The New Industrial Revolution Has a Major Security Flaw
We are in the midst of a new industrial revolution. The digital world of Information Technology (IT)—our networks, servers, and data—is merging with the physical world of Operational Technology (OT)—the industrial control systems (ICS) that manage power plants, factory floors, and transportation grids.
This IT/OT convergence is the engine of Industry 4.0. It allows companies to use real-time data and AI to make operations more efficient, predict maintenance failures, and streamline supply chains.
But this new connectivity comes at a steep price.
For decades, OT systems were “air-gapped,” meaning they were physically isolated from corporate IT networks and the internet. Their security was a locked door. Today, that air-gap is gone. By connecting industrial controls to the internet, we have created a new, high-stakes doorway for cyber adversaries, from ransomware gangs to nation-state hackers.
Attacks on these converged environments are no longer theoretical. They’re here, and their impact is measured in real-world disruption:
The Colonial Pipeline attack forced a multi-day shutdown of fuel pipelines, causing gasoline shortages across the U.S. East Coast.
The manufacturing sector has seen a dramatic spike in breaches, leading to production halts at major automotive and manufacturing plants.
The chilling TRITON malware was specifically designed to target and disable the safety systems of a petrochemical plant, demonstrating an attacker’s ability to cause physical destruction or even loss of life.
As these critical industries digitize, cybersecurity is no longer just about protecting data. It’s about protecting public safety, economic stability, and national security.

The 6 Core Challenges of IT/OT Security
Blending these two formerly separate worlds creates a unique set of security challenges that traditional IT security models are ill-equipped to handle.
1. The Vanishing Air-Gap Systems that were never designed to face internet-based threats are now connected to them. An attacker no longer needs physical access to a plant; they have a potential attack path from their laptop to a critical turbine or valve.
2. The Legacy Trap Many OT components—like the controllers running an assembly line or a power grid—are decades old. They often run outdated operating systems that can’t be patched and use industrial protocols (like Modbus or DNP3) that were built for trusted, closed networks. These protocols lack modern security basics like encryption and authentication.
3. The Uptime Dilemma In IT, you patch a vulnerability as soon as possible. In OT, you can’t. The top priority is availability and safety. Stopping a production line or a power grid to apply a patch—even for a few minutes—is often unacceptable and could cause significant operational or safety issues. This leaves a massive window of opportunity for attackers to exploit known, unpatched vulnerabilities.
4. The Cultural Clash IT and OT teams have fundamentally different priorities:
IT Security: Focuses on the “CIA Triad”—Confidentiality, Integrity, and Availability. Protecting data is paramount.
OT Security: Flips the model to Availability and Safety. Keeping the physical process running safely is the only thing that matters.
This “clash of cultures” means IT’s standard security policies (like forced password rotations or network scanning) can be seen as disruptive or even dangerous by OT engineers, leading to security controls falling through the cracks.
5. The Visibility Black Hole You cannot protect what you cannot see. Many organizations have robust tools for monitoring their IT networks, but almost no visibility into their OT environments. The proprietary nature of industrial equipment makes it difficult to use traditional IT tools to discover assets, let alone monitor them for threats. Attackers can hide in these blind spots for months.
6. The Exploding Attack Surface Every new Industrial IoT (IIoT) sensor, smart device, and remote-access laptop added to the network is another potential entry point for an attacker. A single weak link, like an insecure smart sensor, can become a pivot point to compromise the entire IT/OT ecosystem.
