For years, operational technology (OT) cybersecurity has been treated as a network problem. If you could see the traffic, the thinking went, you could stop the threats.
That model made sense when plants and grids were relatively isolated, but the world has changed. OT networks are now deeply connected to IT, cloud services, and remote operations. Attackers have taken notice, and they know how to exploit the blind spots defenders still leave open.
The most dangerous of those blind spots? Host data.
Host Data: The Missing Half of the Story
Network monitoring is essential, but it only shows you what moves between devices. It’s like watching security cameras in the hallways of a facility. You know when someone walks into a room, but you have no idea what they do once inside.
Host data is what happens inside the room—the configuration of your PLCs, the logic running your pumps and turbines, the firmware keeping your HMIs stable, and the logs showing exactly who accessed what and when. It’s the microscope focused on your most critical machines.
Ignore host data, and you’re essentially guarding the gates while leaving the control room unattended.
Why the Blind Spot Is a Critical Vulnerability
Attackers know how to exploit this gap. They can:
- Upload a “routine” project file that subtly alters safety thresholds.
- Change setpoints in a chemical process without raising a network alarm.
- Slip malicious payloads into communications that look legitimate on the wire.
From a network-only perspective, everything appears normal. The right protocol, the right devices, the right communication patterns. Meanwhile, the logic inside a PLC has been quietly compromised.
That’s why the blind spot isn’t just an oversight, it’s an open invitation. And when the consequences can include outages, environmental harm, or safety risks, it’s a vulnerability no utility can afford to ignore.
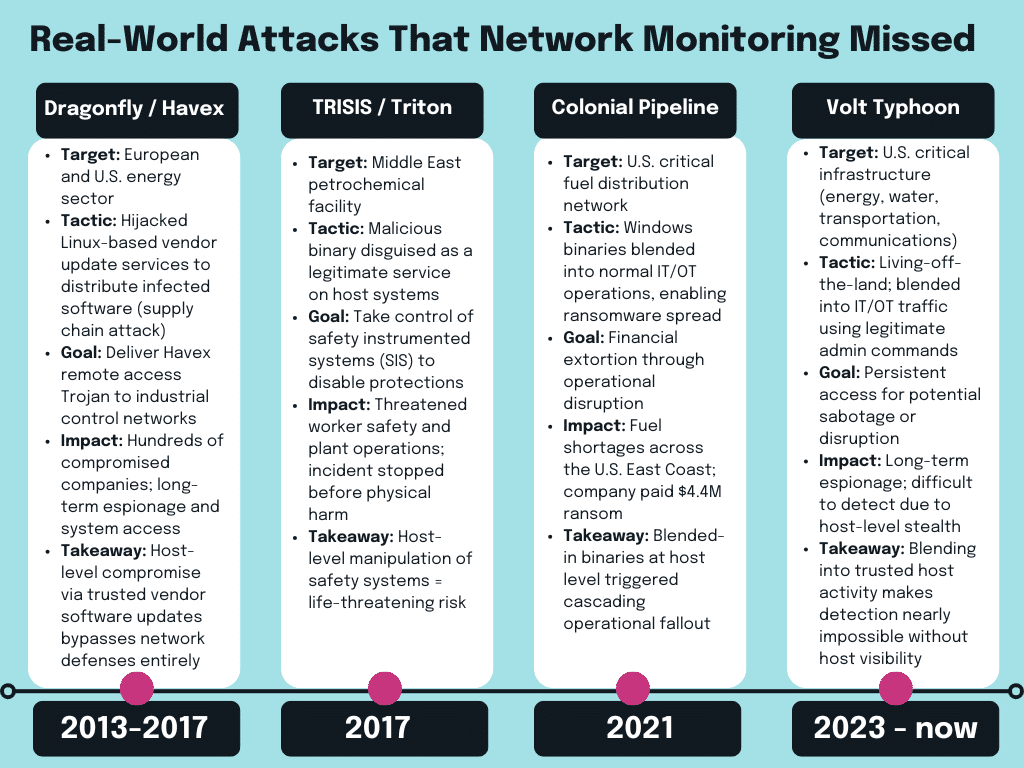
Real-World Attacks That Exploited Host Data
This isn’t theory—it’s happening. Some of the most significant OT cyber incidents have hinged on manipulating host-level processes or blending into trusted services:
- TRISIS / Triton: This malware deployed a binary disguised to look like a legitimate service on infected hosts. Its goal was chilling: to take control of industrial safety systems, threatening not just operations but the lives of workers on site.
- Colonial Pipeline: While known primarily as a ransomware story, this attack spread via Windows binaries designed to blend into normal operations, crippling fuel supply across the U.S. East Coast.
- Volt Typhoon: This state-sponsored campaign embedded itself in IT and OT environments by mimicking legitimate administrative commands and traffic patterns—effectively hiding in plain sight.
- Dragonfly / Havex: This threat actor group hijacked Linux-based vendor update services, pushing out infected software packages that were trusted by industrial operators, spreading compromise through the supply chain.
Each of these attacks took advantage of trust at the host level—something that network monitoring alone could not expose in time.
Meeting Compliance While Staying Ahead of Threats
For utilities, the challenge is twofold: stay ahead of increasingly sophisticated attacks while also proving compliance with strict regulatory frameworks like NERC CIP. That’s where Valkyrie, Insane Cyber’s continuous OT monitoring platform, changes the game.
Developed by OT cybersecurity experts, Valkyrie delivers a single pane of glass into both host and network activity. It combines deep protocol inspection with device-level visibility, ensuring operators are never left in the dark.
Key capabilities include:
- Continuous monitoring across industrial networks, down to device-level activity.
- Behavioral baselining that flags suspicious deviations before they escalate.
- Audit-ready reporting that generates regulator-ready evidence with minimal effort.
- Customizable alerts and SOC integration to fit seamlessly into existing workflows.
The Path Forward
The industry can no longer afford to view OT cybersecurity as a compliance checkbox or a matter of monitoring traffic alone. The threats are real, the stakes are physical, and the blind spot is too dangerous to ignore.
The future of OT defense is full visibility: network plus host, working together.
That’s not just good security—it’s the foundation of resilience.