitoring controls, and ensure their teams are prepared for real-world threats.
Behavioral Analysis: Focus on understanding what constitutes normal operational behavior. This allows for the detection of subtle deviations that might indicate a compromised system or an insider threat.
Configuration Change Monitoring: Unauthorized changes to PLC logic, HMI configurations, or network device settings can be early indicators of an attack. Implementing systems to detect and alert on such changes is vital.
PLC Forensics and Investigation:
Analyzing programmable logic controllers (PLCs) for forensic purposes involves a specialized set of techniques distinct from traditional IT forensics. Unlike conventional endpoints, PLCs store critical operational data in memory modules and have unique architectures. A forensic process typically includes:Firmware and Configuration Extraction: Securely capturing the current firmware, ladder logic, and configuration files from the PLC without altering device state. This often requires vendor-specific tools and interface cables.
Log and Audit Trail Analysis: Examining event logs, diagnostic information, and change histories available within the PLC to trace unauthorized access, logic changes, or anomalous behaviors. In some cases, logs can reveal precisely when and how a configuration was altered.
Memory Imaging: In select scenarios, creating a bit-by-bit copy of PLC memory modules may be necessary to reconstruct operational states or recover deleted logic.
Cross-Referencing with Network Data: Correlating PLC activity with network monitoring data helps pinpoint command sources and tie activity to specific workstations or users. This holistic approach can uncover lateral movement or malicious automation.
Chain of Custody and Preservation: It’s critical to maintain a strict chain of custody and use write-blocking techniques to preserve evidentiary integrity, in line with forensic best practices.
PLC forensics is a rapidly evolving field, as attackers increasingly target industrial control equipment and as regulatory requirements tighten regarding incident investigations. Having a well-defined forensic readiness plan specific to OT environments ensures faster and more reliable root cause analysis following an incident.
Secure Remote Access Protocols: Enforce multi-factor authentication (MFA), use VPNs with strong encryption, and limit remote access to only what is necessary and for the shortest duration required. All remote sessions should be logged and monitored.
Principle of Least Privilege (PoLP): Grant users and applications only the permissions they absolutely need—nothing more, nothing less. This minimizes the risk of accidental or malicious changes.
Rule-Based Access Controls: Implement granular, rule-based access controls for sensitive devices and systems. Ensure that system installations do not default to privileged modes.
Authentication, Authorization, and Accounting (AAA): Leverage authentication frameworks like RADIUS (Remote Authentication Dial-In User Service) with IEEE 802.1x and extensible authentication protocols for robust user verification. Salting passwords further strengthens user authentication.
Remote Access Gateways: Deploy VPN gateways to manage and secure all remote connections into your network, especially for critical SCADA and ICS infrastructure.
Physical Security Tokens: Consider the use of hardware security tokens to control access to sensitive physical areas, adding an extra layer of protection.
By combining strong digital protocols with strict privilege management and physical controls, you can significantly reduce your attack surface and better safeguard critical assets.
Access Control: The Gatekeeper of SCADA Security
Weak or poorly configured access controls are a recurring culprit in SCADA breaches. When access permissions aren’t carefully managed, attackers (or even careless insiders) can end up with the keys to the kingdom—gaining unauthorized entry to critical systems, data, or even the ability to manipulate operations.
Effective access control in SCADA relies on a trio of essential mechanisms—often referred to as the “AAA” framework:
- Authentication: Ensures that only verified users or devices can attempt to access the system. Think of it as the security guard checking IDs at the door—passwords, smart cards, and biometrics are typical tools.
- Authorization: Determines what each user or device is actually permitted to do once inside. Just because someone works at a facility doesn’t mean they should have access to every control panel—least privilege is the rule of thumb.
- Accountability: Tracks and logs every access attempt and action taken, making it possible to audit activity and trace any suspicious behavior back to a specific user or process.
When any part of this chain is weak—say, a shared password, overly broad permissions, or missing audit trails—critical resources become exposed. The result? Attackers can disrupt operations, steal sensitive data, or cover their tracks without detection. Robust, regularly reviewed access control policies are fundamental to defending SCADA environments against these risks.
- Regular Security Audits and Penetration Testing: Independent security assessments, including penetration tests specifically designed for OT environments (and conducted with extreme care), can help identify blind spots and validate the effectiveness of existing controls.
SCADA Testbeds: Safe Environments for Security Validation
A SCADA testbed is a specially isolated environment designed to safely replicate the components and behavior of a live industrial control system. These testbeds allow organizations to rigorously evaluate security tools, practices, and incident response procedures without risking disruption to actual production networks.
By simulating the real-world conditions of PLCs, RTUs, HMIs, and network traffic, testbeds become invaluable for:
- Testing patches and security updates before deployment, ensuring compatibility and safety.
- Safely running penetration tests and red-team exercises to discover vulnerabilities in a controlled setting.
- Training staff on incident response, forensic analysis, and system recovery—building vital hands-on skills without business impact.
- Validating the effectiveness of anomaly detection, EDR solutions tailored for OT, and network segmentation policies.
In short, SCADA testbeds provide a risk-free playground for pioneers and defenders alike, ensuring that security strategies are robust, effective, and tailored for the complex realities of industrial control networks.
- Risks of Real-Time Security Testing in SCADA Environments:
Conducting real-time security tests on active SCADA systems presents unique challenges. Unlike traditional IT environments, disruptions—even momentary—can have serious repercussions, from production downtime to compromised safety. Testing live systems runs the risk of triggering faults or crashes in sensitive industrial processes, potentially halting operations or damaging equipment. As a result, organizations must carefully plan and often simulate such tests in isolated or replica environments to avoid jeopardizing critical functions and business continuity. - Incident Response Plan: Incident Response Plan: Be Ready Before Trouble Strikes
Have a well-defined and practiced incident response plan specifically for SCADA incidents. This plan should outline roles, responsibilities, communication channels, and procedures for containment, eradication, and recovery.
Go beyond just a checklist—develop a forensic taxonomy of your SCADA assets and processes so you know exactly what’s at stake and where to look first when something goes wrong. Map out critical devices, communication flows, and dependencies in advance. Incorporate lessons learned from real-world incidents and tabletop exercises to refine your approach over time. Assign clear responsibilities for evidence collection and documentation, ensuring that every response action is traceable and defensible. Regularly review and update your plan as new technologies and threats emerge, so your team isn’t caught off guard when minutes matter.
- Threat Intelligence Integration: Leverage industrial-specific threat intelligence feeds to stay informed about the latest TTPs (tactics, techniques, and procedures) used by adversaries targeting SCADA systems.