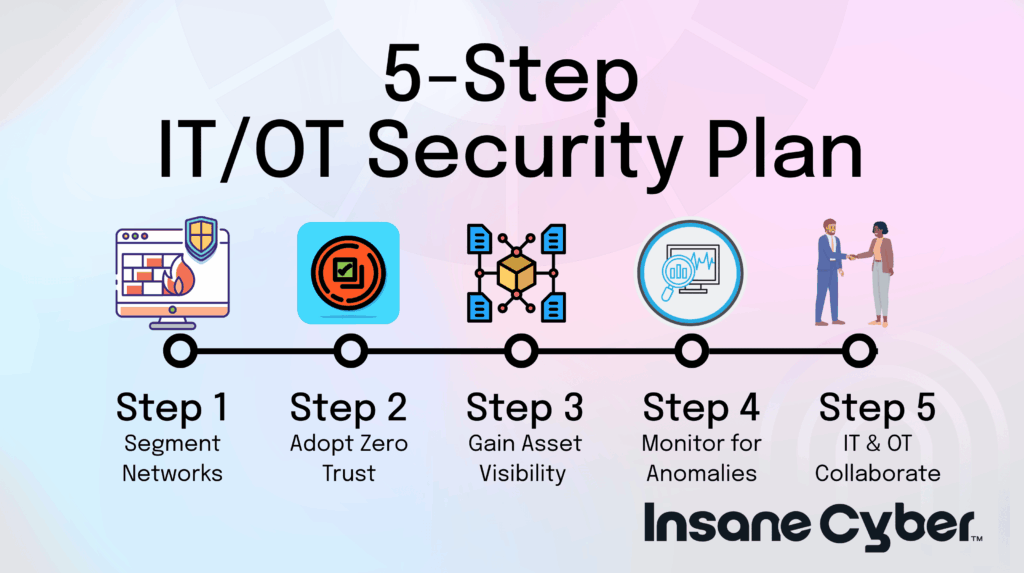
Building the Digital Fortress: A 5-Step Best Practice Guide
Securing a converged IT/OT environment is complex, but it’s not impossible. It requires a modern, defense-in-depth strategy that moves beyond old perimeter-based security.
1. Segment and Isolate If you can’t have an air-gap, create a virtual one. Use network segmentation to create strict zones that separate your IT and OT networks. A common practice is using a “demilitarized zone” (DMZ) that acts as a secure buffer. This ensures that even if malware hits your corporate email, it can’t jump directly to the plant floor.
2. Adopt a “Never Trust, Always Verify” Model This is the core of a Zero Trust Architecture. Assume that attackers are already inside your network. This means:
Enforcing strict access: Use multi-factor authentication (MFA) for any user, especially for remote access to OT systems.
Applying least privilege: An engineer should only have the exact access they need to do their job, and nothing more.
Securing critical accounts: Use Privileged Access Management (PAM) to lock down and monitor the “keys to the kingdom”—the administrator accounts for control systems.
3. See Everything: The Power of Asset Visibility You must know what’s on your network. Deploy passive monitoring tools specifically designed for OT environments. These tools listen to network traffic to safely identify and profile every device (PLCs, HMIs, sensors) without disrupting operations. This is the foundation for all other security.
4. Spot the Ghost in the Machine Once you have visibility, use continuous anomaly detection. These systems learn the “normal” operational baseline of your industrial network—what devices talk to each other, what commands they use, and what process values are normal. They can then instantly alert you to deviations that signal an attack, such as a laptop trying to reprogram a controller it’s never spoken to before.
5. Bridge the Human Divide Technology alone is not the answer. The single most important step is to break down the silos between IT and OT teams.
Create joint teams: Form a dedicated IT-OT cybersecurity task force.
Cross-train: Teach OT engineers about cybersecurity basics and teach IT security staff about industrial processes and safety.
Get executive buy-in: C-level and board support is essential to foster a culture where security and safety are seen as interdependent, not opposing, goals.
The Way Forward: Security as an Enabler
For CISOs and business leaders, OT security is no longer a niche technical problem—it is a core, board-level business risk. The good news is that by taking a proactive stance, security can become an enabler for innovation, not a blocker.
By embedding security into new industrial projects from the start (security-by-design) and adopting frameworks like ISA/IEC 62443, organizations can safely unlock the immense benefits of digital transformation. The convergence of IT and OT is the future, and those who secure it will be the ones to lead.