Understanding the Importance of Offensive Assessments in Industrial Control Systems (ICS)
Industrial Control Systems (ICS) face increasing cybersecurity challenges due to rising connectivity and evolving threats. For IT managers and cybersecurity professionals, securing these systems is critical to protecting critical infrastructure.
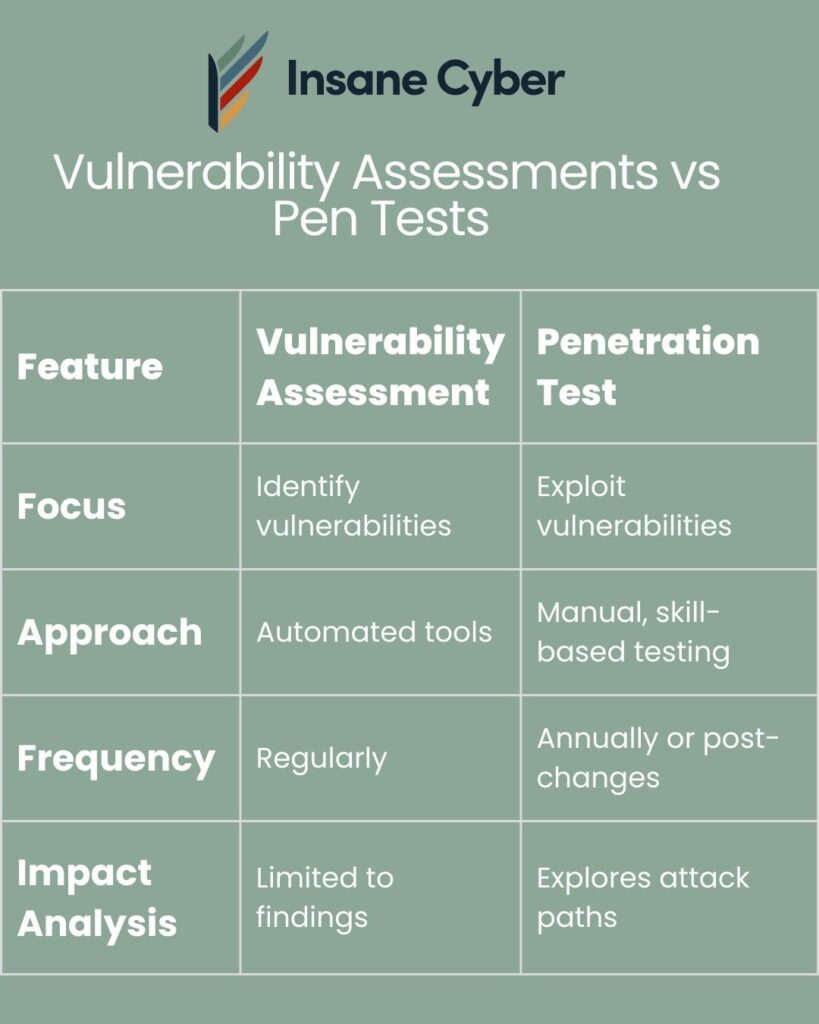
One key component of ICS security is offensive assessments, which identify vulnerabilities and assess potential impacts. These assessments fall into two primary categories: Vulnerability Assessments and Penetration Tests. In this guide, we will explore their differences, applications, and best practices for conducting them safely in ICS environments.
Introduction to Operational Technology (OT) Security
OT vs. IT: Key Differences
While Operational Technology (OT) and Information Technology (IT) serve distinct roles, they are increasingly converging. Understanding their differences is essential:
-
OT: Controls physical devices, processes, and infrastructure in industries like manufacturing, energy, and transportation. Focuses on reliability, safety, and efficiency.
-
IT: Manages digital systems that process, store, and secure data for business functions. Prioritizes data integrity and cybersecurity.
With IT/OT convergence, cybersecurity teams must adapt strategies to manage hybrid environments effectively.
The Need for Offensive Assessments in OT Environments
Traditional security measures, such as firewalls and antivirus software, are insufficient to protect OT systems from targeted attacks. As technology advances and interconnectivity increases, so does the attack surface.
Key concerns in OT security:
-
Prioritization of availability: OT environments often prioritize uptime over data security, making them attractive attack targets.
-
Aging infrastructure: Many ICS systems were not designed with cybersecurity in mind.
