From the clean water in your tap to the electricity powering your screen, critical infrastructure relies on a hidden network of technology. But what happens when that network, the very backbone of our physical world, is attacked?
Recent events, like the Colonial Pipeline incident, have starkly reminded us that cyber threats extend far beyond data breaches and financial fraud. They now directly impact our daily lives, posing risks to safety, availability, and the fundamental operations that underpin society.
This unseen network is known as Operational Technology (OT) – the hardware and software that directly monitors and controls physical devices, processes, and events in an enterprise.
As the digital and physical worlds converge, protecting these systems has become a paramount concern. This post will define OT security, explain its critical differences from traditional IT security, and reveal why relying solely on your existing IT defenses leaves your most vital operations dangerously exposed.

What is Operational Technology (OT) Security?
OT security is the practice of protecting industrial control systems (ICS) and the broader operational technology environment from cyber threats.
While IT security focuses on safeguarding information and data, the primary goal of OT security is ensuring the availability, reliability, and safety of physical processes. This distinction is crucial: a breach in IT might mean data loss, but a breach in OT could mean a power outage, an environmental disaster, or even loss of life.
Key components of the OT environment include:
- Industrial Control Systems (ICS): The overarching category for systems controlling industrial processes.
- Supervisory Control and Data Acquisition (SCADA) systems: Used to control and monitor geographically dispersed industrial processes.
- Distributed Control Systems (DCS): Typically used for process control within a localized production area.
- Programmable Logic Controllers (PLCs): Ruggedized industrial computers that automate specific processes, like controlling a robotic arm or a conveyor belt.
- Human-Machine Interfaces (HMIs): Graphic displays that allow operators to interact with and monitor industrial processes.
Examples of OT Security in Action
To truly grasp OT security, it helps to visualize it in real-world scenarios. Here are a few examples:
Industry | Scenario | OT Security Measures |
Manufacturing Plant | Protecting an automated assembly line that builds cars. | Network Segmentation: Isolating the factory floor’s network from the corporate IT network. Access Control: Restricting who can modify PLC programming that controls robotic arms. Anomaly Detection: Continuous monitoring for unusual commands that could halt production or cause a safety incident. |
Electrical Grid | Ensuring the uninterrupted flow of electricity. | SCADA System Hardening: Securing the control systems managing the grid. RTU Protection: Safeguarding Remote Terminal Units from unauthorized access. Protocol-Aware IDS: Implementing intrusion detection systems designed to understand industrial protocols (like Modbus or DNP3) and identify malicious commands. |
Water Treatment Facility | Guaranteeing water purification processes aren’t tampered with. | HMI Security: Hardening Human-Machine Interfaces to prevent an attacker from changing chemical dosing levels. Secure Remote Access: Establishing stringent policies for third-party maintenance. Fail-Safes: Ensuring physical and digital fail-safes are in place if control systems are compromised. |
IT Security vs. OT Security: A Tale of Two Worlds
The most common misconception in cybersecurity is that IT security practices can simply be extended to OT environments. This couldn’t be further from the truth. While both aim to protect digital assets, their fundamental priorities, technologies, and operational contexts are vastly different.
Here’s a comparison:
Feature | IT Security (Information Technology) | OT Security (Operational Technology) |
Primary Goal | Confidentiality, Integrity, Availability (CIA) of data | Availability, Integrity, and Confidentiality of industrial processes |
Key Assets | Data, servers, applications, cloud infrastructure | Physical equipment, industrial processes, human lives, environmental impact |
System Lifespan | 3-5 years (frequent upgrades) | 15-25+ years (legacy systems are common, “if it ain’t broke…”) |
Operating Systems | Modern (Windows Server, Linux) with regular updates | Often proprietary or legacy OS (e.g., Windows XP, embedded systems) |
Patching Cadence | Frequent (daily/weekly/monthly) | Infrequent; requires scheduled downtime, testing, or complex change management |
Network Protocols | TCP/IP, HTTP/S, SMTP, standard IT protocols | Industrial protocols (Modbus, Profinet, DNP3, OPC UA) |
Impact of Failure | Data breach, financial loss, reputational damage, service disruption | Production shutdown, environmental disaster, injury, loss of life, significant economic impact |
Is OT Security Just a Different Kind of Network Security?
Network security is a fundamental component of both IT and OT security, but its application and considerations are profoundly different.
In IT, network security focuses on securing data in transit across corporate networks. This involves firewalls, VPNs, and intrusion detection systems (IDS) that understand common internet protocols and look for malware signatures or unauthorized access attempts.
OT network security, however, demands a specialized approach:
- Protocol Awareness: Standard network security tools don’t “speak” the language of industrial protocols. An OT security solution must understand Modbus, Profinet, DNP3, etc., to detect malicious commands that could manipulate a physical process, not just malicious files.
- The “Air Gap” Myth: While many believe OT networks are completely isolated (“air-gapped”), this is rarely the case today. For efficiency, remote monitoring, and data analysis (Industry 4.0, IIoT), OT networks are increasingly connected to IT networks, creating new attack vectors that traditional network security might miss.
