The Unseen Dangers in Your Industrial Operations
The operational technology (OT) that underpins our industrial world is undergoing a profound transformation. Increased digitization and connectivity promise unprecedented efficiency and innovation.
However, this evolution simultaneously broadens the attack surface, exposing critical infrastructure to a rising tide of cyber threats. The stakes could not be higher. Unplanned downtime alone costs industrial manufacturers an estimated $50 billion annually. For specific sectors, the figures are even more alarming: the automotive industry, for example, can hemorrhage $2.3 million for every hour of lost production.
Despite these stark realities, a critical gap persists in how many organizations approach OT security. Traditional risk assessments, often designed with information technology (IT) environments in mind, frequently fail to identify or adequately weigh vulnerabilities unique to the OT domain. It is crucial to distinguish between IT and OT cybersecurity requirements to effectively protect not only data but also the physical industrial operations that are vital to our economy and safety.
This article aims to illuminate five commonly overlooked OT vulnerabilities, explore the reasons they are often missed, discuss their potential impact with supporting data, and offer actionable guidance for bolstering your defenses. The fundamental differences in operational priorities between IT and OT environments often lead to these blind spots.
Why Standard Risk Assessments Falter in OT Environments
The efficacy of any risk assessment hinges on its ability to accurately model the environment it evaluates and the priorities it must protect. When standard, IT-centric risk assessment methodologies are applied to OT environments, they often fall short due to fundamental incompatibilities.
The IT vs. OT Security Triad Misalignment:
A core tenet of information security is the CIA triad: Confidentiality, Integrity, and Availability. In traditional IT environments, protecting the confidentiality of data is often paramount. However, in OT environments, the priorities are inverted. The primary concern is Availability – ensuring continuous operation of physical processes – followed by Integrity – ensuring that data and control commands are accurate and reliable. Confidentiality, while still important, typically ranks third.
This is often referred to as the AIC (Availability, Integrity, Confidentiality) triad, or sometimes the SIC triad, explicitly including Safety. This fundamental difference in priorities means that risk calculations and mitigation strategies derived from an IT-centric model can be dangerously skewed when applied to OT.
The Elusive Asset Inventory:
A comprehensive and accurate asset inventory is the bedrock of any effective risk assessment. Yet, in OT environments, achieving this is a monumental challenge.
OT landscapes are often dynamic, with assets being added, removed, or modified frequently without centralized IT oversight. These environments are typically populated with a diverse array of legacy systems, some of which may have been operational for decades.
Such systems often lack detailed documentation, may not be compatible with modern network scanning and inventory tools, and may run on proprietary protocols unfamiliar to IT teams.
This results in poor visibility into the OT environment, with an estimated 42% of enterprise assets being agentless and potentially unmanaged. The adage “you can’t protect what you can’t see” is particularly pertinent here. An incomplete or inaccurate asset inventory directly translates to unassessed devices and, consequently, unmitigated vulnerabilities.
Unique OT Complexities:
Several other factors contribute to the inadequacy of standard risk assessments in OT:
- Proprietary Protocols and Systems: Many OT devices utilize specialized, vendor-specific communication protocols (e.g., Modbus, DNP3, Profibus) that are not well understood or parsed by traditional IT scanning tools. This can lead to these devices being misidentified or missed entirely during assessments.
- Extended Lifecycles and Patching Dilemmas: Unlike IT assets, which typically have refresh cycles of 3-5 years, OT equipment can remain in service for 10, 20, or even 30 years. Patching these systems is often fraught with difficulty. Continuous uptime requirements may preclude taking systems offline for updates, vendors may no longer support older equipment, or there may be legitimate fears that a patch could disrupt critical processes. This “patching paradox” in OT means that systems often remain vulnerable for extended periods.
- Complex Interdependencies: OT systems are often intricately interconnected. A seemingly minor change or failure in one component can have unforeseen cascading effects on other systems and processes. Risk assessments must be capable of understanding and modeling these complex relationships.
- Physical Impact: Crucially, OT systems interact with and control the physical world. Cyberattacks are not limited to data breaches; they can result in physical damage to equipment, disruption of essential services (like power or water), environmental incidents, and even threats to human safety.
The lack of standardized OT-specific risk assessment methodologies and a persistent scarcity of cybersecurity professionals with deep OT expertise further exacerbate these challenges. In the absence of tailored frameworks and specialized knowledge, organizations often default to applying familiar IT-centric approaches, or they may engage consultants who also lack the necessary OT context.
This perpetuates a cycle where the unique risks inherent to operational technology are systematically undervalued or misunderstood, often leading to a dangerous and unwarranted sense of security.