-
Growing attack surface: The integration of IoT and remote access increases exposure to cyber threats.
To address these risks, organizations must conduct offensive security assessments that simulate real-world attack scenarios.
Types of Offensive Assessments in ICS Environments
Key Assessment Types:
-
Red Team Assessments – Focus on evasion and threat emulation to test an organization’s detection and response capabilities.
-
Penetration Tests – Simulate real-world cyberattacks in collaboration with internal teams to identify exploitable vulnerabilities.
-
Device Penetration Tests – Evaluate security risks in specific ICS hardware and vendor applications.
-
Vulnerability Assessments – Identify potential weaknesses using automated tools without actively exploiting them.
Insights from the SANS State of OT/ICS Cybersecurity Survey:
-
75% of organizations conduct annual OT security assessments.
-
51% of organizations rely on paper-based vulnerability assessments.
-
40% have participated in active vulnerability assessments.
-
25% have conducted penetration tests.
Despite increasing adoption, there is a growing need for more active assessments that validate vulnerabilities and measure their potential impact. However, such assessments should only be conducted where safe within OT networks.
Understanding Vulnerability Assessments
A Vulnerability Assessment is a structured approach to identifying security weaknesses within a network or system. In ICS environments, this involves evaluating control systems and associated assets.
Key Characteristics:
-
Broad Scope – Examines domain, host, and network configurations.
-
Automated Tools – Uses scanning tools to detect known vulnerabilities.
-
Identification & Prioritization – Focuses on classifying vulnerabilities by severity.
-
Ongoing Process – Regular assessments ensure continued security as threats evolve.
While vulnerability assessments provide valuable insights, they do not actively exploit weaknesses, leading to the need for penetration testing.
The Role of Penetration Testing in ICS Security
Penetration Testing (Pentesting) goes beyond identifying vulnerabilities by attempting to exploit them, revealing their real-world impact.
Key Characteristics:
-
Focused Attack Simulation – Tests security controls against real attack scenarios.
-
Manual & Automated Methods – Uses a combination of techniques to assess weaknesses.
-
Exploitation – Demonstrates how vulnerabilities could be leveraged by attackers.
-
Detailed Reporting & Remediation Guidance – Provides actionable insights for mitigating risks.
Vulnerability Assessment vs. Penetration Test: Choosing the Right Approach
When to Use Each:
-
Vulnerability Assessments – Best for routine security checks and maintaining awareness of potential risks. They are non-intrusive and can be scheduled frequently.
-
Penetration Tests – Should be conducted periodically or after major system changes to evaluate security posture under real-world attack conditions.
Challenges & Considerations in ICS Assessments:
-
System Sensitivity – Many OT systems are fragile, requiring caution to avoid operational disruptions.
-
Specialized Expertise – ICS assessments demand professionals with knowledge of both cybersecurity and industrial control systems.
Preparing for Offensive Assessments in ICS
Successful security assessments require proper preparation:
Key Preparation Steps:
-
Set Clear Goals & Objectives – Define the scope and focus of the assessment to ensure meaningful results.
-
Comprehensive Documentation – Provide network diagrams, firewall rules, and asset inventories.
-
Access & Permissions – Ensure authorized testers have necessary access to conduct assessments.
-
Rules of Engagement – Establish boundaries to ensure safe and effective testing.
-
Involvement of Subject Matter Experts (SMEs) – Leverage expertise for accurate risk evaluation.
Challenges of Offensive Assessments in OT Environments
ICS assessments present unique challenges:
-
Safety Concerns – Legacy OT systems can be sensitive to active testing.
-
Complexity – Industrial networks require tailored testing approaches.
-
Regulatory Compliance – Standards like NERC CIP impose strict security assessment requirements.
Conclusion
Both vulnerability assessments and penetration tests play essential roles in securing Industrial Control Systems. By strategically integrating both approaches, organizations can strengthen their cybersecurity posture, safeguard critical infrastructure, and mitigate evolving threats.
Cybersecurity professionals and IT managers must carefully evaluate the benefits and limitations of each method to ensure effective risk management. A proactive security strategy, incorporating regular assessments and real-world attack simulations, will help maintain the resilience and reliability of ICS environments.
For more insights on ICS security strategies, stay tuned to our blog or connect with us on our professional network.