OT Incident Response
for Critical Infrastructure
A cyber event in your industrial environment is more than just an IT problem, it interferes with operations, safety, and more.
Our OT-first incident response helps you contain threats, return to uptime, and uncover what really happened—with expert guidance and specialized tools built for the job.
When Control Systems Are Under Fire,
You Need More Than an IT Playbook
Traditional incident response methods can fall flat, or cause harm, in OT environments.
The wrong move could interrupt operations, violate safety constraints, damage critical assets, or result in regulatory issues.
Our approach is tailored to the challenges you’re facing, because our team has been in your shoes. We understand the legacy systems, the industrial protocols, the methods attackers use, and how critical these systems are to operations.
The challenges IT teams may face in OT environments:
Limited logging on OT devices
No endpoint agents allowed
Flat networks with minimal segmentation
Complex vendor access and remote interfaces
Regulatory reporting timelines
Industrial cyber incidents, handled with precision
Our team is ready to bring the tools and knowledge to help you resolve and recover from incidents.
Core Response Capabilities
Rapid Threat Containment
Work side-by-side with your team to isolate impacted systems without taking down operations.OT-Capable Forensics & Analysis
We use our proprietary Valkyrie platform to collect and parse data from control systems, field devices, and industrial protocols—no agents, no disruption.Root Cause Investigation
Determine what happened, how it happened, and what it touched.Threat Hunting & Scope Validation
Identify lateral movement, command & control behavior, and persistence mechanisms across your ICS network.Remediation & Recovery Support
Help bring systems back online safely, with forensic evidence preserved and lessons applied, while also helping monitor for additional threats.Regulatory & Stakeholder Reporting
We support your compliance team with clear, timely documentation aligned to NERC CIP, TSA, EPA, and other relevant mandates.
Powered by people and purpose-built tools
We’ve trained for this and tested our skills in real environments. We know what’s at stake, and are ready with an arsenal of tools and knowledge to give you faster answers to make more informed decisions.
Deep OT Expertise – Industrial-focused responders with backgrounds in control systems, not just cyber.
Passive Forensics Tools – Built to safely extract data from switches, HMIs, controllers, and engineering workstations.
Protocol-Aware Analysis – We understand Modbus, DNP3, IEC 104, and more, and know what an abnormal function code looks like.
Evidence-Driven Results – Everything we do is logged, documented, and ready for internal or regulatory review.
When to call our team
Not every alert is a crisis, but every minute counts when it is.
You see unusual activity in your SCADA or DCS network
Systems are behaving abnormally, but you’re not sure why
You’re dealing with ransomware or suspected extortion
Remote access was misused—or left open too long
A regulator is asking hard questions after an event
You’re preparing for or recovering from a tabletop exercise and want to improve
You want to verify before calling in a large retainer
Even if you’re just suspicious, our team can help you quickly figure out what’s real and what’s just noise.
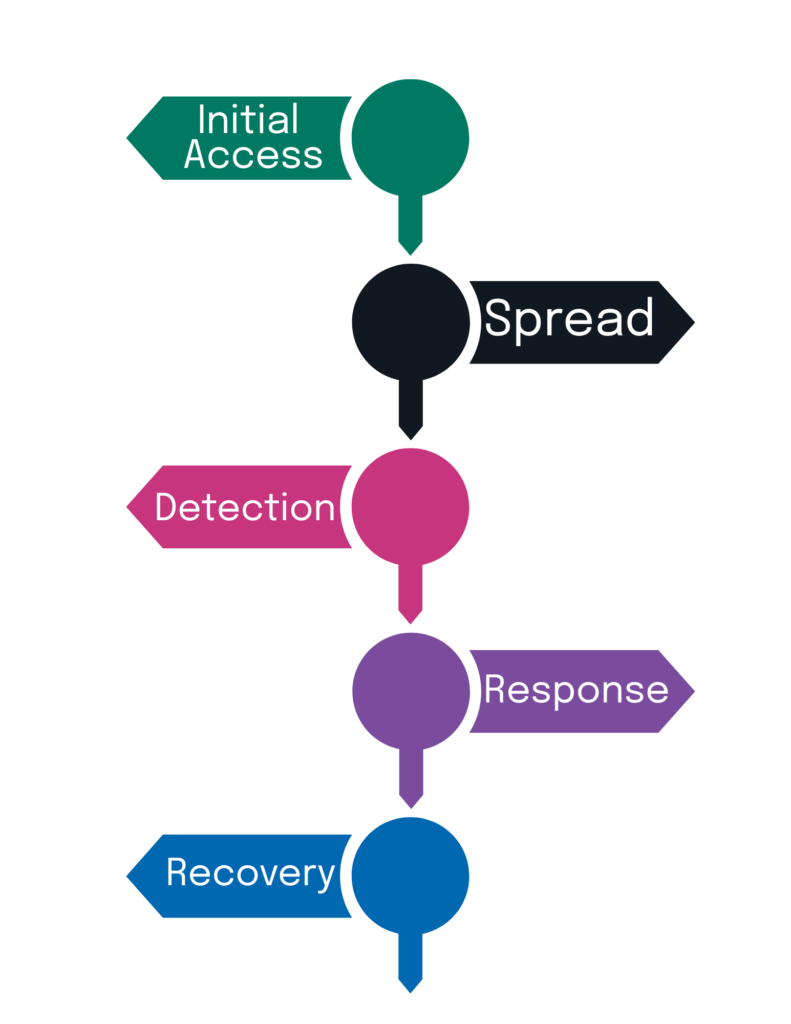
How it works
What you get
Activate – We jump in quickly via remote or on-site response, aligned with your escalation protocols.
Stabilize – Contain the threat without interrupting operations unnecessarily.
Investigate – Use OT-aware tools and techniques to uncover root cause and scope.
Remediate – Support patching, configuration changes, or system rebuilds where needed.
Report – Deliver a detailed, actionable report tailored to multiple audiences.
Recover & Harden – Help you restore service safely and strengthen defenses for next time.
Forensic investigation summary and timeline
Root cause and impact report
Recovery and containment actions taken
Remediation recommendations
Regulatory-ready incident report (optional)
Lessons learned + hardening roadmap
See how Insane Cyber transforms security
Our products are designed to work with
you and keep your network protected.