Conducting SCADA Network Forensics for Protocols Like PCCC
When it comes to investigating incidents in SCADA environments, the process gets particularly nuanced with industrial protocols like PCCC (Programmable Controller Communication Commands). Effective network forensics in this context means going well beyond traditional packet captures.
Here’s what a robust approach should look like:
- Deep Packet Inspection (DPI): Use specialized OT network forensics tools like Nozomi Networks or Claroty that understand the PCCC protocol, allowing analysts to reconstruct command sequences, inspect payloads, and spot unauthorized operations.
- Protocol Decoding and Analysis: By decoding PCCC traffic at a granular level, forensic teams can identify suspicious commands (like unauthorized write requests or code uploads) and isolate potentially compromised assets.
- Timeline Reconstruction: Maintain detailed logs of network activity to reconstruct the timeline of events. This helps determine the progression and intent behind anomalous PCCC protocol usage.
- Artifact Preservation: Ensure volatile artifacts (such as session keys, command histories, and device logs) are securely preserved for post-incident analysis or legal proceedings.
- Integration with Threat Intelligence: Correlate forensic findings with OT-specific threat intelligence feeds. Doing so enriches the investigation and helps identify whether observed behaviors match known attacker tactics targeting PCCC or similar protocols.
A knowledge of the protocol’s structure isn’t just helpful—it’s essential. With the right combination of deep protocol awareness, modern forensic platforms, and process discipline, organizations can effectively trace, analyze, and respond to threats hiding in the nooks and crannies of industrial networks like those built on PCCC.
Credential Management: The First Line of Defense
Proper credential management is essential for safeguarding SCADA systems. Weak or default passwords are an open invitation to attackers—far too often, breaches begin with easily-guessed logins left unchanged on critical devices. Every SCADA administrator should make strong password hygiene a foundational security habit, not an afterthought.
Here are actionable strategies to strengthen credential management in SCADA environments:
- Eliminate Default Credentials: Change all vendor-supplied passwords during system setup. Default logins are widely known and frequently exploited by attackers scanning for low-hanging fruit.
- Implement Password Complexity and Rotation: Enforce strong, unique passwords for every account and mandate regular password updates to reduce the risk of compromise over time.
- Salting and Hashing: Protect stored passwords by salting (adding random data) before hashing. This simple step thwarts rainbow table and brute-force attacks by making precomputed hashes useless to adversaries.
- Least Privilege Principle: Restrict user accounts to only the permissions they need for their roles. Disable unused accounts and ensure administrative access is tightly controlled.
- Multi-Factor Authentication (MFA): Wherever possible—especially for remote or privileged access—add an extra layer of verification with MFA. This greatly reduces the risk of unauthorized entry, even if a password is stolen.
Effective credential management isn’t glamorous, but it’s the invisible shield that protects critical infrastructure from countless attacks each day. Coupled with ongoing vigilance and the security practices mentioned above, it dramatically reduces risk…
Advanced Detection Methodologies: Federated Learning & Temporal Pattern Recognition
Modern cyberattack detection in industrial control systems (ICS) is constantly evolving. Two noteworthy methodologies making waves in the field today are federated learning and temporal pattern recognition techniques.
Federated Learning: Unlike traditional, centralized approaches, federated learning enables organizations to collaboratively train anomaly detection models using data distributed across multiple sites—without sharing sensitive operational data externally. This is particularly valuable in industrial contexts where data privacy and regulatory compliance are paramount. The result: smarter anomaly detection (such as for unusual traffic or process behavior) that adapts to unique operational environments while benefiting from collective insights.
Temporal Pattern Recognition: Cyberattacks in SCADA and ICS environments often manifest through unusual sequences or timing of events rather than isolated anomalies. Temporal pattern recognition leverages this by analyzing patterns over time—identifying deviations or suspicious activity based on the expected order, frequency, and timing of commands or data flows. Techniques in this domain help catch subtle, slow-moving threats and insider actions that more static rule-based systems might overlook.
By integrating these advanced methodologies into security operations, organizations can strengthen their ability to uncover both known and novel attacks—well before they lead to operational disruptions or compromise critical infrastructure.
Quantitative Security Evaluation Techniques: From OSINT to Mitigation
For those looking to objectively measure the security posture of SCADA protocols, there are advanced, structured approaches that span from initial reconnaissance to post-mitigation analysis:
- OSINT-Driven Threat Assessment: The process often begins with gathering Open Source Intelligence (OSINT) to uncover publicly available information about the SCADA protocol, including documentation, exposed device fingerprints, and known vulnerabilities. This step helps establish a baseline understanding of exposure and potential attack vectors.
- Vulnerability Scanning and Enumeration: Automated tools and manual methods are employed to scan for weaknesses within protocol implementations—from missing authentication mechanisms to improper command validation. The findings are logged and scored based on severity, providing a data-driven snapshot of protocol risks.
- Attack Simulation and Penetration Testing: Quantitative security evaluation then advances through controlled penetration tests. By simulating attacks, organizations can collect metrics on factors such as exploit success rates, required time to compromise, and system impact, thereby translating technical findings into quantifiable risk levels.
- Scoring Models and Risk Matrices: Frameworks such as the Common Vulnerability Scoring System (CVSS) and custom risk matrices are used to assign numerical values to discovered vulnerabilities. This allows for a prioritized and clearly communicated mitigation roadmap.
- Mitigation Effectiveness Analysis: After countermeasures are applied—like protocol hardening, segmentation, or enhanced monitoring—measurements are repeated. The reduction in vulnerabilities, attack surface, and response time is tracked quantitatively to gauge the success of implemented defenses.
These techniques provide a layered, measurable approach for evaluating—and, importantly, improving—the security of SCADA protocols across their lifecycle.
Harnessing Testbeds for SCADA Cybersecurity Research and Training
Testbeds—realistic, contained environments that replicate SCADA systems—are indispensable tools for advancing both cybersecurity research and workforce development in industrial control systems.
These environments provide a safe space to simulate attacks, test defense mechanisms, and observe how SCADA components respond to real-world threats without risking actual production networks. Researchers can stress-test new detection algorithms, incident response processes, and patch management approaches, generating actionable insights under highly controlled, repeatable conditions.
For education, testbeds enable operators, engineers, and cybersecurity professionals to gain invaluable hands-on experience. By recreating attack scenarios and enforcing remediation steps, participants build practical skills in a consequence-free setting, bridging the knowledge gap that is often left unaddressed by theoretical training alone.