To illustrate these fundamental differences, consider the following:
Table 1: Key Differences in IT vs. OT Risk Assessment Focus

The 5 Overlooked OT Vulnerabilities (And How to Spot Them)
Given the unique characteristics and challenges of OT environments, several critical vulnerabilities are frequently missed by standard risk assessments. Understanding these blind spots is the first step toward a more robust security posture.
Vulnerability 1: “Shadow OT” and Unmanaged Machines
“Shadow OT” refers to any undocumented, unmanaged hardware or software in the OT environment. This includes unauthorized devices like personal laptops or USB drives, unapproved software, and forgotten assets such as old PLCs, sensors, or network segments still connected but no longer tracked or maintained.
- Why Missed: Assessments rely on existing inventories. Without continuous, OT-aware discovery, these lists become outdated, and rogue devices go unseen.
- Impact: Unmanaged assets often lack basic security. 42% of enterprise assets are agentless, and networks average over 50 high-risk devices. Shadow IT is linked to nearly half of all cyberattacks.
- Fix It: Use continuous asset discovery tools. Enforce strict policies for new devices. Conduct regular audits.
Vulnerability 2: Unsafe “Out-of-Band” HMI Access & Exposed Interfaces
This vulnerability involves Human-Machine Interfaces (HMIs), engineering workstations, and other OT interfaces accessible via insecure channels. Examples include:
OT devices exposed to the public internet without protections like firewalls, VPNs, or MFA
Remote access via unmanaged tools—e.g., personal TeamViewer accounts, unsecured vendor VPNs, or misconfigured cellular modems with default credentials or public IPs
These “out-of-band” access points bypass the organization’s secure, managed network and its controls.
- Why Missed: Assessments might confirm remote access is possible but not check how. Standard IT scans may not detect internet-exposed OT devices or unmanaged remote access software. An exposed HMI is a critical vulnerability.
- Impact: Exposed HMIs offer direct pathways for attackers. Globally, ~145,000 Industrial Control Systems (ICS) are exposed online. 65% of assessed OT environments had insecure remote access conditions.
- Fix It: Remove OT systems from direct internet exposure. Secure essential remote access with VPNs, MFA, and least privilege. Prohibit unmanaged remote access tools.
Vulnerability 3: Compromised Third-Party and Vendor Access
This category covers risks from external parties—like vendors, integrators, and contractors—who access OT networks or supply components. Threats include compromised vendor software or updates (e.g., HAVEX), embedded vulnerabilities, and insecure remote access for support or maintenance.
- Why Missed: Assessments often focus internally. Complex supply chains and lack of Software Bills of Materials (SBOMs) hinder thorough third-party vetting.
- Impact: 90% of large energy firms reported a vendor-related data breach. Compromised remote access (often used by vendors) was implicated in 50% of industrial ransomware incidents. Software supply chain attacks surged 742% (2020-2023).
- Fix It: Implement stringent Third-Party Risk Management (TPRM). Secure and monitor all vendor remote access. Validate software updates.
Vulnerability 4: Insufficient or “Flat” Network Segmentation
Network segmentation – the practice of dividing a larger network into smaller, isolated subnetworks or zones – is a foundational security principle for OT environments. Proper segmentation aims to separate critical OT systems from the corporate IT network and to create distinct zones within the OT environment based on criticality and function (e.g., using the Purdue Model).
- Why Missed: Assessments may review diagrams but not actively test segmentation effectiveness. Focus might be on IT/OT boundary, neglecting internal OT micro-segmentation. Operational resistance can lead to unapproved exceptions becoming backdoors. Having unmonitored network parts often correlates with poor segmentation.
- Impact: Poor segmentation enables rapid malware spread, like ransomware. Attackers can achieve lateral movement easily. Over 50% of ransomware victims reported OT impact even if OT wasn’t initially infected, due to poor segmentation.
- Fix It: Implement granular network segmentation (Purdue Model, Zero Trust). Regularly audit firewall rules. Conduct penetration tests.
Vulnerability 5: The Human Element: OT-Specific Security Unawareness
This vulnerability extends beyond generic cybersecurity awareness (like recognizing phishing emails) and delves into human behaviors and knowledge gaps specific to the OT context. OT personnel lacking training on OT-specific cyber threats; risky practices due to operational pressures (e.g., using unauthorized USBs, sharing credentials); IT/OT cultural divides; or failure to follow patching procedures.
- Why Missed: Assessments may verify general awareness training but not its OT relevance. Risky behaviors and cultural factors are hard to measure. Prioritizing uptime over security is often a rational response by OT staff, not negligence. Improving your cybersecurity assessment process is key.
- Impact: Human error causes nearly 23% of unplanned manufacturing downtime. Attackers often exploit human error and social engineering. Poor password hygiene is pervasive.
