Let’s face it, in today’s digital world, it’s not a matter of if a cyberattack will happen, but when. When that moment arrives and a security threat demands immediate action, a well-crafted Incident Response (IR) Plan is your organization’s lifeline. It’s the playbook that helps you minimize damage, kickstart recovery, and get back to business.
Think of an IR plan as your emergency preparedness kit for cyber threats. While every organization’s kit will look a bit different based on its unique needs, the best ones are built on proven frameworks. The National Institute of Standards and Technology (NIST) Special Publication 800-61 is a fantastic starting point, offering solid recommendations for handling security incidents. It’s a go-to resource whether you’re building an IR team from the ground up or fine-tuning your existing protocols.
While NIST is often seen as the gold standard, other respected frameworks like the SANS Incident Management process also offer invaluable insights. Most of these frameworks break down incident response into clear, actionable phases: getting ready (Preparation), spotting the trouble (Identification), stopping the bleeding (Containment), cleaning up the mess (Eradication), getting back on your feet (Recovery), and learning from the experience (Post-Incident Review). Handy resources like CISA’s Incident Response Plan Basics cheat sheet can also give you practical checklists as you draft your plan.
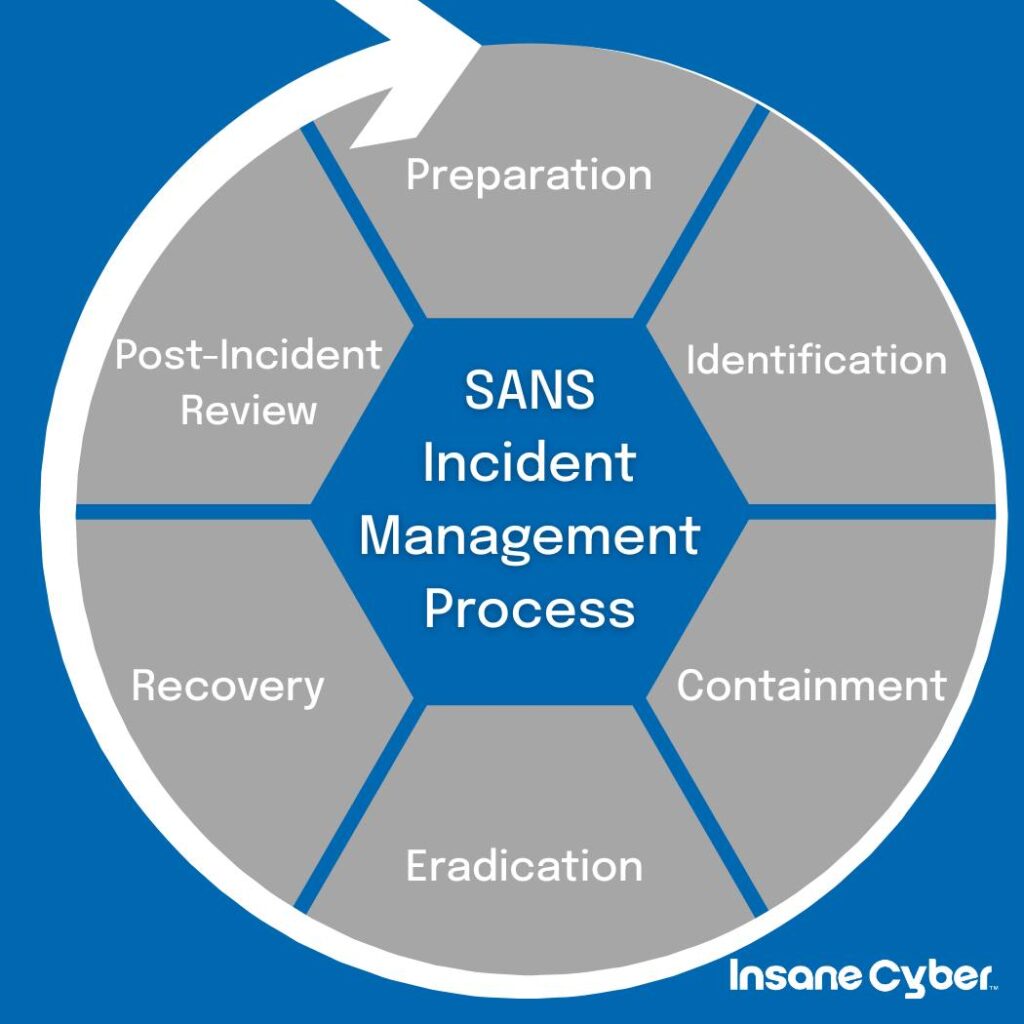
Tapping into these trusted sources ensures your IR plan isn’t just a document gathering dust, but a dynamic tool ready for action when a real-world security event unfolds.