In short, integrating SCADA-focused testbeds into both research and training initiatives fosters a culture of continuous learning and prepares teams to respond confidently to the evolving threat landscape.
Challenges in SCADA Forensic Investigations
Despite advances in monitoring and proactive security, digital forensics in SCADA environments brings its own set of unique hurdles:
- Lack of Standardized Logging: Unlike IT systems, many SCADA devices generate minimal or highly proprietary logs—if any at all. This lack of consistent, detailed event data can make it extremely tough to reconstruct the sequence of events following an incident.
- System Uptime Requirements: SCADA systems often run critical infrastructure where downtime isn’t just inconvenient—it’s outright unacceptable. Pausing or shutting down devices to acquire forensic images can disrupt operations, making traditional investigation techniques a non-starter.
- Proprietary Protocols and Hardware: From Siemens to Schneider Electric, each vendor may use unique protocols, firmware, and device architectures. This diversity means forensic analysts often need specialized tools and training just to access or interpret evidence.
- Volatile Environments: Some key forensic evidence (such as active memory or volatile logs) can be lost with a simple restart or power cycle—and in industrial environments, such resets are not uncommon, intentional or otherwise.
- Chain of Custody and Legal Concerns: As with other sectors, maintaining forensic soundness and a defensible chain of custody is vital—but it gets complicated when dealing with non-standard, real-time systems and a mix of physical and digital evidence.
These challenges highlight the importance of incident preparedness, cross-disciplinary expertise, and ongoing collaboration between IT, OT, and legal teams.
SCADA Testbeds: Analyzing Cyberattack Impact
Realistic SCADA testbeds play a key role in understanding just how disruptive cyberattacks can be in operational environments. By simulating real-world processes—from water treatment to power distribution—these platforms allow security teams to safely launch attack scenarios and measure the resulting fallout without putting actual infrastructure at risk.
- Quantifying Damage: Testbeds like SWaT and PowerCyber make it possible to assess the scale and nature of potential damage, whether to equipment, data integrity, or operational continuity. Analysts can observe how different attack vectors affect process logic, safety controls, and physical systems.
- Scenario-Based Testing: They enable organizations to run through “what-if” scenarios, such as ransomware targeting PLCs or unauthorized changes to HMI configurations, to identify weak points and better prioritize defenses.
- Guiding Mitigation Strategies: Insights from these controlled experiments inform incident response planning and help fine-tune detection rules, ensuring teams know which alarms are noise and which signal real risk.
Using these testbeds as a proving ground, defenders gain practical experience and data-driven confidence—turning lessons learned into better protection for live SCADA systems.
Enhancing SCADA Security with Testbed Encryption
Encryption-based testbeds present a practical path to strengthening SCADA security. By simulating real-world attack scenarios in a controlled environment, operators can evaluate how different encryption schemes perform under pressure—without putting production networks at risk. This hands-on approach makes it possible to:
- Assess Encryption Protocols: Testbeds allow for side-by-side comparisons of encryption options (like TLS or IEC 62351) to ensure they align with industrial communication requirements and don’t introduce unacceptable latency.
- Reveal Weaknesses in Data Flows: During simulated attacks, encrypted testbeds can highlight vulnerabilities in data transmission—whether between PLCs and HMIs or from remote operators into the control network.
- Fine-Tune Key Management: Secure key distribution and rotation are often pain points in OT. Testbeds offer a venue to experiment with automated key management solutions and validate that they work reliably in complex SCADA topologies.
- Evaluate Device Compatibility: Not all legacy devices handle modern encryption well. Test environments help pinpoint integration issues early and develop tailored mitigations.
Integrating insights from these testbed exercises can lead to practical upgrades in operational networks—such as implementing robust encryption for data in transit and ensuring all endpoints are compatible and securely configured.
Enhancing SCADA System Availability with Fault Tolerance
A rock-solid SCADA network isn’t just about keeping the bad guys out—it’s also about staying resilient when things inevitably go sideways. Fault tolerance techniques are at the core of ensuring that even when a hiccup (or a full-blown hardware meltdown) occurs, your control systems remain up and running.
Some practical ways to bake fault tolerance into SCADA environments include:
- Redundant Hardware: Deploying duplicate PLCs, servers, and network components so if one fails, another instantly takes over—think of it as a relay race where someone’s always ready to pick up the baton.
- Failover Protocols: Smart configuration ensures that, upon detecting a failure, systems shift operations to backup modules or routes with minimal interruption. This can be as simple as dual network paths or as complex as hot-swappable control units.
- Data Synchronization: Regular, automatic syncing between primary and secondary systems helps prevent data loss and ensures accurate state recovery in case of a switchover.
- Distributed Architectures: By spreading out critical functions across multiple nodes or sites, you reduce the risk that a single incident takes everything down.
- Continuous Health Checks: Automated monitoring to spot impending hardware or software issues before they trigger a full outage, enabling preemptive maintenance.
By weaving these fault tolerance measures into the fabric of your SCADA network, you not only keep operations humming along through equipment failures but also limit your exposure to cascading disruptions from cyber or physical threats.
SCADA and ICS Cybersecurity Testbeds: An Essential Foundation
It’s not just alerts and audits that power robust defenses—hands-on research, simulation, and operator training play a critical role. Enter the world of testbeds for SCADA and industrial control system (ICS) environments. These purpose-built test platforms allow organizations, researchers, and security teams to safely replicate real-world scenarios, analyze attack techniques, and experiment with response strategies.
Key categories of SCADA/ICS cybersecurity testbeds include:
Operational Technology (OT) Testbeds: Comprehensive platforms that accurately mimic the behavior of industrial processes—think power grids, water treatment plants, or manufacturing lines. These are invaluable for testing how malware or unauthorized commands could impact safety and reliability, and for validating detection tools in as close to real-world conditions as possible.
Cyber-Physical System (CPS) Testbeds: These environments bridge the gap between digital threats and physical processes, allowing researchers to observe how a compromise in the cyber layer (like a PLC or HMI breach) can translate into real-world consequences—everything from power outages to equipment failure.
Virtualized and Cloud-Based Testbeds: For situations where deploying physical hardware isn’t feasible, virtual testbeds recreate ICS/SCADA protocols and components in software. This makes it possible to safely test exploits, develop forensic analysis techniques, and train operators without putting any real infrastructure at risk.
Remotely Accessible Testbeds: Universities and industry consortiums often provide access to controlled testbed environments remotely. This allows global teams to collaborate on attack-and-defense exercises, share new threat intelligence, and hone incident response without logistical hurdles.
