Supervisory Control and Data Acquisition (SCADA) systems are the unsung heroes of our modern world. They quietly manage critical infrastructure – from power grids and water treatment plants to manufacturing lines and transportation networks.
But this critical role also makes them a prime target for cyberattacks. As these systems become increasingly interconnected, robust cyber monitoring isn’t just advisable; it’s essential.
Let’s dive into the tools, techniques, and evolving threat trends that security professionals need to navigate to keep these vital systems secure.
The Rising Tide: Why SCADA Systems Are in the Crosshairs
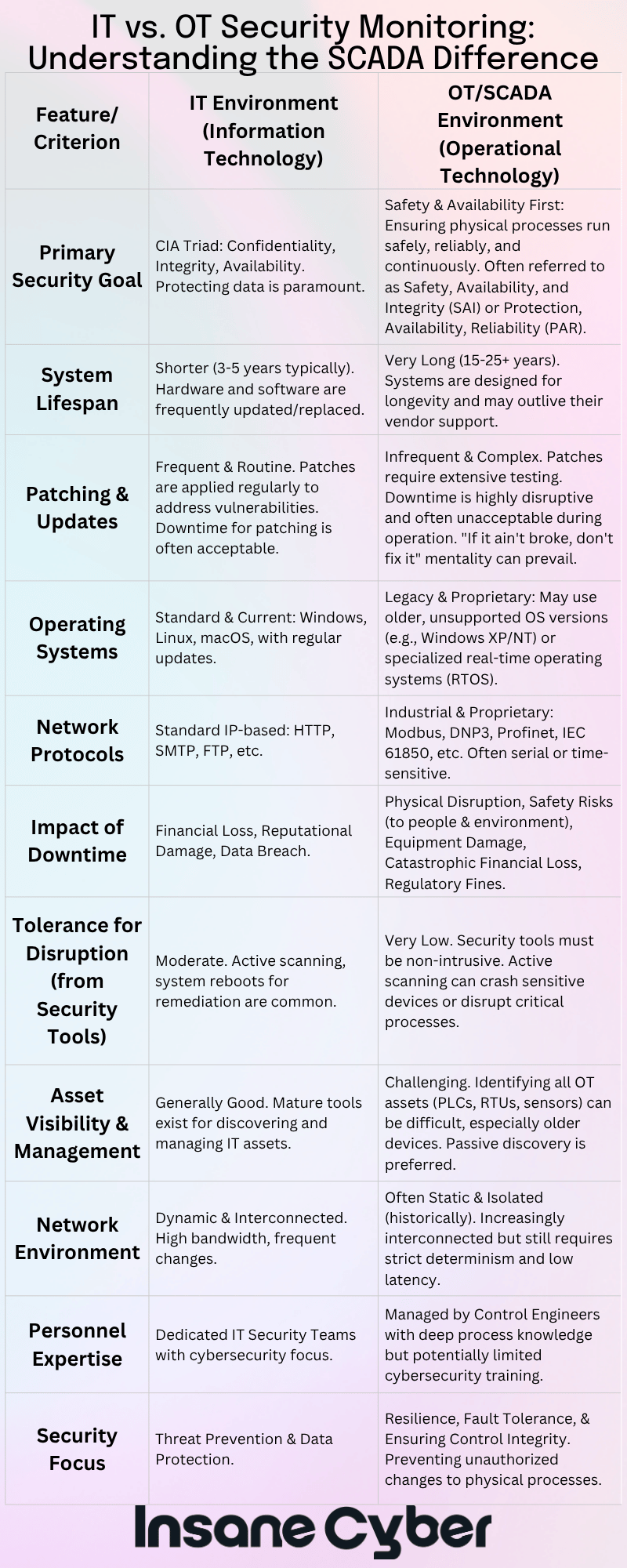
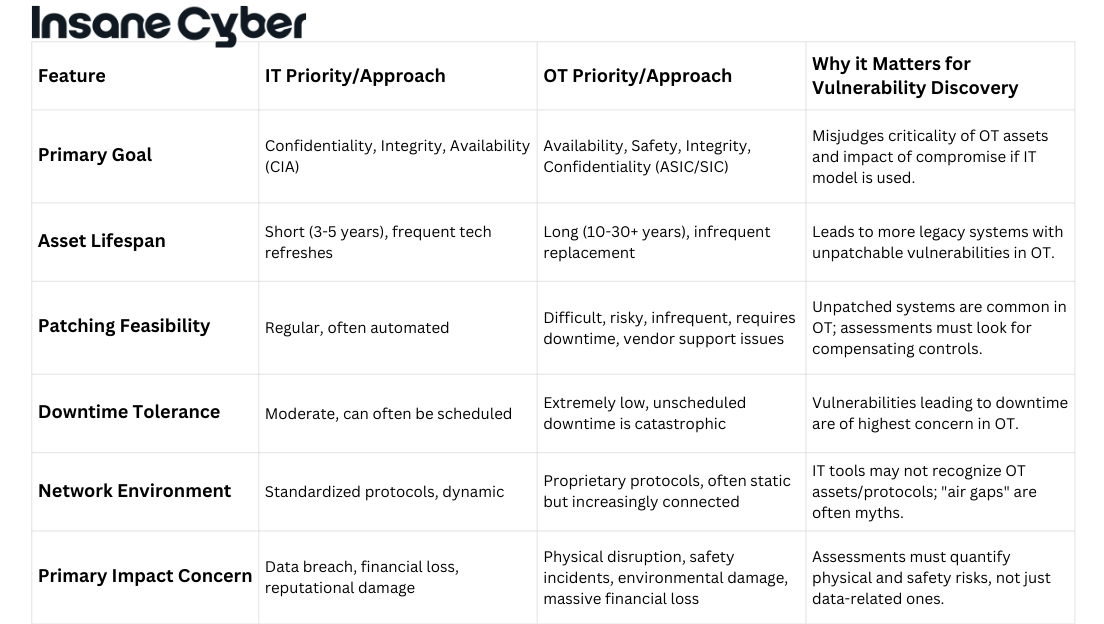
Historically, SCADA systems were often isolated, relying on “security through obscurity.” However, the drive for efficiency, remote access, and data integration with enterprise networks has brought them online, exposing them to a new world of cyber threats. The potential impact of a compromised SCADA system is immense, ranging from operational disruption and financial loss to environmental damage and even threats to public safety.
Understanding the adversary is key. Attackers targeting SCADA systems can range from disgruntled insiders and opportunistic hackers to sophisticated nation-state actors and organized cybercriminal groups. Their motivations are equally varied, including espionage, sabotage, and financial extortion through ransomware.
Emerging Threat Trends: What to Watch For
The threat landscape is anything but static. Staying ahead requires understanding the latest attack vectors and methodologies:
- Targeting IT/OT Convergence Points: As Information Technology (IT) and Operational Technology (OT) networks become more integrated, attackers are exploiting vulnerabilities at these convergence points to pivot from less secure enterprise systems into critical control environments.