In this article, we’ll dive into the essentials of incident response: how to get your response capability organized, effectively handle security incidents, and make sure everyone’s on the same page with information sharing.
Before you roll out your freshly minted IR plan, it’s worth acknowledging some of the real-world hurdles that can sabotage even the best-prepared teams. Here are a few common pitfalls to look out for:
By anticipating these snags and addressing them early, your organization will be far better positioned to turn your IR plan into a reliable safety net—rather than an afterthought.
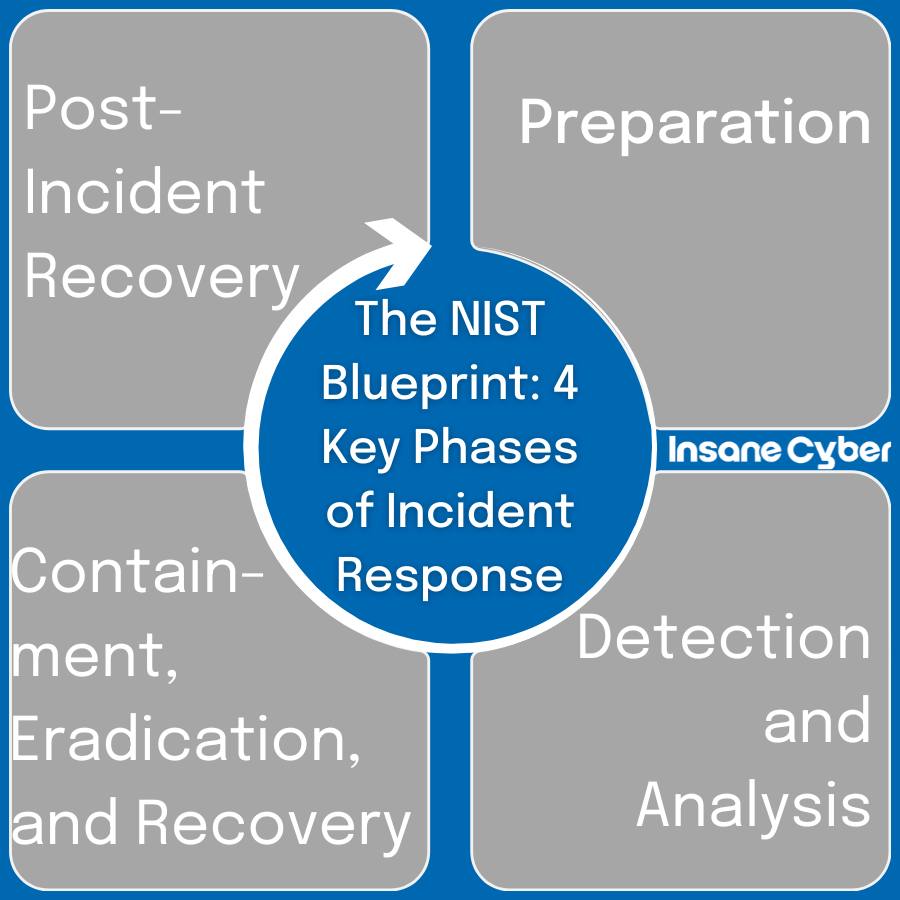
At the core of NIST’s SP 800-61 guidelines are four distinct stages. Understanding these helps any organization tackle threats methodically and effectively:
To build a robust IR framework, it’s important to understand the difference between three often-confused terms:
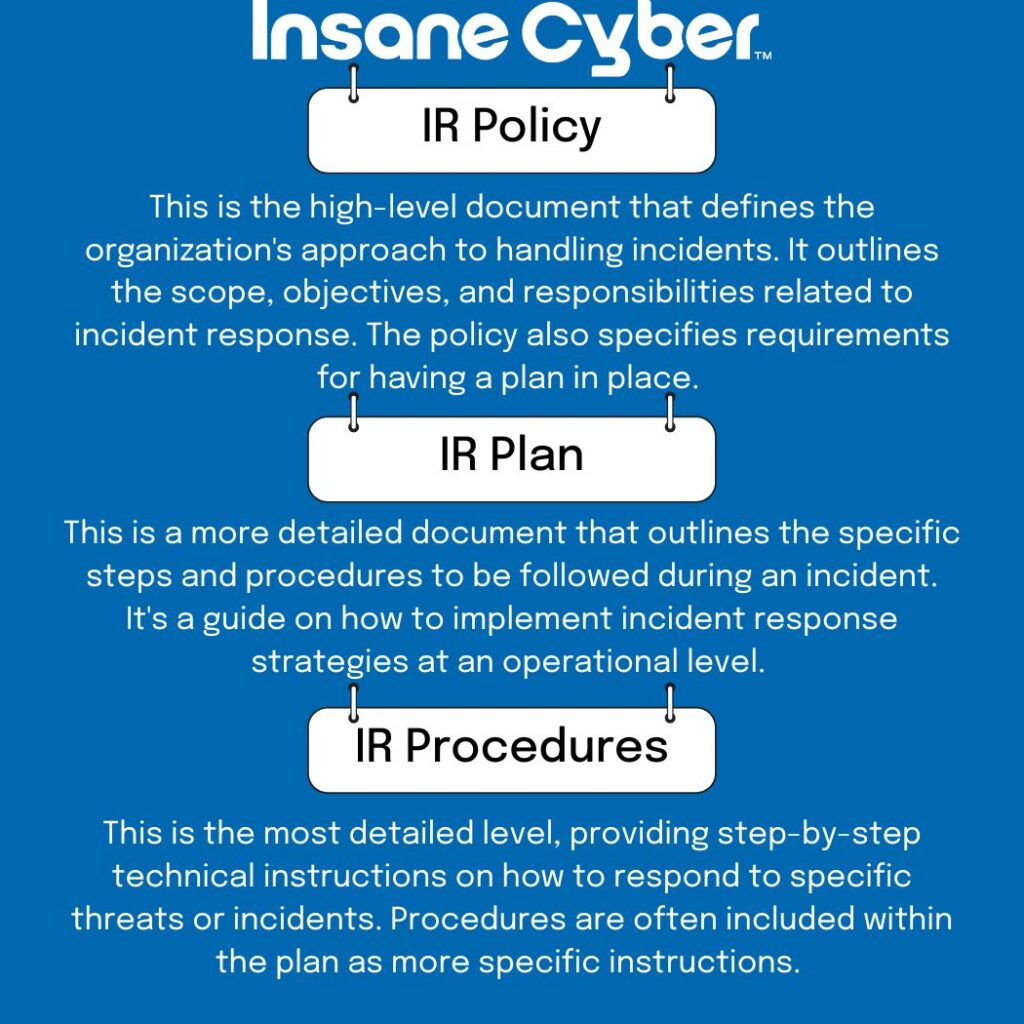
Let’s zoom in on crafting those crucial procedures.
Step 1: Anchor to Your IR Policy and Plan
Every single IR procedure needs to be firmly rooted in:
For instance, your IR policy might state a goal of resolving high-severity incidents within four hours. The IR plan would then outline the escalation paths and team structure, while the specific IR procedure would detail the exact technical steps and communication actions to take within that four-hour window.
To know if your procedures are working, you need to measure! The incident response team leader should diligently track and report on:
By basing every procedure on clear responsibilities and business needs, and by consistently measuring your performance, you build an IR approach that’s not only actionable but also constantly getting better.
Step 2: Clarify Who Handles What
Avoid a “too many cooks in the kitchen” scenario or, worse, having critical tasks fall through the cracks. Clearly define which teams or individuals are responsible for specific types of threats. This stops redundant efforts and ensures the right people are prepped for the incidents they’re most likely to handle.
Build Your Core and Extension Response Teams
Start by establishing your Cybersecurity Incident Response Team (CSIRT). This should include a clearly documented list of roles and responsibilities, along with up-to-date contact information for each member—whether you keep that info front-and-center or tucked away in an appendix.