Purpose-Specific Testbeds for Forensics and Training: Some platforms focus specifically on post-incident analysis, providing controlled logs and known attack patterns for perfecting forensic skills. Others support ongoing operator training, scenario walk-throughs, and protocol analysis exercises vital for ongoing resilience.
Testbeds like these aren’t merely academic playgrounds—they’re critically important for staying ahead of ever-evolving threats in industrial environments. Combined with real-world monitoring, strong configuration management, and skilled personnel, they form a cornerstone of a modern SCADA cyber defense strategy.
Forensic Analysis: Challenges and Research Needs
Despite major strides in SCADA security, forensic analysis within these environments remains a complex undertaking with unique obstacles still to conquer.
- 24/7 Operations Complicate Evidence Gathering: Unlike many traditional IT systems, SCADA environments must remain operational around the clock. This constant activity makes it extremely difficult to perform live forensic collection—anything that disrupts operations can have serious, real-world consequences.
- Lack of Specialized Forensic Tools for OT: Most forensics platforms are tailored to standard IT, not industrial controls. This leaves investigators without essential capabilities, such as capturing memory dumps or analyzing volatile system data from PLCs and HMIs, at precisely the moments when such information is most valuable.
- Verification of Volatile Data: Since much of the critical forensic evidence in SCADA systems exists only temporarily (in RAM or active session logs), verifying and preserving this volatile data during incidents is a major research gap. The integrity and reliability of such data are essential to reconstructing the timeline of an attack.
- Need for Embedded Forensics Capabilities: There’s a pressing need for vendors to build forensic functionality directly into OT products. This would enable forensic teams to securely and efficiently collect evidence without impairing system performance or jeopardizing uptime.
Leveraging Analytics and Automation
Emerging tech, like automation, data science, and big data analytics, is beginning to offer promising approaches:
- Automated analytic techniques can help sift through vast logs of ICS data, extracting hidden artifacts that often elude manual review.
- Data-driven solutions could enable more rapid, accurate decision-making during incident response—turning overwhelming volumes of sensor and event data into actionable intelligence.
The Path Ahead
Moving forward, more research, cross-industry collaboration, and targeted tool development are needed to:
- Enable safe, live collection of forensic evidence in always-on environments.
- Verify and preserve the integrity of volatile forensic data for legal and operational review.
- Equip security professionals with analytic tools designed for the scale and specificity of SCADA environments.
Without dedicated advances in these areas, incident response and root-cause analysis in industrial settings will continue to lag behind attackers’ tactics.
SCADA Testbeds: Validating Security Controls in a Realistic Environment
One of the most effective ways to ensure the strength of SCADA security controls is by putting them to the test in controlled, lifelike environments. SCADA testbeds—simulated platforms that accurately replicate industrial systems—play a crucial role here. They allow organizations to safely evaluate and refine security mechanisms by mimicking real-world attack scenarios without risking live operations.
Here’s how testbeds support robust security control validation:
- Hands-On Stress Testing: Security teams can deploy proposed firewalls, intrusion detection systems, or other safeguards on the testbed and subject them to a battery of attacks, from malware infections to unauthorized command injections. This reveals whether the controls actually detect or block threats as intended.
- Learning From Real-World Failure Modes: By simulating everything from insider threats to advanced persistent attacks, testbeds highlight potential weaknesses, misconfigurations, or unexpected interactions between systems—insights that aren’t always obvious on paper.
- Tuning and Adaptation: Teams can tweak detection thresholds, response playbooks, and security rules in a setting that mirrors their actual SCADA environment. This ensures that controls aren’t just effective in theory, but also reliable under the specific demands and quirks of operational networks.
- Safe Experimentation: Without risking downtime or safety hazards, even complex or destructive attacks can be replicated. This enables security professionals to learn, adapt, and respond swiftly—building muscle memory for when a real incident occurs.
In short, leveraging SCADA testbeds bridges the gap between proposed cybersecurity solutions and confidence they’ll hold up under fire in a live facility.
The Hidden Risk: Credential Management in SCADA Historians
Mismanaged credentials are a classic Achilles’ heel in SCADA historian databases. When default usernames and passwords are left unchanged—or when weak passwords are used out of convenience—the historian becomes a soft target. Attackers who discover these credentials (often documented in vendor manuals or shared across multiple deployments) can quietly let themselves in.
Once inside, an unauthorized user can access sensitive operational data stored in the historian, including real-time process values, historical trends, and sometimes even system configuration snapshots. The stakes are high: this treasure trove of information may reveal proprietary process details, operational strategies, and even clues for crafting more advanced attacks.
To minimize the risk of information disclosure:
- Replace all default credentials immediately during deployment.
- Use strong, unique passwords that are regularly changed.
- Implement strict access controls and audit all user activities within the historian.
- Integrate historian login with centralized identity management where possible.
Sound credential hygiene is a simple but powerful step toward preventing data exposure—and keeping critical operational secrets out of adversaries’ hands.
Securing Wireless SCADA Systems in Rural Power Grids
Wireless SCADA deployments in rural power grids introduce unique security challenges, owing to their exposure to broader attack surfaces and often limited on-site resources. To shore up defenses for these vital systems, several best practices should be prioritized:
- Encryption for Wireless Communications: All wireless data transmissions should be secured with robust, industry-standard encryption protocols (such as WPA3 or advanced VPN tunneling) to prevent eavesdropping and unauthorized access.
- Strong Authentication Mechanisms: Enforce multi-factor authentication (MFA) for all remote connections, making it far more difficult for attackers to gain unauthorized entry to control systems.
- Hardened Wireless Infrastructure: Regularly update and patch wireless access points and devices. Use secure configurations—disable unused services, change default credentials, and limit signal range to just what’s necessary for operations to minimize external exposure.
- Physical Security Measures: Even in remote locations, critical network components such as radio towers and field devices should be protected with locked enclosures and monitored for tampering.
- Continuous Monitoring: Deploy intrusion detection systems (IDS) capable of monitoring wireless traffic for suspicious activity and integrate alerts with broader network security operations.
- Periodic Security Assessments: Regular risk evaluations—through both internal audits and third-party penetration testing—are essential to identify and close potential vulnerabilities unique to rural and wireless setups.
By layering these protective measures, operators can dramatically reduce the likelihood of unauthorized access or malicious disruption to rural SCADA-controlled power grids.