- The Purdue Model: This widely accepted framework helps segment industrial networks into logical zones, creating layers of defense between the corporate IT world and the sensitive control systems on the plant floor. It’s about containing threats, not just blocking them at the perimeter.
- Focus on Behavior: OT network monitoring is less about signature-based detection (which is difficult for proprietary systems) and more about detecting abnormal behavior. For example, “Why is this PLC suddenly receiving a command from an unauthorized HMI?” or “Why is this valve opening beyond its normal operating parameters?”
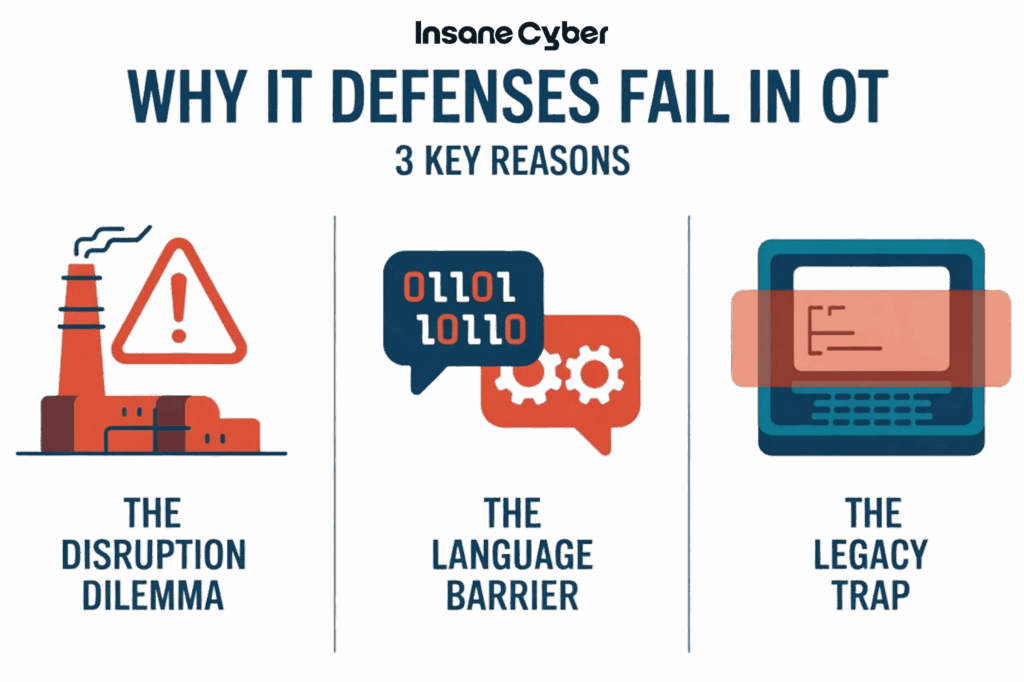
Top 3 Reasons IT Security Tools Fail in OT Environments
Given these fundamental differences, it becomes clear why traditional IT security tools are largely ineffective, and often detrimental, in OT environments.
- The Disruption Dilemma
Traditional IT security often involves active scanning, aggressive patching, and frequent reboots – practices that can crash fragile, legacy OT systems. Imagine trying to run a vulnerability scan on a system controlling a chemical process; it could cause an immediate, catastrophic shutdown or even trigger unsafe conditions. You can’t simply “reboot a power plant” or halt a manufacturing line without immense cost and risk.
- The Language Barrier
As mentioned, standard firewalls, antivirus software, and intrusion detection/prevention systems (IDS/IPS) don’t understand industrial communication protocols. They might see a malicious command to open a floodgate as legitimate network traffic because they lack the context of the operational process. This makes it easy for sophisticated attacks to slip past traditional defenses, directly manipulating physical systems.
- The Legacy Trap
OT environments are characterized by devices built to last for decades. This means many critical systems run on unpatched, outdated operating systems (e.g., Windows XP, unsupported Linux kernels) that are inherently vulnerable. Replacing or upgrading these systems is often prohibitively expensive, complex, or impossible without shutting down operations for extended periods. Traditional IT security assumes modern, patchable systems; OT rarely offers this luxury.
Conclusion: Building the Bridge Between IT and OT
OT security is not merely an extension of IT security; it is a specialized discipline with unique priorities, technologies, and risks. While IT focuses on data confidentiality, OT is centered on the physical safety, continuous availability, and operational reliability of the systems that run our critical infrastructure.
As industries embrace digital transformation, the convergence of IT and OT networks will only increase. This makes understanding and implementing dedicated OT security strategies more crucial than ever. Relying on traditional IT defenses to protect these delicate, high-stakes environments is a recipe for disaster. Organizations must bridge the gap between IT and OT, fostering collaboration and investing in specialized solutions and expertise to safeguard the physical world against an ever-evolving cyber threat landscape.
Want to assess your organization’s OT security readiness? Schedule a 15-minute consultation with one of our industrial cybersecurity experts to secure your critical operations.