At the core, designate an incident response lead (IRL)—often the Chief Information Security Officer (CISO), Director of Security, or another senior security figure. Surround them with a cross-functional team drawn from security operations, security management, legal, and privacy. These are the folks who should be ready to jump in at a moment’s notice, handling the majority of incidents your organization might face.
But don’t stop there. Identify an extension team that can be activated for specific scenarios. This broader group might include people from human resources, marketing, physical security, law enforcement liaisons, and other departments relevant to certain incidents (think: HR for insider threats, communications for public messaging, or facilities for physical breaches). By having these roles mapped out in advance, you ensure no critical perspective is missing when the pressure is on.
The Crucial Role of Communicating with Executive Leadership
You can have the best technical response in the world, but if your leadership is in the dark, you’re fighting an uphill battle. Designate a specific point person – often the Chief Information Security Officer (CISO) or another senior leader – to manage all updates to executive leadership.
This person’s job is to translate complex technical details into clear, concise, business-relevant language. The C-suite and board need to understand the scope of the incident and its potential impact on operations, finances, or reputation. Timely, easy-to-understand updates empower leadership to make informed decisions, allocate necessary resources, and effectively manage stakeholder concerns – whether that means coordinating with legal teams on GDPR obligations or preparing statements for customers. Clear reporting bridges the gap between IT trenches and strategic decision-making.
Step 3: Factor in Your Unique Environment
No two organizations are identical, and your IR procedures must reflect your specific operational landscape:
Navigating the Regulatory Maze in Incident Response
Regulatory obligations are a huge driver in how organizations must respond to and report cybersecurity incidents. For example, publicly traded companies in the U.S. now have the SEC breathing down their necks with rules mandating the disclosure of “material” cybersecurity incidents, often within a tight four-business-day window.