Forensic Artefacts in Programmable Logic Controllers
When it comes to understanding what’s really happening inside your SCADA ecosystem, few things are more important than being able to extract and analyze the right forensic artefacts from your programmable logic controllers (PLCs). If and when an incident occurs, these digital breadcrumbs can provide vital insights for both incident response and root cause analysis.
Key types of acquirable forensic artefacts from PLCs include:
- PLC Event Logs: Most modern PLCs capture a record of system events, such as firmware updates, logic changes, error states, and even failed login attempts. These logs can help reconstruct a timeline of activity leading up to or during a security incident.
- Logic and Configuration Backups: The current and previous versions of ladder logic, function block diagrams, or other programming paradigms used within the PLC can reveal unauthorized modifications or malicious payloads.
- User Interaction Records: Some PLCs maintain a record of operator actions—think uploads, downloads, and manual overrides. Reviewing this data can highlight unauthorized access or anomalous commands.
- Communication Histories: Forensic acquisition of network communication sessions passing through or originating from the PLC may expose potential lateral movement, C2 activity, or attempts to manipulate field devices.
- Diagnostic and System Snapshots: Many devices support on-demand or scheduled snapshots of their operational state, diagnostic registers, and memory contents—a gold mine for threat hunters looking for volatility or signs of compromise.
Gathering and preserving these artefacts, ideally in a forensically sound manner, is crucial for both ongoing monitoring and post-incident investigations. This holistic approach ensures that even if an attacker leaves little obvious trace, the subtle clues embedded in PLC artefacts can still speak volumes.
Semantic Security Analysis for Power Grid Protection
Semantic Security Analysis:
Traditional security tools often focus on network traffic patterns or known attack signatures. Semantic security analysis takes things further by examining the meaning and context of control commands issued within the SCADA network—especially in critical infrastructure like power grids.Detecting Malicious Control Commands:
Instead of just flagging unusual traffic, semantic analysis scrutinizes the intent behind commands sent to devices such as PLCs and Remote Terminal Units (RTUs). For example, issuing a “trip” command to open a substation breaker during peak demand might be perfectly legitimate as part of load-balancing—but highly suspicious if issued in the middle of the night by an unfamiliar user account.How It Works:
By modeling typical operational workflows (when certain tasks are usually performed, and by whom), semantic analysis tools can spot commands that don’t fit the expected pattern. This allows for the detection of:Out-of-sequence operations,
Contextually inappropriate commands,
Abnormal command parameters,
Actions that could cause unsafe physical states.
Real-World Impact:
Power grid operators benefit from semantic analysis because it flags not just technical anomalies but also potential operational sabotage, providing early warning of attacks that might otherwise slip past conventional monitoring systems.
Seamless integration of these advanced analytics into the incident response workflow helps teams prioritize alerts and reduce noise, ensuring that real threats receive rapid attention.
Harnessing Automation and Big Data for SCADA Forensics
Automation, data science, and big data analytics are game-changers for forensic investigations in SCADA environments. Collecting and analyzing massive volumes of industrial data—such as network traffic, system logs, and control commands—was once painstakingly manual and slow. Today, automation rapidly sifts through this data mountain, flagging suspicious patterns and changes that human analysts might overlook.
Data science techniques, like anomaly detection models and correlation analysis, help identify subtle clues buried in operational data—artifacts that could point to the root cause, timeline, and scope of security incidents. Machine learning algorithms can go a step further, surfacing previously unknown attack behaviors and offering early warnings based on historical trends.
Big data platforms like Splunk and ELK Stack make it feasible to ingest, query, and visualize years of SCADA event histories in seconds. This accelerated analysis not only improves incident response but also supports more informed decision-making, turning forensic data into actionable insights for preventing future compromises.
Key Considerations for Selecting a SCADA Testbed in Cybersecurity Research
Not all SCADA testbeds are created equal, and choosing the right one for cybersecurity research can make a major difference in both the quality of your findings and your team’s sanity. So, before you jump in and start plugging in hardware or spinning up virtual environments, here’s what you need to think about:
Fidelity vs. Flexibility:
Are you aiming for a near-real-world replica with actual industrial hardware, or do you need a flexible, cost-effective environment that lets you rapidly try out different scenarios? Physical testbeds offer high fidelity—real devices, real protocols, real consequences—but they can be expensive and difficult to scale. Virtual or hybrid testbeds provide more flexibility and lower costs, though sometimes at the expense of realism. Decide which trade-off better serves your research goals.Supported Protocols:
SCADA isn’t a one-size-fits-all world. Make sure your testbed supports the communication protocols your research demands—think Modbus TCP/IP, DNP3, IEC 61850, OPC UA, and so on. Some environments only cover the basics, while more advanced ones allow you to mix and match, even emulating fieldbus I/O for deeper attack experimentation.Attack and Defense Capabilities:
Can the testbed simulate relevant cyberattack scenarios such as Man-in-the-Middle (MITM), denial-of-service (DoS), unauthorized access, and command injection? Likewise, does it allow you to safely practice and validate defensive strategies, like patching, anomaly detection, and incident response, without risking production systems?Integration and Scalability:
Consider how easily the testbed can integrate with both real and simulated devices. If your research requires scaling up—maybe modeling an entire plant or utility grid—look for environments that support this without requiring you to remortgage your future.Cost and Accessibility:
Let’s face it: robust physical testbeds with all the bells and whistles can rival the cost of a small spaceship. Be realistic about budget constraints, and check whether there are open-source options or platforms supported by academic consortia. Some environments are purpose-built for academic use, while others are proprietary (and often prohibitively expensive).Scenario Customization:
A good testbed should let you customize scenarios—whether you’re modeling attacks against a water treatment plant, a power grid, or a hybrid manufacturing setup. Look for testbeds that don’t lock you into a narrow use case.Live Data and Hardware-in-the-Loop:
Need to go hands-on? Some hybrid testbeds provide options for connecting real PLCs, HMIs, or other field devices right alongside simulated components—a big plus if your research depends on validating outcomes in environments that closely mimic operational realities.
In short, the right SCADA testbed for cybersecurity research depends on balancing realism, flexibility, protocol support, cost, and your specific attack/defense scenarios. Take inventory of your requirements before you commit, and don’t be afraid to get creative—sometimes the best environment is a hybrid, purpose-built mix.
Real-Time Cyber-Physical System Testbeds: A Crucial Tool
A key resource now gaining traction in the world of SCADA defense is the use of real-time cyber-physical system (CPS) testbeds. Think of these as full-scale operational laboratories where engineers and security teams can safely simulate and scrutinize complex power system scenarios—including cyberattacks.
