Modern industrial environments are a paradox: cutting-edge digital initiatives running side-by-side with decades-old control systems. While Industry 4.0 marches ahead with smart sensors and cloud-connected analytics, the systems at the heart of most OT networks are anything but modern. Legacy infrastructure isn’t a corner-case problem—it’s the baseline reality for manufacturers, energy providers, transportation networks, and critical infrastructure operators.
This blog breaks down how security professionals can protect the aging core of our industrial systems—not by chasing perfection, but by embracing pragmatic, non-disruptive strategies grounded in reality.
The Legacy Reality: Built to Last, Not to Defend
![]() Legacy OT systems weren’t designed for the cybersecurity battles of today. Many were engineered 20+ years ago for reliability and stability—long before the first targeted OT malware even existed.
Legacy OT systems weren’t designed for the cybersecurity battles of today. Many were engineered 20+ years ago for reliability and stability—long before the first targeted OT malware even existed.
From SCADA systems and Distributed Control Systems (DCS) to programmable logic controllers (PLCs) running Windows XP, these assets continue to drive the world’s infrastructure. Why? Because they work. And because taking them offline for upgrades is often cost-prohibitive, operationally risky, or flat-out impossible.
A 2025 survey of OT leaders across Europe tells the story: half said at least 50% of their environment still relies on legacy systems. One in five said over 75% of their infrastructure is legacy-dependent.
This isn’t a problem of poor decision-making—it’s a consequence of real-world constraints.
Why the Old Stays On
1. Downtime Is Unacceptable
In OT, uptime is sacred. Even planned outages can cost millions per hour and risk cascading failures. The potential consequences—disrupted production, lost revenue, compromised safety—eclipse the hypothetical risk of a cyberattack in many decision-makers’ minds.
2. Modernization Costs Are Massive
A full upgrade of legacy hardware and software isn’t just expensive—it’s overwhelming. Organizations hesitate to rip and replace critical systems when existing ones still “work.” Plus, many legacy devices are proprietary and deeply integrated. Replacing them can trigger unexpected incompatibilities across production lines.
3. Support Is Scarce
Vendors for legacy platforms may be long gone, and the engineers who originally installed these systems are retiring. Knowledge gaps are growing wider, and replacement parts are increasingly rare. These conditions make modernization even riskier.
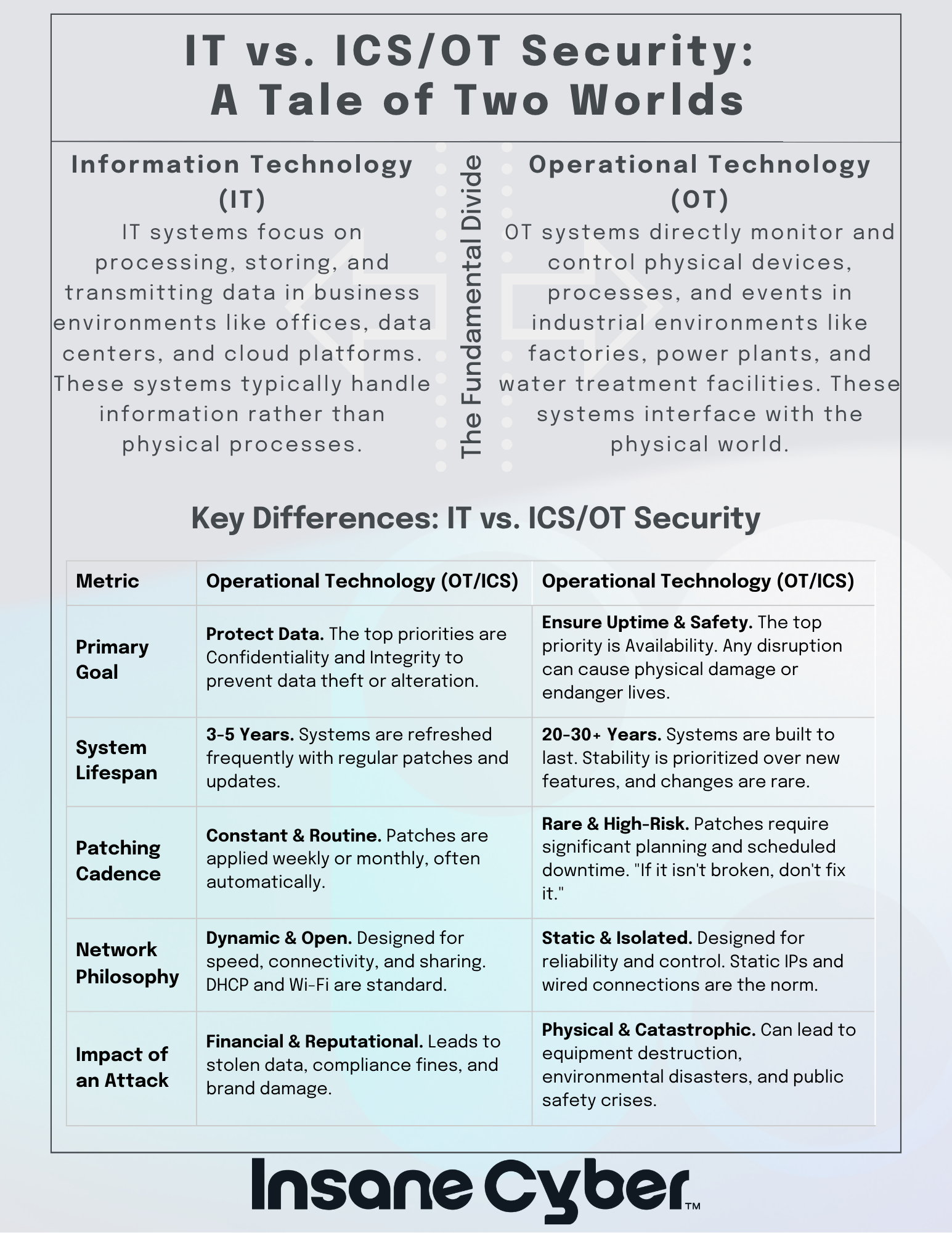
IT vs. OT: Why Security Strategies Don’t Translate
If you’ve ever tried to apply IT security practices to OT, you already know: it doesn’t work.
