Bring together host and network data to uncover hidden risks and blind spots.
You need:
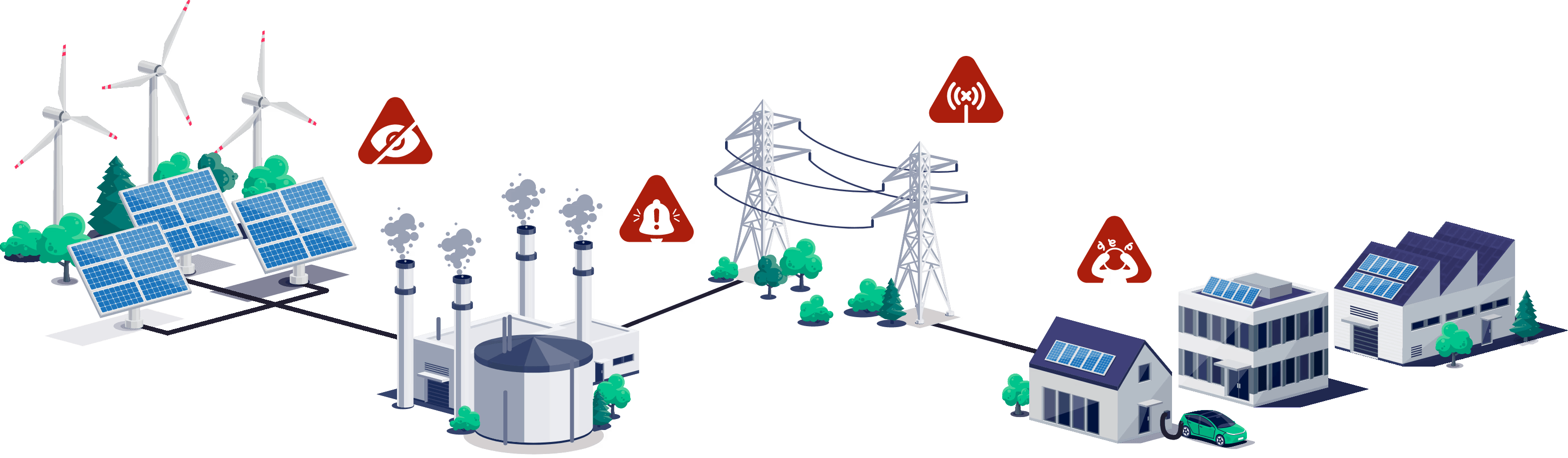
Seeing your entire environment feels impossible with cost-prohibitive monitoring solutions and hard to reach places.
No one will understand your environment's challenges quite like you, and professional services firms treat every engagement the same.
Teams often don't have the resources or expertise to respond quickly or effectively to OT incidents, meaning longer downtime and costly retainers.
Near real-time host and data monitoring built for OT environments.
Valkyrie software in durable, ready-to-go flyaway kit.
Our team of experts plus Valkyrie to keep your network protected.
OT cybersecurity help,
when and how you need it.




Our products are designed to work with
you and keep your network protected.