Hacking for Good: A Practical Guide to Offensive Security in ICS Environments
Industrial Control Systems (ICS) are the backbone of our modern world, running everything from power grids and manufacturing plants to water treatment facilities. But as these systems become more connected, they also become bigger targets for cyberattacks. For any IT manager or cybersecurity pro working with this critical infrastructure, understanding how to proactively find and fix vulnerabilities is no longer optional—it’s essential.
That’s where offensive security comes in. By simulating real-world attacks through vulnerability assessments and penetration tests, you can uncover weaknesses before an adversary does. This guide will break down how to conduct these assessments safely and effectively in sensitive Industrial Control System (ICS) and Operational Technology (OT) environments.
IT vs. OT: Why Industrial Cybersecurity Is Different
While Information Technology (IT) and Operational Technology (OT) are increasingly intertwined, they operate on different principles. Understanding these differences is the first step to securing them.
- IT (Information Technology): This is the world of data. IT systems process, store, and secure information for business functions. The top priorities are confidentiality and data integrity.
- OT (Operational Technology): This is the world of physical processes. OT controls the machinery and infrastructure in industries like energy and manufacturing. Here, the non-negotiable priorities are reliability, uptime, and safety.
The unique challenge in OT is that the technology is directly tied to physical equipment. Think of sprawling power grids or automated assembly lines. These environments are often a complex mix of custom-built systems, legacy hardware, and specialized protocols. A generic vulnerability scan won’t cut it. Effective security assessments in OT are about understanding the physical process and implementing protections that keep operations running safely.
The Growing Need for Offensive Security in OT
Traditional security tools like firewalls and antivirus software are no longer enough. The “attack surface” for OT systems is expanding due to the rise of IoT devices and remote access. Key concerns include:
- Uptime Over Security: OT environments are built for continuous operation, which can sometimes lead to security being a lower priority.
- Aging Systems: Many industrial systems were designed decades ago without modern cybersecurity in mind.
- IT/OT Convergence: As IT and OT systems connect, OT environments are exposed to new threats they weren’t designed to handle.
Offensive assessments help bridge these gaps by simulating how a real attacker might think and act, allowing you to find and fix vulnerabilities before they can be exploited.
What Kind of Assessment Do You Need?
Offensive security isn’t a one-size-fits-all solution. Assessments range from passive scans to full-blown attack simulations.
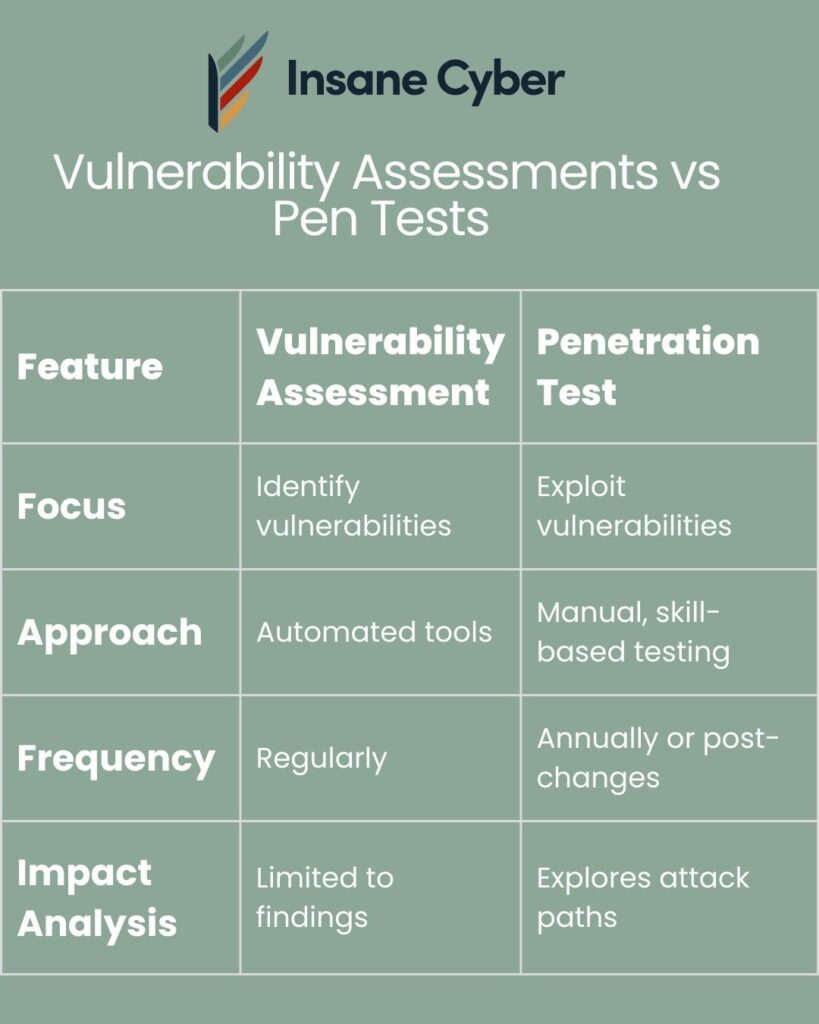
Vulnerability Assessments
A vulnerability assessment is a broad scan of your network, hosts, and systems to find known weaknesses. It’s a great starting point for identifying and prioritizing potential security flaws without actively trying to exploit them. Think of it as creating a map of potential problems.