IT and OT operate under different imperatives. In IT, we protect data. In OT, we protect people, processes, and uptime. A patch that causes a Windows server to reboot may be an inconvenience in IT. In OT, that same reboot could halt a refinery, damage expensive equipment, or endanger human lives.
This difference is more than technical—it’s cultural.
| Characteristic | IT Security | OT Security |
|---|---|---|
| Priority | Confidentiality, Integrity, Availability | Safety, Availability, Integrity |
| Lifecycle | 3-5 years | 15-30+ years |
| Downtime tolerance | High | Extremely low |
| Threat model | Data loss, espionage, financial theft | Physical harm, production loss, safety failures |
As more OT systems get connected to IT networks and the internet, the attack surface has grown exponentially—but the cultural gap and strategic misalignment persist.
Why Legacy Systems Are So Vulnerable
Legacy systems aren’t just old—they’re fundamentally exposed:
No Patch Support: Many run on end-of-life operating systems like Windows XP or NT that no longer receive security updates.
Insecure-by-Design: Legacy devices often lack authentication, encryption, or audit logging.
Hardcoded Credentials: Some firmware contains default usernames and passwords that can’t be changed.
Fragile Communication Protocols: Modbus and DNP3, the workhorses of industrial networking, were built for reliability—not security. They lack encryption, authentication, and integrity checks.
Example: How Modbus Can Be Exploited
An attacker who gains network access can:
Intercept commands (because Modbus sends data in plaintext)
Modify setpoints (e.g., change a temperature value from 100°F to 1000°F)
Send unauthorized commands (e.g., stop a motor or open a valve)
That’s not theoretical—it’s happening now. Tools like Incontroller and malware like Triton have shown how these weaknesses can be operationalized at scale.
Modern Threats, Old Targets
Legacy OT is a magnet for both opportunistic attackers and nation-state adversaries.
Ransomware groups increasingly target industrial companies, not just IT systems.
State-sponsored actors like VOLTZITE (Volt Typhoon) and ELECTRUM (Sandworm) actively conduct reconnaissance and embed themselves into critical infrastructure for potential future disruption.
Malware toolkits like Pipedream can attack a broad range of PLCs across vendors—scalable, modular, and built for industrial sabotage.
It’s not about “if” a threat actor finds your legacy systems—it’s about “when.”
So… You Can’t Patch. What Now?
For many OT teams, patching isn’t an option. But you don’t need to patch to protect.
Here’s what you can do instead—starting with the network.
1. Network Segmentation: Contain the Blast Radius
The most effective non-disruptive control is also the most overlooked: network segmentation. It divides your OT network into zones and isolates critical systems so that a compromise in one area doesn’t spread to the rest.