- Ransomware with an OT Twist: Ransomware attacks are no longer confined to encrypting data. We’re seeing an alarming trend where attackers specifically target OT processes, threatening to disrupt physical operations unless a ransom is paid. This can halt production, disrupt essential services, and create significant safety risks.
- Sophisticated Nation-State Activity: Nation-state actors continue to show a keen interest in SCADA systems, often with the goal of reconnaissance, establishing persistence for future disruption, or outright sabotage. These attackers typically have significant resources and employ advanced, stealthy techniques.
- Exploitation of Remote Access: The increased need for remote operation and maintenance has expanded the attack surface. Weak or improperly secured remote access solutions provide a direct pathway for attackers into SCADA networks.
- Supply Chain Vulnerabilities: Attackers are increasingly targeting the supply chain, compromising software, hardware, or third-party vendors that have access to SCADA environments. A single compromised supplier can provide a foothold into numerous target organizations.
- AI-Powered Attacks (and Defense): Artificial intelligence is a double-edged sword. Attackers are exploring AI to automate reconnaissance, craft more convincing phishing attacks, and identify vulnerabilities faster. Conversely, defenders are also leveraging AI and machine learning for advanced anomaly detection and faster incident response.
- Attacks Aiming for Physical Disruption: A deeply concerning trend is the rise of attacks specifically designed to cause physical damage or disruption. This moves beyond data theft or encryption to actively manipulating control systems to unsafe states.