Penetration Tests (Pentests)
A penetration test goes a step further by actively trying to exploit the vulnerabilities discovered. This simulates a real cyberattack to see how your defenses hold up and what the real-world impact of a breach could be. Pentesting in an OT environment must be done with extreme care to avoid disrupting operations.
Other specialized assessments include:
- Red Team Assessments: These focus on evading detection to test your organization’s monitoring and response capabilities.
- Device Penetration Tests: These target specific ICS hardware or vendor applications to find security flaws.
Recent SANS surveys show a growing adoption of these assessments, but there’s still a long way to go. While 75% of organizations conduct some form of annual OT security assessment, many still rely on paper-based methods. Only 25% have conducted a full penetration test. Moving toward more active, hands-on assessments is key to truly understanding and mitigating risk.
How to Conduct Safe and Effective ICS Assessments
The stakes are high in OT environments. A misstep during testing could cause a system outage or even a safety incident. That’s why a structured, cautious approach is critical.
Step 1: Pinpoint Your “Crown Jewel Assets”
Before you start any assessment, you need to know what you’re protecting. Work with your operations team to identify your Crown Jewel Assets (CJAs)—the critical systems or processes that would cause the most severe disruption if compromised. This could be a safety controller in a chemical plant or the master control server for a utility. By focusing on what matters most, you can prioritize your testing efforts on the worst-case scenarios.
Step 2: Choose Your Targets and Tactics
Once you know your CJAs, you need to think like an attacker. Review your network architecture to identify high-impact targets like PLCs, HMIs, or remote access points. When selecting the Tactics, Techniques, and Procedures (TTPs) to simulate, draw from real-world threat intelligence using frameworks like the MITRE ATT&CK for ICS. Focus on attacks that are relevant to your industry, whether it’s ransomware targeting manufacturing or remote exploits in the energy sector.
Step 3: Use a Phased and Methodical Approach
A successful assessment follows a clear, repeatable process that builds trust with the operations team.
- Plan and Scope: Work with all stakeholders to define clear goals, objectives, and rules of engagement.
- Gather Information (Passively): Start with non-disruptive methods. Conduct threat modeling, interview engineers and operators, perform site walkthroughs, and analyze network traffic to map your attack surface without touching live systems.
- Active Analysis (Carefully): Once you have a clear picture, you can move to controlled, active testing. This is where you might validate vulnerabilities or simulate specific attack scenarios.
Step 4: Test in a Controlled Lab Environment
The best way to understand the real-world impact of an attack without risking production is to replicate it in a lab. By building a controlled environment with similar hardware and software, you can safely:
- Simulate attacks like unauthorized commands or spoofed sensor data.
- Assess the physical outcomes of an attack on safety and control systems.
- Develop realistic attack scenarios that can be used for training and awareness.
Building Your ICS Security Skills
Effective OT penetration testing requires a unique blend of cybersecurity expertise and industrial knowledge. If you’re looking to move into this field, focus on building a strong foundation in:
- Cybersecurity Fundamentals: Understand risk assessment, common threats, and core security principles.
- Penetration Testing: Get hands-on experience with network and application testing.
- Digital Forensics: Learn how to investigate incidents in both IT and OT contexts.
- ICS/OT Basics: Gain a working knowledge of industrial components, protocols, and safety constraints.
Hands-on training courses are invaluable for developing these skills. Look for programs that include practical exercises like building ICS kits, analyzing industrial protocols, and running simulated red team scenarios in a lab environment.
Final Thoughts: From Assessment to Action
Both vulnerability assessments and penetration tests are vital for a strong ICS security program. By using a strategic combination of both, organizations can move from a reactive to a proactive security posture. The goal isn’t just to find flaws; it’s to gain actionable insights that strengthen your defenses, protect critical infrastructure, and ensure the continued safety and reliability of your operations.