Here’s why these testbeds are proving invaluable for power system security and control:
Simulating Realistic Threats: Testbeds allow organizations to create controlled environments that closely mimic actual power grids. This enables teams to launch and observe both traditional and advanced cyber threats—ranging from ransomware to zero-day exploits—without risking disruption to real-world operations.
Testing Controls and Response: Security teams can trial incident response runbooks, validate detection tools, and measure how quickly their defenses can contain and recover from attacks. It’s like running a fire drill for your SCADA system, but with the ability to stress-test controls under true-to-life conditions.
Evaluating System Resilience: By safely tweaking configurations or introducing faults, teams can study how different parts of a power system behave under stress. This hands-on approach provides practical insights for hardening PLCs, HMIs, and network architecture.
Training and Collaboration: Engineers, operators, and cybersecurity pros can all get hands-on experience tackling evolving threats. These exercises not only build muscle memory for incident response but also bridge gaps between IT and OT staff.
From identifying hidden vulnerabilities to refining recovery procedures and fostering team preparedness, real-time cyber-physical system testbeds have become a trusted proving ground. They play a vital role in sharpening defenses before actual adversaries come knocking.
Real-Time Cyber-Physical Testbeds: A Platform for Hands-On Training and Security Prototyping
A critical component in advancing both operator skills and security resilience is the use of real-time cyber-physical systems testbeds. These environments simulate the unique mix of IT and operational technology seen in SCADA environments, allowing organizations to replicate real-world network architectures, protocols, and process controls—without putting production systems at risk.
Real-time testbeds offer several key benefits:
- Operator Training: Testbeds provide a safe, realistic environment where operators and engineers can practice responding to everything from routine incidents to sophisticated cyberattacks. This includes exercises in incident detection, response coordination, and system recovery. By facing plausible scenarios—such as unauthorized configuration changes, protocol anomalies, or ransomware events—staff develop the muscle memory and situational awareness needed to act quickly under pressure.
- Prototyping and Validation: Security teams leverage these platforms to test defensive technologies, such as OT-tailored EDR tools and industrial firewalls, in a controlled setting. This helps uncover gaps in protections, finetune alert thresholds, and validate that monitoring rules accurately flag suspicious behavior without false positives.
- Scenario-Based Drills: By emulating current threat actors’ tactics (using intelligence feeds, for instance), testbeds enable organizations to gauge their readiness against emerging risks. Teams can rehearse response plans, test communication protocols, and pressure-test new policies or technical controls.
- Research and Process Improvements: Finally, testbeds facilitate experimentation—whether evaluating new network segmentation strategies or trying out advanced behavioral detection algorithms powered by machine learning.
Investing in real-time simulation environments ultimately raises the bar for both security posture and staff confidence in handling SCADA incidents.
Using Input Validation Frameworks to Safeguard SCADA Applications
Input validation is a foundational defense when securing SCADA software against injection attacks and other forms of malicious data input. To strengthen your application:
- Emphasize Whitelisting: Rely on “allow lists” that clearly define and permit only expected data types, lengths, formats, and values for every input field. This rigorous approach ensures that any unexpected or suspicious data is blocked at the outset.
- Leverage Established Frameworks: Frameworks such as the OWASP Enterprise Security API (ESAPI) provide robust input validation capabilities, helping ensure your application checks incoming data against well-defined criteria before processing.
- Framework Integration: Consider adopting mature solutions like Struts (with its built-in validators), or similar libraries, to enforce input constraints consistently throughout your SCADA environment.
- Implementation Tactics: Input should always be checked for proper formatting (e.g., number ranges, string lengths, correct dates), and edge-case protections like divide-by-zero or overflows. This level of scrutiny is essential for reducing risk from SQL injection, cross-site scripting (XSS), and command injection attacks.
- Harden Query Handling: When working with databases, always use parameterized queries or stored procedures. These techniques separate query structure from user input, making it much harder for attackers to inject malicious statements.
By weaving these frameworks and approaches into your SCADA development process, you’ll significantly narrow the avenues through which attackers can target your critical infrastructure.
Input Validation: The Front Line Against Injection Attacks
An often-overlooked pillar of SCADA system defense is robust input validation. When attackers search for footholds, input fields—whether via HMIs, engineering workstations, or remote interfaces—are a prime target. Without strong controls, malicious data can slip through, opening the door to dangerous injection attacks like SQL injection, cross-site scripting (XSS), or rogue command execution.
Modern best practice? Use input validation frameworks such as the or open-source tools like Apache Struts. These frameworks enforce a whitelist approach, meaning they only allow predefined, legitimate inputs. Controls should account for:
- Data type checks: Ensuring fields accept only expected formats (e.g., numbers, dates).
- Length and range: Blocking oversized or out-of-range inputs likely to conceal an attack payload.
- Format validation: Confirming inputs match what legitimate users would send—think phone numbers, email addresses, or command syntax.
- Sanitization routines: Actively cleaning or rejecting suspicious characters.
On top of user-facing validation, back-end protections are a must. For any database queries, always rely on parameterized or stored statements so that user input is processed strictly as data—not as executable code.
Combine these measures to eliminate easy avenues for adversaries hoping to inject harmful commands into your SCADA environment. Input validation may not be glamorous, but it’s a critical—and often first—line of defense, especially in systems where even a small lapse could translate into outsized operational impact.
Memory Dump Analysis and Function Codes in SCADA Intrusion Detection
Another valuable forensic technique for SCADA environments involves analyzing memory dumps—both volatile (like DRAM) and non-volatile (such as flash storage). This approach can help unearth sophisticated threats or malware that might otherwise evade traditional detection. In practice, memory content can sometimes be extracted directly using protocol function codes or through hardware-level interfaces such as JTAG, provided the hardware supports it.
- How It Works: Function codes built into SCADA communication protocols may allow authorized users to read and write memory on PLCs. This can be leveraged to capture the current memory state for later analysis—helpful for identifying traces of hidden malware, unauthorized code injections, or other anomalies.
- Practical Challenges: Real-time memory analysis is often constrained by the need for continuous operation and minimal disruption in industrial settings. In many cases, it’s only feasible to perform memory dumps during scheduled downtime or post-incident.
- Device Variability: The ease and completeness of memory extraction vary between device models and vendors. For example, one PLC might offer a removable flash card capturing the whole file system, while another might rely on backup batteries to retain DRAM only during power loss. Not all devices expose the same data, and some may even restrict hardware interfaces like JTAG for security reasons.
