In the relentless cat-and-mouse game of cybersecurity, attackers constantly seek footholds. One of the most consistently abused avenues? Remote Desktop Protocol (RDP). Whether it’s exposed to the wild web or used for lateral movement within your network, RDP is a prime target. But what if I told you one specific Windows event ID could be your ace in the hole for spotting this and other malicious activity?
Today, we’re diving deep into what might just be the most valuable event ID for your threat hunting arsenal: Windows Event ID 4624.
If you peek into the MITRE ATT&CK framework, specifically technique T1021.001 (Remote Desktop Protocol), you’ll see just how common this attack vector is. Attackers love RDP for moving across trust boundaries, be it from an external point into your network or internally between different zones.
Alarmingly, a quick search on services like Shodan can reveal millions of RDP instances exposed to the internet. While some are undoubtedly honeypots, a significant number are genuine, potentially vulnerable systems.
But even if your RDP isn’t internet-facing, don’t tune out. This event ID is still incredibly crucial. Imagine an attacker gains initial entry – perhaps via a phishing email and then deploys a tool like Mimikatz to harvest credentials. What’s often next? They might use those stolen credentials with RDP or another network-authenticated service to pivot and burrow deeper into your environment.
So, whether you’re worried about external RDP exposure or internal lateral movement, Event ID 4624 is your friend. It’s a go-to for tracking not just attacker activity but also potential insider threats.
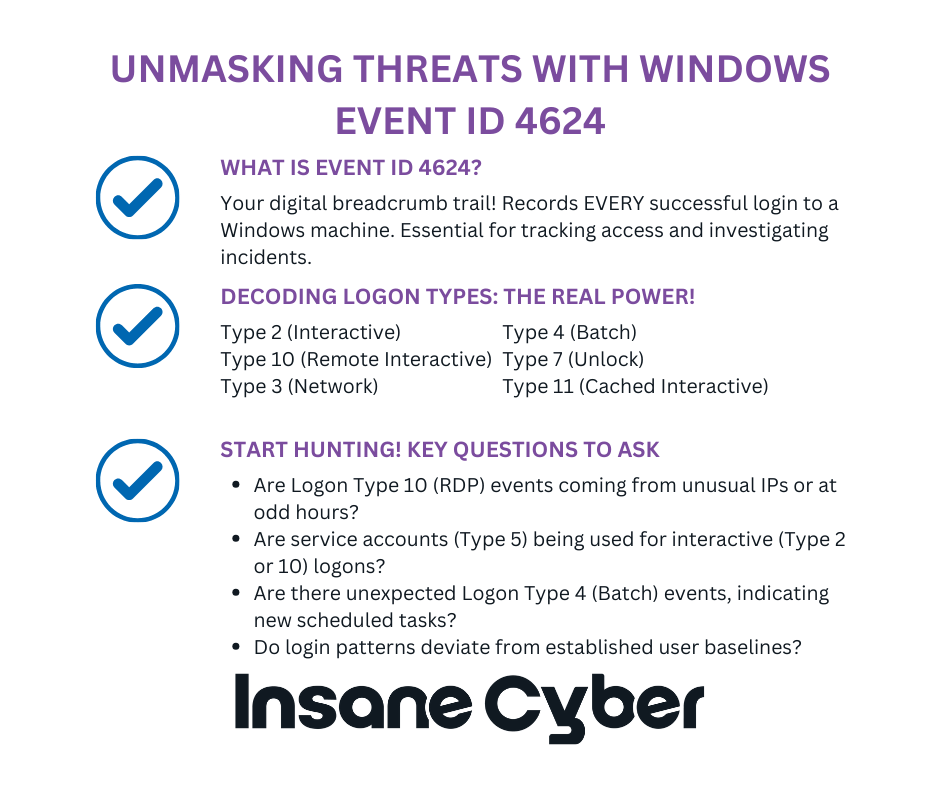
So, what exactly is Windows Security Log Event ID 4624? In simple terms, it records every successful authentication request to a Windows machine.
This isn’t just a simple “someone logged in” message. It’s packed with valuable forensic data:
While we’re focusing on successful logons (4624), it’s also wise to keep an eye on Event ID 4625 (failed logons). But for today, 4624 is our star.
(Pro-tip: For an excellent free resource, check out the “Ultimate Windows Security’s Encyclopedia of Security Logs.” It often provides sample logs and field explanations, which is invaluable if you don’t have a specific event in your own logs yet.)
The “Logon Type” field within Event ID 4624 is where things get really interesting. This single field gives you critical context about how the logon occurred. Here are some of the most important Logon Types you need to know:
By understanding these Logon Types, you can quickly discern between someone physically at a machine versus a remote RDP session, or a scheduled task versus a network share access. This context is vital for effective threat hunting.
Imagine sifting through gigabytes, even terabytes, of these logs. Manually, it’s a nightmare. This is where Security Information and Event Management (SIEM) tools or log analysis platforms like the ELK Stack (Elasticsearch, Logstash, Kibana) become indispensable.
You can ingest these Windows Event Logs (using methods like Elastic Beats, Logstash forwarders, or even custom scripts like evtx_to_elk if you’re dealing with raw EVTX files) and then build dashboards and queries to pivot through the data.
For example, you could easily filter by Logon Type, then look at the source IPs, usernames, and processes involved. You can see which processes are initiating which types of logons (e.g., user32.dll for cached interactive, advapi32.dll or other service processes for service logons). You can also see the account names, including Microsoft accounts (which might show up as an email address).
The ability to quickly slice and dice this data, search for specific text strings within raw logs, and visualize patterns is what elevates your threat hunting from tedious to powerful.
So, how do you turn this data into actionable intelligence? Here are a few starting points for your threat hunts using Event ID 4624:
Baseline Your ‘Normal’:
Hunt for Anomalous RDP (Logon Type 10):
Spot Out-of-Hours Activity & Unusual Account Usage:
Connect the Dots in an Attack Chain:
Investigate Scheduled Task Abuse (Logon Type 4):
These are just a few generic ideas. As you become more familiar with your environment and the specifics of your threat hunts, you’ll develop even more targeted hypotheses.
While we’ve highlighted RDP, remember that Event ID 4624, with its various Logon Types, provides visibility into a wide range of authentication activities. It’s a foundational log source for uncovering many different MITRE ATT&CK techniques.
Windows Event ID 4624 is more than just a log entry; it’s a rich source of truth for understanding who is accessing your systems and how. By mastering its nuances, especially the different Logon Types, you significantly enhance your ability to detect, investigate, and respond to cyber threats.
So, start digging into your 4624 events. You might be surprised by what you find. Happy hunting!
Our products are designed to work with
you and keep your network protected.