- Fix It: Implement ongoing, OT-specific security awareness training. Develop clear OT security policies with OT staff. Foster a strong security culture bridging IT and OT. Building a culture of compliance is vital.

The Staggering Financial Toll of OT Security Failures
The failure to adequately address OT vulnerabilities carries a substantial and escalating financial burden. While the direct costs of cyberattacks are significant, the indirect and long-term consequences can be even more devastating for industrial organizations.
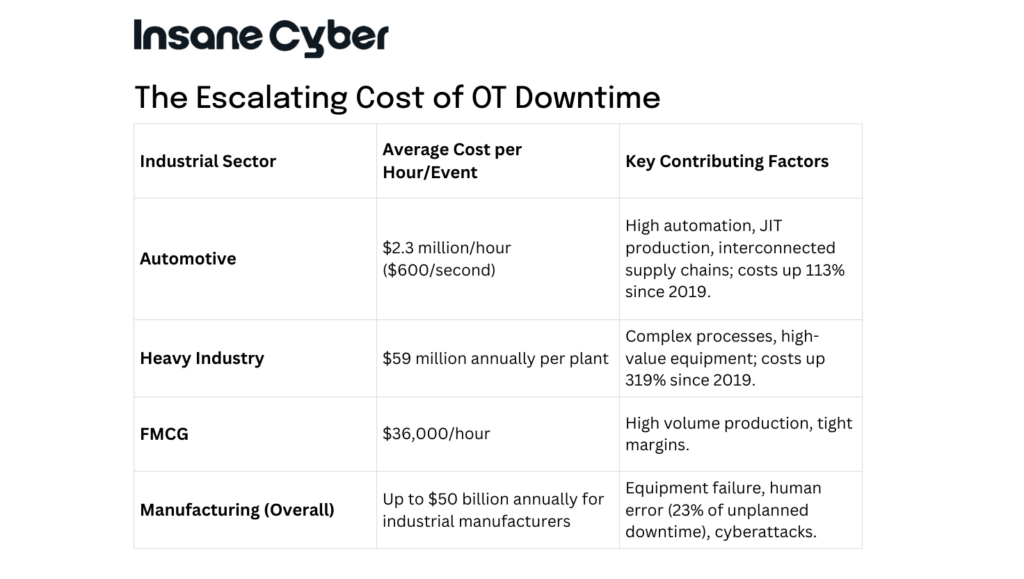
- The average manufacturer contends with approximately 800 hours of equipment downtime each year. Cumulatively, unplanned downtime costs industrial manufacturers as much as $50 billion annually.
- According to the Siemens 2024 Report on the True Cost of Downtime, the world’s 500 largest companies collectively lose an estimated $1.4 trillion per year due to unplanned downtime, which represents a staggering 11% of their annual revenues.
- Human error, often exacerbated by a lack of OT-specific security awareness or risky practices, is a major contributor, accounting for nearly 23% of unplanned downtime incidents in manufacturing.
- Beyond lost revenue, downtime incurs increased operational costs (e.g., overtime pay, expedited shipping), leads to production backlogs and increased lead times, erodes customer satisfaction due to late deliveries, and can trigger safety and compliance risks.
The financial impact of downtime varies significantly by industry, as highlighted by the following statistics:
Fortifying Your Defenses
Addressing these vulnerabilities requires a proactive, OT-centric approach.
- Continuous Monitoring & Assessment: OT security needs constant re-evaluation due to evolving threats and system changes. Continuous monitoring is essential.
- Dynamic OT Asset Inventory: A complete, updated asset inventory is foundational.
- OT-Specific Security Frameworks: Use frameworks like the NIST Cybersecurity Framework (CSF) adapted for OT, NIST SP 800-82, and ISA/IEC 62443. Learn about the differences in OT cybersecurity standards.
- Develop OT-Specific Incident Response (IR) Plans: Plans must account for physical consequences and safe restoration. Test them regularly. If you have no game plan for a cyber incident, this is a critical gap.
Effective OT risk management demands a cultural shift to proactive defense and shared responsibility.
Conclusion: Moving Beyond the Blind Spots
Standard risk assessments often miss OT’s unique vulnerabilities. The five dangers discussed—Shadow OT, insecure HMI access, third-party risks, poor segmentation, and the human element—demand immediate attention. Addressing them requires understanding asset visibility challenges, IT-centric tool limitations, skills gaps, and OT operational pressures.
Organizations must transition to proactive defense, investing in OT-specific technologies and expertise, fostering a security culture, and applying frameworks like NIST CSF and ISA/IEC 62443. Robust OT security is a critical investment in operational resilience, safety, and stability. The systems powering our world are too vital to leave vulnerable. As OT evolves, so must our approach to securing it.