- Forensic Value: The data recovered from PLCs—such as variable states, application logic, logs, and metadata—can be crucial evidence in determining the nature and impact of an intrusion. However, inconsistencies in data format, accessibility, and completeness can pose additional forensic hurdles. Moreover, relying solely on vendor-supplied tools poses risks, since these platforms can sometimes have unpatched vulnerabilities themselves.
In short, memory dump analysis, enabled by function codes and supported protocols, is a powerful—but sometimes challenging—tool in the incident investigator’s arsenal for SCADA security. The approach is most applicable to incidents involving local PLCs, and remains a developing field as architectures continue to evolve.
Water Treatment Testbeds: Hands-On Training Grounds for ICS Security
In the world of SCADA and industrial control systems, theory only gets you so far. That’s where water treatment testbeds come into play. These hands-on lab environments are designed to mimic real-world water treatment plants—down to the pumps, valves, sensors, and programmable logic controllers (PLCs) that keep clean water flowing to cities and towns.
So, why are these testbeds valuable? For starters:
- Safe Experimentation: Researchers and engineers can safely simulate both routine operations and cyberattacks without risking critical infrastructure. This makes it possible to test defenses against common threats such as malware, unauthorized commands, or even insider sabotage.
- Training and Skill Development: Testbeds give cybersecurity professionals, operators, and students a arena to practice detecting, responding to, and containing incidents. Whether you’re running mock ransomware attacks or practicing forensic analysis, you’re building muscle memory in a risk-free setting.
- Validation of Security Tools: Vendors and defenders alike use testbeds to fine-tune network monitoring systems, intrusion detection solutions, and protocol analyzers—seeing how tools behave with industrial protocols such as Modbus or DNP3 in real time.
- Scenario-Based Learning: By recreating attack scenarios from industry case studies (think Stuxnet or Triton), teams learn how adversaries exploit vulnerabilities and how layered defenses, like those discussed earlier, can be used to thwart or contain such threats.
In short, water treatment testbeds transform academic concepts into practical, actionable skills. They’re carving out a pivotal role in preparing the next generation of ICS defenders—making cyber resilience more than just a checklist item.
The Value of Shared ICS Security Operations Centers
Shared ICS (Industrial Control Systems) Security Operations Centers (SOCs) provide a centralized approach to monitoring and defending SCADA environments across multiple facilities or organizations. By pooling cybersecurity expertise and resources, these centers deliver several important functionalities and advantages:
- Centralized Threat Detection and Response: Shared SOCs aggregate and analyze security data from various sites, enabling a broad view of threats targeting different operations. This collective intelligence helps to identify attack patterns early, even across geographically dispersed locations.
- 24/7 Surveillance: With a dedicated team monitoring networks round the clock, organizations benefit from constant vigilance—reducing detection and response times for incidents that might otherwise go unnoticed in individual environments.
- Standardized Procedures: Shared operations centers establish and enforce consistent response protocols and best practices. This uniformity ensures that all participants maintain a strong security posture and respond to incidents with coordinated efficiency.
- Cost Efficiency: Pooling resources across companies or business units allows organizations to deploy advanced monitoring and analytics technologies—like SIEM (Security Information and Event Management) and behavioral analysis tools—without each entity bearing the full financial burden.
- Knowledge Sharing: Shared SOC analysts develop specialized expertise by observing a diverse range of attacks and anomalies. This collective learning, along with real-time threat intelligence exchange, accelerates detection and improves defensive measures for everyone involved.
By deploying a shared ICS SOC model, organizations can bridge skill gaps, optimize investments, and raise the overall bar for SCADA security—making these collaborative centers an increasingly attractive strategy for industrial cyber defense.
Output Encoding: Safeguarding Against XSS in SCADA Systems
Output encoding is a fundamental defensive measure, especially in environments where human-machine interfaces (HMIs) or web-based dashboards interact with users. By encoding user input before displaying it in browsers—converting special characters so they can’t be misinterpreted as executable code—you significantly reduce the risk of cross-site scripting (XSS) attacks.
Here’s how output encoding strengthens your SCADA security posture:
- HTML and JavaScript Encoding: By encoding dynamic data presented on web HMIs or administrative consoles, malicious scripts injected by attackers simply appear as harmless text, neutralizing their threat.
- URL Encoding: When user input is appended to URLs—such as in remote diagnostics or configuration portals—encoding ensures control characters can’t be exploited to inject malicious commands or scripts.
- CSS Encoding: For interfaces with dynamic styling or configuration, encoding prevents style-based exploits that could impact the display or behavior of industrial screens.
Proper output encoding should be tailored to the context: HTML for web content, JavaScript for scripts, and so on. Tools like Microsoft’s AntiXSS library or OWASP’s ESAPI can help automate this process, taking the guesswork out for your development team.
By enforcing output encoding across all SCADA web interfaces and remote access points, organizations make it substantially harder for attackers to exploit vulnerabilities or trick operators with rogue scripts—helping keep the physical process out of harm’s way.
Evaluating Machine Learning Models on the UNSW-NB15 Dataset
To get a sense of how different machine learning models stack up when detecting attacks in SCADA networks, we put the UNSW-NB15 dataset to the test. We compared four popular algorithms—Logistic Regression (LR), K-Nearest Neighbors (KNN), Random Forest, and Support Vector Machine (SVM)—to see which offers the best bang for your buck in terms of accuracy and reliability.
Here’s how the contenders performed:
- Logistic Regression: Delivered modest results, with accuracy, precision, and recall in the low 70% range. While LR is simple and interpretable, its ability to catch the subtleties in complex attack patterns was limited on this dataset.
- K-Nearest Neighbors (KNN): Raised the bar with an accuracy around 84%, showing good balance between recall and precision. KNN proved more capable of recognizing attack behaviors, making it a stronger fit for environments where attack patterns aren’t always straightforward.
- Random Forest: Emerged as the top performer, hitting approximately 86% accuracy and maintaining equally high recall and precision. Its ensemble approach makes it especially well-suited for complex, noisy datasets like those found in operational networks.
- Support Vector Machine (SVM): Not far behind Random Forest, SVM posted an 85% accuracy, excelling in recall. SVM’s knack for handling high-dimensional data helped it spot attacks nearly as well as Random Forest, though with slightly less balanced precision.
In short, Random Forest and SVM led the pack for threat detection on the UNSW-NB15 dataset, with KNN as a strong contender. Logistic Regression, while useful as a baseline, lagged behind in this scenario. Choosing the right model should account for your environment’s unique data, performance demands, and resource constraints.