Essential SCADA Cyber Monitoring Tools
No single tool is a silver bullet. Effective SCADA monitoring relies on a layered security approach, utilizing a combination of specialized and traditional cybersecurity tools:
- Network Intrusion Detection/Prevention Systems (IDS/IPS): These are fundamental for monitoring network traffic for malicious activity or policy violations. For SCADA, IDS/IPS solutions often require deep packet inspection capabilities that understand industrial protocols (e.g., Modbus, DNP3, IEC 61850).
- Security Information and Event Management (SIEM): SIEM systems aggregate and correlate log data from various sources across the IT and OT environments. This provides a centralized view for security analysts to detect patterns indicative of an attack. Tailoring SIEM use cases for OT-specific threats is crucial.
- Asset Discovery and Inventory Tools: You can’t protect what you don’t know you have. Specialized OT asset discovery tools can identify and map all connected devices, including PLCs, RTUs, and HMIs, providing crucial visibility into the SCADA environment.
- Vulnerability Scanners: Regular vulnerability scanning helps identify known weaknesses in SCADA components and software. However, scanning in OT environments must be approached cautiously to avoid disrupting sensitive processes. Many organizations opt for passive scanning techniques or conduct scans during planned maintenance windows.
- Anomaly Detection Platforms: These tools establish a baseline of normal network and system behavior and then alert on deviations. In SCADA environments, this can be highly effective in detecting novel or zero-day attacks that signature-based tools might miss. Machine learning is increasingly powering these platforms.
- Endpoint Detection and Response (EDR) for OT: While traditional EDR is common in IT, solutions tailored for OT endpoints (like engineering workstations and HMIs) are emerging, providing better visibility and response capabilities for these critical assets.
- Industrial Firewalls: These are designed to segment SCADA networks, control traffic flow between zones, and understand industrial protocols to enforce security policies with greater granularity than traditional IT firewalls.
Effective SCADA Cyber Monitoring Techniques
Beyond tools, effective monitoring hinges on robust processes and skilled personnel:
- Network Segmentation: Dividing the SCADA network into distinct security zones limits the blast radius of an attack. Traffic between zones should be strictly controlled and monitored. Implementing Demilitarized Zones (DMZs) between IT and OT networks is a common best practice.
- Continuous Monitoring and Vigilance: SCADA environments require 24/7 monitoring. This involves not just automated alerts but also proactive threat hunting by security analysts who understand the nuances of industrial control systems.
- Protocol-Aware Monitoring: Deep understanding and monitoring of SCADA-specific communication protocols are essential to identify anomalous or malicious commands that could disrupt physical processes.
- Behavioral Analysis: Focus on understanding what constitutes normal operational behavior. This allows for the detection of subtle deviations that might indicate a compromised system or an insider threat.
- Configuration Change Monitoring: Unauthorized changes to PLC logic, HMI configurations, or network device settings can be early indicators of an attack. Implementing systems to detect and alert on such changes is vital.
- Secure Remote Access Protocols: Enforce multi-factor authentication (MFA), use VPNs with strong encryption, and limit remote access to only what is necessary and for the shortest duration required. All remote sessions should be logged and monitored.
- Regular Security Audits and Penetration Testing: Independent security assessments, including penetration tests specifically designed for OT environments (and conducted with extreme care), can help identify blind spots and validate the effectiveness of existing controls.
- Incident Response Plan: Have a well-defined and practiced incident response plan specifically for SCADA incidents. This plan should outline roles, responsibilities, communication channels, and procedures for containment, eradication, and recovery.
- Threat Intelligence Integration: Leverage industrial-specific threat intelligence feeds to stay informed about the latest TTPs (tactics, techniques, and procedures) used by adversaries targeting SCADA systems.
The Human Element and Proactive Defense
Technology alone isn’t enough. Skilled cybersecurity professionals with knowledge of both IT and OT environments are crucial. Regular training for operators, engineers, and security staff on SCADA cybersecurity best practices and threat awareness can significantly bolster defenses.
A proactive, defense-in-depth strategy is paramount. This involves not just detecting attacks but actively hunting for threats, continuously assessing and improving security posture, and fostering a culture of security awareness throughout the organization.
Securing the Future of Critical Infrastructure
SCADA cyber monitoring is a complex but non-negotiable aspect of modern industrial operations. As threats evolve in sophistication and frequency, organizations must invest in the right tools, implement effective techniques, and empower their people with the knowledge to defend these critical systems. By doing so, we can help ensure the continued reliability and safety of the essential services we all depend on.