This means your IR procedures must explicitly cover:
By baking regulatory considerations directly into your IR plan, you avoid frantic, last-minute scrambles and significantly reduce the risk of non-compliance. Always stay current with applicable laws like GDPR, SEC requirements, or industry-specific mandates.
Keeping Everyone Accountable: Compliance with Your IR Plan
Building a robust incident response plan is just step one—the real challenge is making sure everyone follows it when it counts. To ensure teams stick to the script, lay out clear expectations for what compliance looks like, and regularly audit processes to check that procedures are actually being followed. This can include scheduled tabletop exercises, after-action reviews, and routine policy reviews with both frontline staff and leadership.
But what if someone—or an entire team—doesn’t adhere to the plan? Transparency is crucial. Specify the consequences of non-compliance upfront, ranging from additional training for minor slip-ups to formal disciplinary action for repeated or serious breaches. Aligning your approach with HR policies and internal codes of conduct helps set a fair, consistent standard.
Treat compliance as a living process. Make evaluation and feedback loops a regular part of your IR lifecycle. The threat landscape evolves, new regulations emerge, and your organization changes—all of which means your plan and your compliance strategy need to keep pace. Ongoing testing, periodic reviews, and a culture of continuous improvement aren’t just “nice-to-haves”—they’re essential to turning your IR plan from a binder on a shelf into real organizational resilience.
Step 4: Let Severity Guide Your Response Actions
Not all incidents are created equal. The severity of an incident should directly dictate the intensity and nature of your response:
Incident Classification and Tailored Response
Classifying incidents by severity isn’t just for initial triage; it ensures the right people take the right actions at the right time. For every incident, consider:
Building and Using a Risk Classification Matrix
Now, let’s talk about one of the unsung heroes of any effective IR plan: the risk classification matrix. Think of it as your playbook for sizing up an incident’s potential harm and urgency at a glance.
A risk classification matrix is simply a tool that helps you systematically evaluate incidents based on how severe they are and how quickly they need attention. By mapping incidents against factors like business impact (e.g., data loss, service downtime, reputational hit) and urgency (how fast a response is needed), you can quickly determine which procedures to activate and who gets the 3 a.m. phone call.
Here’s how you should use it:
By formalizing thresholds and actions in your matrix, you create clarity and consistency—preventing both underreaction to a simmering threat and overreaction to harmless network hiccups. As with everything in incident response, revisit and update your matrix regularly to keep pace with new threats and changes in your environment.
Documentation and Communication (Yes, it’s that important!)
Regardless of severity, meticulously document every action taken, decision made, and piece of evidence collected. This is absolutely vital for internal reviews, potential insurance claims, and meeting those external regulatory requirements (like the SEC’s four-business-day rule or GDPR notifications). Again, assign a specific person to keep stakeholders updated in plain English.
The Power of the Post-Incident Review
Once an incident is contained and systems are recovered, it’s time for a “post-mortem” or “lessons learned” session. This should be a blameless, open forum to discuss:
Regular Review and Continuous Improvement
But don’t stop there. An incident response plan (IRP) is a living document, not a dusty binder on a shelf. Make it part of your routine to regularly revisit and test your IR procedures. Tabletop exercises, where you walk through a scenario, and simulated attacks (like controlled phishing campaigns) are invaluable for ensuring your team is truly ready.
It’s recommended to formally review, update, and re-approve your IRP at least once a year—and always after any significant operational or organizational change, or following a real-world incident or exercise. Assign clear roles for who owns this review process and who gives final approval.
After every exercise or real incident, evaluate what you learned and use those lessons to refine your plan. If your organization undergoes major changes—like an IT infrastructure upgrade, a shift in business operations, or a new regulatory requirement—trigger an immediate review and update of your IRP. This ensures your plan always reflects your current reality and the evolving threat landscape.
Regular, meaningful reviews and rigorous testing are what transform your incident response plan from a checkbox into a real-world safety net.
Step 5: Develop a Crystal-Clear Communication Plan
A robust incident response capability hinges on effective communication. Your dedicated communication plan within the broader IR plan should clearly answer:
Establishing these communication channels before a crisis hits eliminates confusion and supports swift, coordinated action when you’re under pressure.
(Stay tuned for Part 2, where we’ll delve into the practical TTPs, building your IR team, and sustaining cyber resilience!)
Need a Hand Getting Started? Crafting a comprehensive Incident Response Plan can feel daunting. If you’re looking for expert-led IR training, tabletop exercises, or help customizing a hands-on OT Incident Response Workshop for your organization’s unique needs, don’t hesitate to reach out. We can help you build the resilience you need.
Our products are designed to work with
you and keep your network protected.