The Human Element and Proactive Defense
Technology alone isn’t enough. Skilled cybersecurity professionals with knowledge of both IT and OT environments are crucial. Regular training for operators, engineers, and security staff on SCADA cybersecurity best practices and threat awareness can significantly bolster defenses.
Harnessing Cyber Ranges and Testbeds for ICS & SCADA Security
To truly prepare for modern threats, organizations are increasingly turning to cyber ranges and testbeds tailored for ICS and SCADA environments. Think of these as highly controlled, risk-free playgrounds—miniature versions of your actual operational systems—designed specifically for learning, experimentation, and validation.
Here’s why they matter:
- Safe, Realistic Training Grounds: Cyber ranges allow security teams, engineers, and operators to simulate real-world cyberattacks without the risk of causing actual harm to critical infrastructure. This hands-on training is invaluable for building both confidence and technical skillsets.
- Testing the Unthinkable: Testbeds enable organizations to safely experiment with new security controls, software patches, and network architectures. They let you see the impact of tweaks or updates before rolling them out to live environments—a bit like a “wind tunnel” for your SCADA network.
- Incident Response Drills: By mimicking attack scenarios—ransomware, insider threats, supply chain compromises—teams can practice and fine-tune their incident response plans so that when (not if) an event happens, everyone knows their role.
- Research and Development: Academia, cybersecurity vendors, and industrial organizations use these environments to study emerging attack methods and develop next-generation defenses. This collaborative, research-driven approach helps stay ahead of adversaries.
In short, cyber ranges and testbeds have become essential tools for bridging the gap between theoretical knowledge and real-world application, ensuring that both people and processes can withstand the ever-evolving cyber risks facing critical infrastructure.
A proactive, defense-in-depth strategy is paramount. This involves not just detecting attacks but actively hunting for threats, continuously assessing and improving security posture, and fostering a culture of security awareness throughout the organization.
Interoperability and Extensibility: Overcoming SCADA’s Legacy Limitations
Modernizing SCADA systems comes with an enduring set of challenges—chief among them is the need for seamless interoperability between diverse devices and future-proof extensibility. Legacy SCADA platforms were often proprietary and closed, making integration with new sensors, PLCs, remote sites, or third-party tools anything but straightforward.
To address these roadblocks, organizations should adopt the following approaches:
- Standardized Protocols and Open Architectures: Transitioning to open communication standards like OPC UA or MQTT dramatically improves cross-vendor compatibility. This paves the way for securely connecting devices from different manufacturers and integrating next-gen technologies with fewer headaches.
- Modular System Design: By structuring SCADA solutions in a modular fashion—with well-defined APIs and decoupled functional components—upgrades and feature enhancements become far less disruptive. Need to add new analytics or connect an IIoT device? Modular architecture keeps the door open.
- Robust Middleware and Gateways: Implementing flexible middleware layers or protocol gateways can help bridge the gap between old legacy gear and modern interfaces, acting as a translator so older assets don’t get left behind.
- Vendor-Neutral Solutions: Whenever possible, opt for platforms and infrastructure that avoid vendor lock-in. This fosters competition, simplifies procurement, and helps ensure a wider support ecosystem as your needs grow.
The bottom line: achieving robust interoperability and building extensibility into your SCADA environment demands foresight, strategic investment in open technologies, and the willingness to reassess legacy equipment. This foundation allows organizations to adapt nimbly as operational requirements—and cyber threats—invariably evolve.
Securing the Future of Critical Infrastructure
SCADA cyber monitoring is a complex but non-negotiable aspect of modern industrial operations. As threats evolve in sophistication and frequency, organizations must invest in the right tools, implement effective techniques, and empower their people with the knowledge to defend these critical systems. By doing so, we can help ensure the continued reliability and safety of the essential services we all depend on.
Yet, as the landscape of SCADA security matures, several persistent challenges and open issues demand attention:
Emerging Challenges in SCADA Security
Evolving Architectures and Cloud Integration: The move from traditional, centralized SCADA systems to IoT- and cloud-based architectures promises scalability and flexibility. However, this shift introduces new attack vectors—from increased exposure to man-in-the-middle attacks to the risk of information leakage and privacy concerns. Decision-makers must weigh the operational benefits of cloud migration against the potential security implications, ensuring that privacy, scalability, and fault tolerance remain front and center.
Limitations of Current Datasets: While the NVD and CVE databases are invaluable for vulnerability management, they lack SCADA-specific depth. Commonly used datasets like KDD99 and NSL-KDD, though popular for intrusion detection research, often contain redundant records or are outdated, limiting their effectiveness for real-world SCADA environments. There’s an urgent need for up-to-date, comprehensive datasets that reflect the diversity and complexity of SCADA deployments.
Intrusion Prevention and Prediction Gaps: Much of the research and tooling has focused on intrusion detection, with less progress made on effective prevention and prediction. While machine learning algorithms—such as random forest, SVM, and Naive Bayes—have shown promise in predicting certain attack types, their practical application remains limited. The next frontier involves developing robust, predictive intrusion prevention systems that can adapt to the rapidly changing threat landscape.
Distributed Monitoring at Scale: As SCADA systems grow in size and complexity, centralized monitoring solutions are increasingly insufficient. Distributed intrusion detection systems (DIDS) offer the potential to aggregate and correlate data across vast networks, improving detection of distributed exploits and stealthy malware. However, optimizing these systems with multiple, coordinated learning models is still an ongoing research challenge.
Testing, Validation, and Scalability: High-fidelity testbeds are crucial for validating SCADA security measures, but developing realistic, scalable environments—covering sectors like water, energy, and transportation—remains cost-prohibitive and technically challenging. Researchers and practitioners alike must prioritize investment in scalable, simulated environments to enable meaningful testing.
Forensic Readiness and Incident Response: Unlike IT environments, SCADA systems must operate continuously, complicating live forensic investigations. Most traditional forensic tools fall short in OT settings, making it essential for vendors to incorporate forensic capabilities directly into their products. Automation, data science, and big data analytics can help address these gaps, improving evidence collection and supporting faster, more informed incident response.
The Road Ahead—Security in an IoT-SCADA World: The integration of IoT devices with SCADA introduces new operational and security considerations. Increased bandwidth demands and potential latency can affect not only system performance but also security response times. Ensuring high throughput and minimal delay is critical—not just for productivity, but for effective defense against time-sensitive threats.
By staying vigilant and proactive in addressing these evolving challenges—and by fostering a culture of continuous improvement—organizations can keep pace with both technological advancements and the threat actors seeking to exploit them.