Start with the Purdue Model as a guide:
IT/OT Separation: Establish a DMZ between the corporate network and control systems.
Macro-segmentation: Separate zones by function (e.g., SCADA vs. safety systems).
Micro-segmentation: Use firewalls or software-defined networks to isolate individual devices.
The result? If an attacker gets in, they hit a wall—again and again.
2. Passive Monitoring: See Without Touching
Legacy systems can’t handle active scanning or vulnerability assessments. But you still need visibility.
Passive network monitoring gives you insight without risk. Using switch SPAN ports or network TAPs, you can mirror traffic and analyze it with OT-aware tools.
OT Intrusion Detection Systems decode industrial protocols and flag malicious commands.
SIEMs correlate alerts across the environment.
AI/ML Anomaly Detection builds baselines of normal behavior and spots deviations—without needing signatures.
This lets you detect threats without disrupting operations.
3. Virtual Patching: Block Exploits at the Network Edge
If you can’t patch the system, patch the path.
Virtual patching uses firewalls or IPS devices to inspect and block malicious traffic aimed at a known vulnerability. The attack never reaches the asset.
Works immediately, with no downtime
Doesn’t touch the asset or risk breaking it
Buys time (or serves as a permanent solution)
Think of it as a bouncer for your unpatchable systems.
4. Application Whitelisting: Stop Unknowns Cold
Legacy HMIs and engineering workstations are perfect for application whitelisting. These are static, single-purpose systems that don’t need frequent software changes.
Only known-good applications can run
All other executables are blocked
Even if malware gets in, it can’t execute
This “default deny” approach is ideal for stopping ransomware and rogue code, and it doesn’t rely on signatures or frequent updates.
5. Harden the Weak Spots
Simple changes can dramatically reduce your attack surface:
Disable unused ports and services on endpoints
Replace default passwords, or at least disable accounts that use them
Restrict remote access to jump hosts with MFA
Control USB usage with policies and scanning kiosks
These controls don’t require patching or downtime—but they make it much harder for attackers to gain a foothold.
6. Have a Recovery Plan That Actually Works
Assume breach. What happens next?
A robust backup and recovery plan tailored for OT is your last line of defense.
Back up control logic, HMI configurations, historian data—not just files
Use the 3-2-1 rule: 3 copies, 2 formats, 1 air-gapped
Test your recovery process regularly
Back up in a way that doesn’t require taking the system offline
Backups aren’t glamorous, but when ransomware hits or malware wipes a system, you’ll be glad they’re there.
Frameworks That Guide, Not Hinder
Structure your program around frameworks designed for OT:
ISA/IEC 62443: Defines zones, conduits, and security levels specific to industrial environments.
NIST CSF + SP 800-82: A broad but flexible framework that helps map risk-based controls to OT assets.
Use these to build a unified governance model that fits both the CISO’s expectations and the plant floor’s constraints.
Bridging Old and New: IIoT Gateways
Need to pull data from legacy systems without exposing them to the open internet?
IIoT gateways provide a secure middle layer:
Speak both legacy (Modbus, serial) and modern (MQTT, OPC UA)
Translate insecure protocols into encrypted, authenticated traffic
Enforce access control and monitor communications
They let you extract insights without opening floodgates to cyber threats.
Modernization, Without the Rip-and-Replace
Eventually, legacy systems must go. But not all at once.
The Strangler Fig Pattern offers a path: build modern components around legacy systems, gradually replacing functions over time.
Start with edge devices or analytics layers
Move into partial upgrades (e.g., HMI refresh or network stack)
Decommission legacy components when they’re no longer mission-critical
This incremental approach avoids downtime and spreads cost over time.
Conclusion: Real Security for Real Constraints
You’re not working in a lab—you’re in the trenches. Your legacy systems aren’t going anywhere anytime soon. The goal isn’t perfection; it’s resilience.
By applying the principles in this guide—network segmentation, passive visibility, compensating controls, and strategic modernization—you can defend your infrastructure without breaking it.
It’s time to stop seeing legacy systems as a dead-end and start treating them as what they are: high-value assets in need of thoughtful protection.
Security isn’t about replacing the past. It’s about securing it—so you can build the future on solid ground.
Need help securing your legacy OT systems?
Contact our team to learn how to implement non-disruptive, high-impact security strategies tailored for your industrial environment.





